Penetration testing has become an essential part of any modern strategy to protect web applications. Pen-testing solutions are preferable to free or open-source ones to prevent attacks on critical APIs and web apps.
The nature of cyberattacks is constantly evolving. For this reason, companies, government agencies, and other organizations are implementing increasingly sophisticated cybersecurity techniques to protect their web applications from cyber threats. Among these techniques is penetration testing, which, given its growing popularity, is on track to become a $4.5 billion market by 2025 as predicted by the consulting firm Markets and Markets.
What are penetration tests?
Penetration tests are simulations of cyberattacks against a computer system, a network, a site, or an application. Typically, pen-tests are carried out by trained security testers who try to breach an organization’s security systems to identify their weaknesses, although there are also automated tests that reduce testing times and costs.
The objective of these tests – whether automated or manual – is to detect vulnerabilities that cybercriminals could exploit to perpetrate their crimes to eliminate them before an attack occurs.
Pen-testing offers several important benefits that make it so popular. But they also have a few downsides.
Benefits and Disadvantages of Penetration Testing
The main benefit of penetration tests is identifying vulnerabilities and the information about them to eliminate them. In addition, the results of pen-tests allow increasing the knowledge of the digital assets (mainly web applications) that are sought to be protected. As a positive side effect, increased application awareness and protection help improve your customers’ trust.
Pen-testing practice also has its downsides. One of the most relevant is that the cost of making a mistake when doing such tests can be very high. The tests can also have negative ethical implications since the activity of criminals who lack all ethics is being simulated.

Many free and open-source security tools are suitable for small or starter sites. When doing manual penetration testing, the cost depends on the skills of the testers. To put it short, manual testing should be expensive to be good. If penetration testing is run as part of a software development process, running it manually slows the development cycle.
To avoid risks in business web applications, premium penetration testing solutions are preferable, as they offer additional benefits, such as detailed reports, specialized support, and recommendations for troubleshooting.
Read on to learn about the top premium penetration testing solutions for your critical web applications.
Netsparker
Penetration testing solutions such as the Netsparker Vulnerability Scanner empower companies to scan thousands of web applications and APIs for vulnerabilities in a matter of hours. They can also be embedded within a software development life cycle (SDLC) to periodically scan web applications for vulnerabilities that may appear with each code change. This prevents security breaches from making their way into live environments.
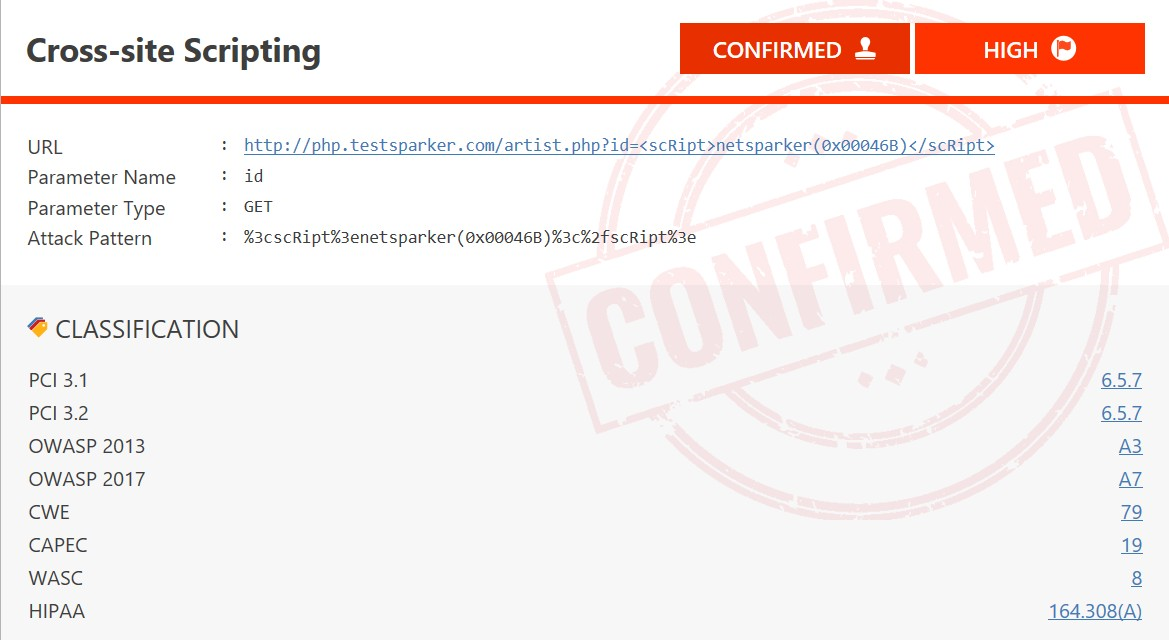
An important aspect of penetration testing tools is coverage, which means that the tool must cover all possible alternatives of a web application or a web API. If there is a vulnerable parameter in an API or an application, and that parameter is not tested, the vulnerability will not be detected. Netsparker’s web application security scanner excels at offering the widest coverage possible so that no vulnerabilities go unnoticed.
