Cloud Access security broker (CASB) solutions provide an additional protection layer for company employees accessing cloud-based applications.
The software also enforces security policies and acts as a gateway between the employees and cloud services. It allows organizations to extend the on-premise security controls beyond their local network or infrastructure.
In practice, a typical CASB solution is a cloud-based or on-premise software that sits between a cloud application user and the cloud service provider. From here, the solution secures the cloud apps, users, and data by enforcing the business’s security policies.
Today, more and more organizations are relying on cloud-based applications due to the cost savings, convenience, and support for a distributed workforce. Unfortunately, accessing cloud applications comes with a wide range of security risks. Generally, the traditional perimeter security that protects on-premise is not adequate for cloud-based applications, hence the need for additional security, such as the ones cloud access security broker solutions offer.
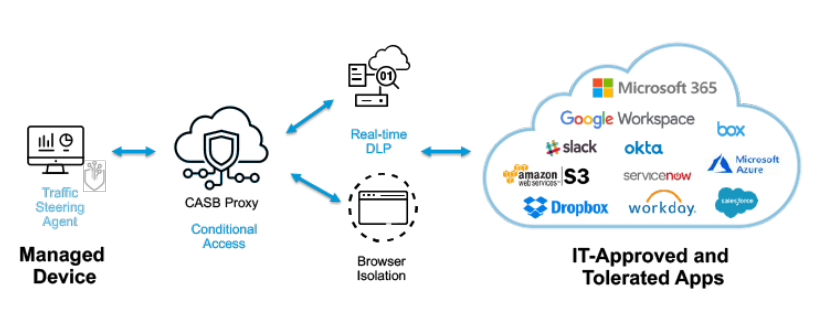
Usually, the CASB solution’s role is to identify security risks and compliance violations whenever users and devices access the cloud apps and data. Besides reducing the security risks, the CASB software will also monitor the systems for any unusual behaviors and activities. Upon detecting any abnormalities, the tools should ideally respond and alert the admins.
How a CASB solution helps organizations improve security
CASB tools enable organizations to
- Improve the security of approved users and cloud applications. It also helps identify unapproved cloud services, unauthorized access, and suspicious activities.
- Monitor and manage the user activities, managed and unmanaged devices, as well as the usage of approved cloud-based applications
- Gain visibility into the organization’s security posture and compliance risks
- Enhance threat detection and response capabilities for the cloud services
- Protect cloud services users, data, and cloud applications.
Key features of a good CASB tool
A typical CASB tool will have four key pillars; visibility, protection against threats, data security, and compliance. While the CASBs may differ in the installation, capabilities, and performance, a good solution should ideally have the following key features.
- Provide visibility into the cloud-based applications and user and device activity.
- Enforce and extend the local security policies to the cloud-based services and provide access controls and encryption.
- Provide an additional layer of protection for the cloud applications, users, and data.
- Empower companies to comply with standard regulations, security, data loss protection, and other policies.
- Provide a secure connection between the employees or end-users and the cloud service company.
Today, there is a wide range of tools with varying capabilities to help you get the best tool for your environment. Here are the best CASB solutions.
Zscaler
Zscaler is one of the best, easy to set up and use CASB solutions that ensure secure access to the cloud applications regardless of a user’s network, location, or device. The solution provides advanced cloud application security and configuration management alongside a central location for enforcing policy and governance.
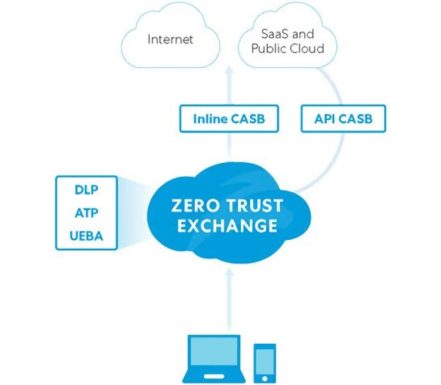
Features
- The consolidated, automated, and scalable web-based solution reduces the complexity and costs of the security system by eliminating the deployment of multiple diverse components.
- Ability to inspect encrypted network traffic at scale hence protecting systems against a wide range of threats and potential data theft or loss. Additionally, it protects the data in transit and at rest.