Netsparker uses a Chrome-based crawling engine that can interpret and crawl any web application, regardless of whether it is legacy or next-generation, as long as it is available through the HTTP and HTTPS protocols. Netsparker’s crawling engine supports JavaScript and can crawl HTML 5, Web 2.0, Java, Single Page Applications, as well as any application that uses JavaScript frameworks such as AngularJS or React.
Intruder
Intruder is an automated vulnerability scanner capable of finding cybersecurity weaknesses in an organization’s digital infrastructure, avoiding costly data loss or exposure.
Intruder integrates seamlessly into your technical environment to test your systems’ security from the same perspective (the internet) that potential cyber criminals trying to compromise see it. To do this, it uses penetration software that stands out for being simple and fast so that you can be protected in the shortest possible time.
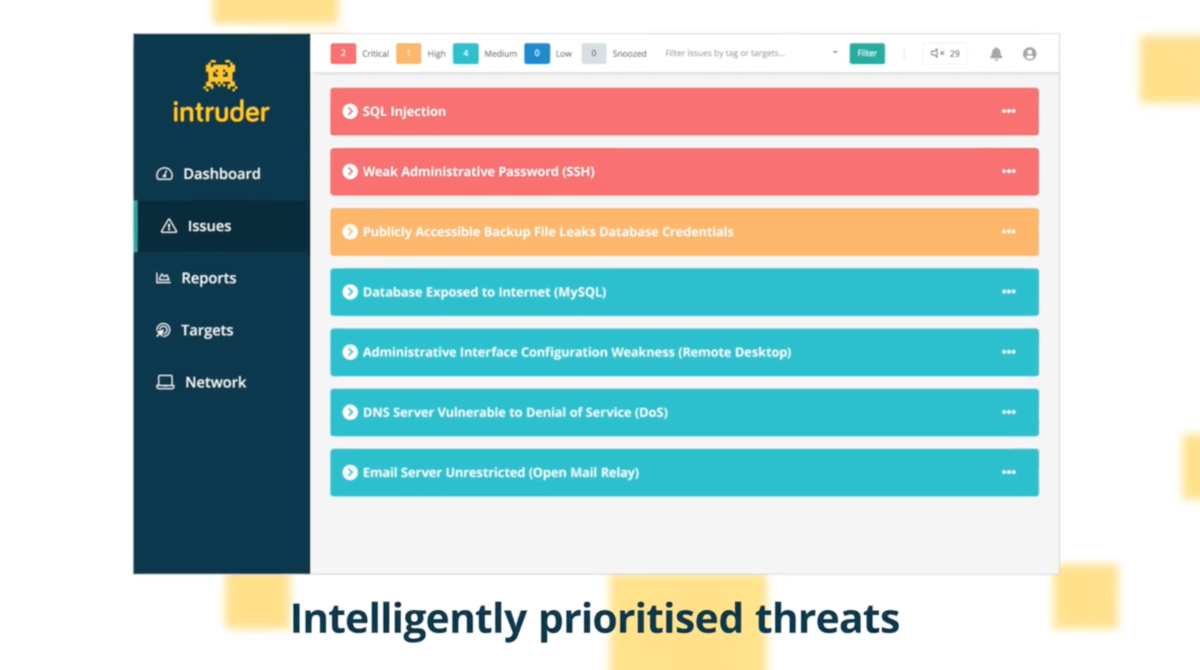
Intruder includes a feature called Emerging Threat Scans, which proactively checks your systems for new vulnerabilities as soon as they are disclosed. This functionality is just as useful for small businesses as it is for large ones, as it reduces the manual effort required to stay on top of the latest threats.
As part of its commitment to simplicity, Intruder uses a proprietary noise reduction algorithm that separates what is merely informational from what requires action, so you can stay focused on what really matters to your business. The detection carried out by Intruder includes:
- Web layer security issues, such as SQL injection and cross-site scripting (XSS).
- Infrastructure weaknesses, such as the possibility of remote code execution.
- Other security configuration errors, such as weak encryption and unnecessarily exposed services.
A list of all the 10,000 checks that Intruder carries out can be found on its web portal.
Probely
Many growing companies do not have their own cybersecurity staff, so they rely on their development or DevOps teams to conduct security testing. The standard edition of Probely is specially designed to facilitate penetration testing tasks in this type of company.
The entire experience of Probely is designed for the needs of growing companies. The product is elegant and easy to use, allowing you to start scanning your infrastructure in no more than 5 minutes. Problems found during the scan are displayed, along with detailed instructions on how to correct them.
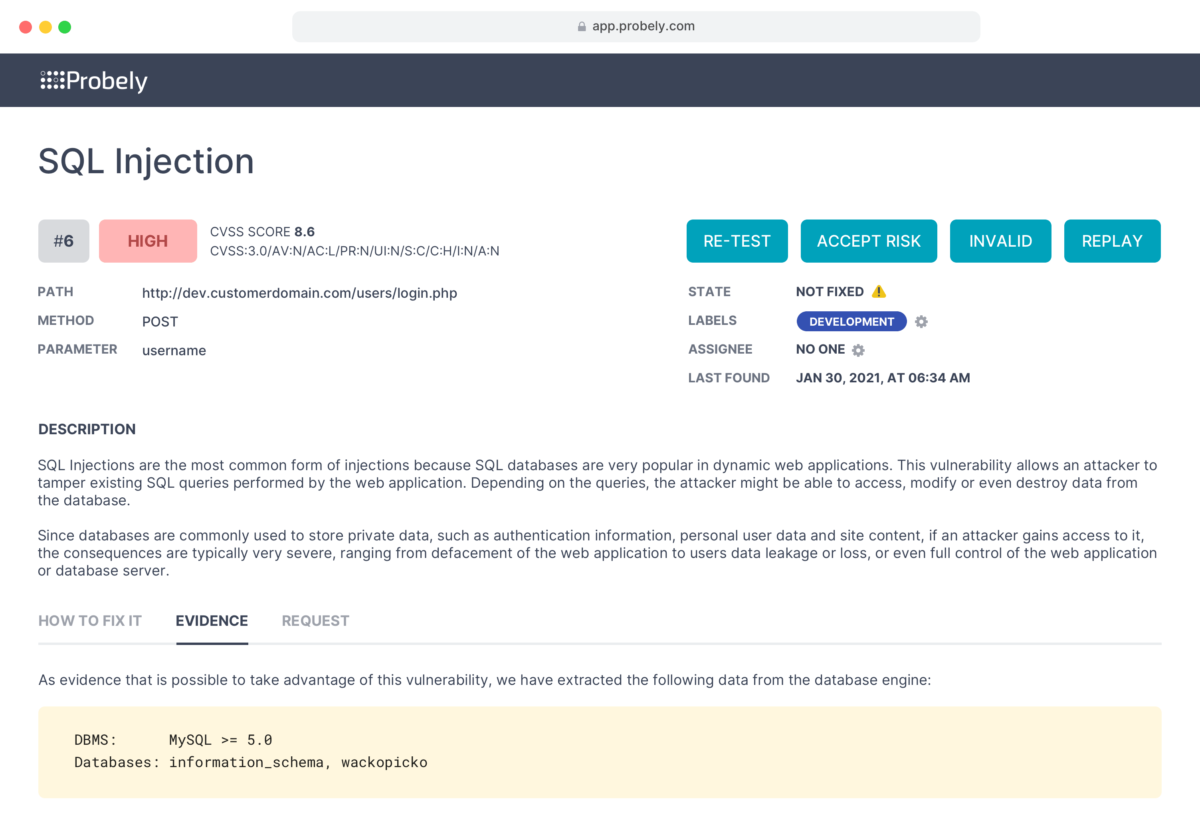
With Probely, security testing carried out by DevOps or development teams becomes more independent from specific security personnel. In addition, the tests can be integrated into the SDLC to automate them and become part of the software production pipeline.
Probely integrates through add-ons with the most popular tools for team development, such as Jenkins, Jira, Azure DevOps, and CircleCI. For tools that do not have a supportive add-on, Probely can be integrated through its API, which offers the same functionality as the web app, since each new feature is added first to the API and then to the UI.