- It provides an extra layer of protection for the cloud-based applications while enabling better control and granular visibility into the user activity, and data
- Employs advanced data classification technologies that accurately identify specific data, forms, and values that require protection. It also has an optical character recognition to identify data in image files
- reducing the attack surface and ensuring secure access to the cloud apps. The tool monitors and addresses a wide range of vulnerabilities and security risks, compliance issues, and misconfigurations.
- Detecting and protecting data in transit and at rest to ensure security.
Lookout
Lookout Cloud Access Security Broker (formerly Cipherworld) is a powerful, feature-rich CASB solution that enables organizations to protect their cloud applications and users. It provides comprehensive security, compliance enforcement, and end-to-end protection of the data in the cloud environment. With an easy-to-use dashboard, the solution allows administrators to gain enhanced visibility into their cloud applications.
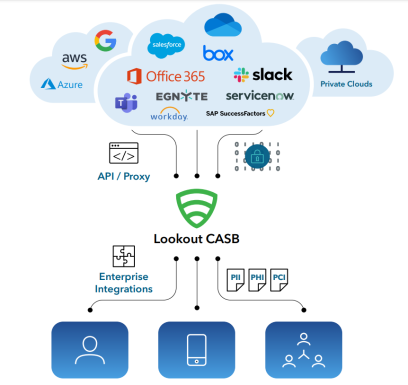
Features
- Provides persistent encryption of the data while only allowing authorized access.
- Monitor user activity, enabling security teams to see the applications in use and ensure compliance.
- Advanced key management that includes rotation, expiry, and other controls that provide maximum security
- Enhanced data loss prevention (DLP) with inbuilt features that help organizations automatically enforce the policies that guarantee the detection of data leaks, potential threats, and other vulnerabilities
- Provides active threat monitoring by observing the users, data, and devices while generating actionable reports.
Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps is a combination of multiple security tools and the ability to support a wide range of deployment modes. Additionally, the CASB solution has other features such as reverse proxy, API connections, and log collection.
The Microsoft CASB comes with advanced analytics capabilities to identify and address a wide range of cyber-attacks across Microsoft and third-party cloud services providers’ platforms. Additionally, it protects data in transit and at rest while providing deep visibility and control.

Features
- Easy to install solution with centralized management that Integrates with major Microsoft deployments and services. Also, it has various automated features hence eliminating manual tasks, associated errors, and inefficiencies.
- Block access and download of sensitive data by unauthorized or vulnerable devices or users
- Enforce real-time session controls hence providing secure collaboration with the company and third-party users
- it has an audit trail feature that allows admins to track user and device activities for forensic investigations
- Protect cloud apps, users, and data by identifying and blocking unusual behavior, rogue applications, ransomware, high-risk usage, and other threats.
- Assess and enforce compliance and other regulatory requirements for your cloud-based services and applications.
Palo Alto
Palo Alto networks CASB is an effective solution that provides a wide range of advanced security features. It includes enhanced threat protection, risk discovery, data governance, user behavior monitoring, etc. Further, it seamlessly integrates with other Alto security solutions such as the access control, firewall, and more to provide comprehensive protection for cloud apps and data.
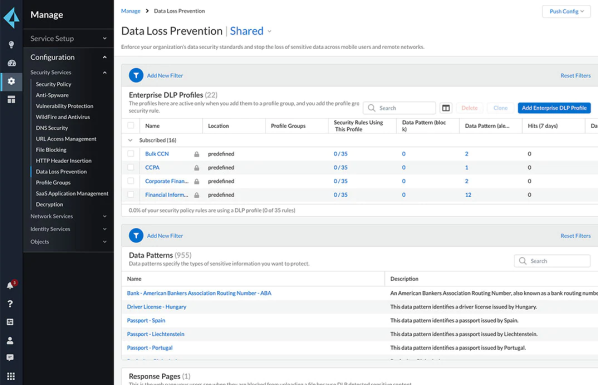
Features
- Advanced-Data loss prevention (DLP) feature that utilizes national language processing, deep learning, OCR, and other intelligent technologies.
- Enhanced visibility and risk discovery feature to identify and manage threats.
- Uses context-aware policies, advanced data prevention, and machine learning technologies to protect the data and prevent leakages.
- Monitor user behaviors to identify, block, and alert on the occurrence of any unusual activities such as multiple failed login attempts, logins from different or unexpected locations, abnormally high usage activity, etc.
- Enforce data governance and compliance policies by detecting and addressing risk violations to regulations such as PCI, PHI, GDPR, and others.
Cisco Cloudlock
Cisco Clocudlock is a simple and automated, cloud-native CASB that allows organizations to protect their cloud apps, data, and users. The comprehensive solution provides deeper visibility into the cloud applications and Shadow IT, enabling security teams to better understand and protect their environments.

Features
- Automates policy-based control of cloud apps, such as revoking applications with high-risk scores and those that exceed set permission levels.
- Uses machine learning, user analytics, and other intelligent technologies to detect and prevent unusual behaviors, malicious insider threats, compromised accounts, unauthorized access, unintentional exposure, and policy violations
- Minimize shadow IT risk by providing automated, policy-based shadow IT enforcement capabilities to block risky activities and applications based on the configured risk level and permissions.
- Uses customizable policies to detect and prevent data loss or theft. This enables the teams to properly secure sensitive data in transit and at rest.
- A fully API-based CASB solution that is easy to deploy and use, enabling teams to quickly secure access and protect the cloud apps, users, and data.
Netskope Security Cloud Platform
Netskope Security Cloud Platform provides enhanced visibility and comprehensive security for users accessing cloud-based applications regardless of their location and devices. The platform protects users and applications against a wide range of threats, malware, and data breaches. The tools support major cloud services, including Microsoft Office 365, AWS, Google G Suite, Box, etc.

Features
- Set granular security policies and controls, gain enhanced visibility that enables you to identify and prevent risks of data loss from external criminals and internal users
- Enables security teams to quickly identify and monitor their organization’s managed and unmanaged cloud applications. The tool allows businesses to continuously monitor their environment for security issues and ensure compliance.
- Protect sensitive data from access or download by unauthorized users such as cybercriminals, collaborators, malicious internal staff, etc. Additionally, it helps you prevent data leakage, including the ability to differentiate between personal and corporate accounts. It also monitors the cloud-based platform in real-time and prevents unauthorized data access, upload, or download before it happens.
- Detect and address misconfigurations in your cloud-based applications and security systems.
- Enforce an effective security posture for your SaaS platform.
Proofpoint
Proofpoint is a cloud-based CASB solution that helps organizations securely access, manage and control their cloud apps and data. The Cloud Access Security Broker solution comes with advanced threat detection and protection capabilities. Its agentless architecture allows organizations to easily and quickly deploy the security solution.
Features
- Provides valuable insights into the cloud services usage at the user, application, and global level
- Advanced DLP options with built-in dictionaries, rules, smart identifiers, templates, and more. Additionally, it has effective and accurate out of box DLP policies that shorten the time to deploy, identify and respond to cloud data compromise threats.
- Prevents account compromise, malicious files, non-compliance, and data oversharing risks
- Monitoring user behavior for unusual activities, suspicious logins, and data compromise threats. The tool provides automated detection and response of unusual activities at and after account compromise.
- Enables teams to deploy consistent data loss protection policies across the on-premise and cloud-based applications and services.
Trend Micro
Trend Micro Cloud App Security is one of the most effective solutions for securing systems and data against various threats, including advanced and complex attacks. It also secures cloud-based applications such as email, G Suite, MS Office 365, collaboration, cloud file-sharing services, etc.

Features
- Enforcing compliance across various cloud-based file-sharing services, including but not limited to Google Drive, Dropbox, OneDrive, Box, and other online systems.
- Advanced controls to protect various online systems against malicious activities, ransomware, malware, email compromise, and other threats.
- Relies on machine learning, sandboxing analysis, and other advanced technologies to detect, identify and respond to a wide range of threats.
- Besides protection against threats, Trend Micro helps organizations set and enforce Data Loss Protection policies and compliance with cloud file-sharing services. It also scans all files, including those from remote workers and devices, before uploading them to the cloud.
- Integrates seamlessly with Apex One endpoint protection and other Trend Micro security solutions.
Conclusion
CASB solutions extend or enforce the organization’s on-premise security systems and policies beyond the local infrastructure and up to the cloud services. The security software or platform usually sits between the users and the cloud services or applications, where they monitor the activities while blocking unauthorized or unusual actions such as unauthorized access, downloads, malware, and other cyber threats.
Additionally, CASB solutions help to enforce a wide range of security policies, ensuring comprehensive protection of the cloud apps, users, and data.