Burp Suite
The Burp Suite Professional toolkit stands out for automating repetitive testing tasks and then deep analysis with its manual or semi-automatic security testing tools. The tools are designed to test the Top 10 OWASP vulnerabilities, along with the latest hacking techniques.
Burp Suite’s manual penetration testing functions intercept everything your browser sees, with a powerful proxy that allows you to modify the HTTP/S communications that pass through the browser. Individual WebSocket messages can be modified and reissued for later analysis of responses – all done within the same window. As a result of the tests, all hidden attack surfaces get exposed, thanks to an advanced automatic discovery function for invisible content.
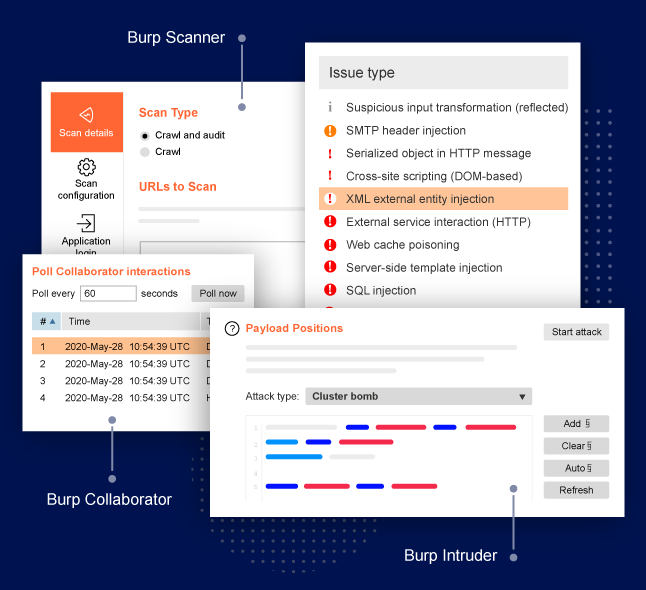
Recon data is grouped and stored in an objective site map, with filtering and annotation features that complement the information provided by the tool. Documentation and remediation processes are simplified by generating clear reports for end-users.
In parallel to the user interface, Burp Suite Professional offers a powerful API that grants access to its internal functionality. With it, a development team can create their own extensions to integrate penetration testing into their processes.
Detectify
Detectify offers a fully automated penetration testing tool that allows companies to be aware of the threats against their digital assets. Penetration testing is part of a suite of digital asset inventory and monitoring tools that include vulnerability scanning, host discovery, and software fingerprints. The complete package helps avoid unpleasant surprises, such as unknown hosts presenting vulnerabilities or subdomains that can be easily hijacked.
The Detectify penetration tests were developed in collaboration with the Ethical Hacking community to turn the latest security findings into vulnerability tests. Thanks to this, Detectify’s automated penetration testing provides access to exclusive security findings and testing of 2000 vulnerabilities in web applications, including OWASP top 10.
If you want to be covered against new vulnerabilities that appear practically every day, you’ll need more than running quarterly penetration tests. Detectify offers its Deep Scan service, which provides an unlimited number of scans, along with a knowledge base with 100 remediation tips. It also offers integration with collaboration tools like Slack, Splunk, PagerDuty, and Jira.
Detectify offers a free 14-day trial that does not require entering credit card details or other means of payment. During the trial period, you can do all the scans you want.
Nessus
Nessus performs point-in-time penetration testing to help security professionals quickly and easily identify and fix vulnerabilities. Nessus’ solution can detect software failures, missing patches, malware, and incorrect configurations on a variety of operating systems, devices, and applications.
Nessus allows you to run credential-based scans on different servers. In addition, its preconfigured templates allow it to work over multiple network devices, such as firewalls and switches.
One of the main goals of Nessus is to make penetration testing and vulnerability assessment simple and intuitive. It does this by offering customizable reports, predefined policies and templates, real-time updates, and unique functionality to silence certain vulnerabilities so that they do not appear for a specified time in the default view of scan results. Users of the tool highlight the possibility of customizing the reports and editing elements such as logos and severity levels.
The tool offers unlimited growth possibilities thanks to a plugin architecture. The vendor’s own researchers continually add plugins to the ecosystem to incorporate support for new interfaces or new kinds of threats that get discovered.
AppCheck
AppCheck is a complete security scanning platform built by penetration testing experts. It is designed to automate the discovery of security problems in apps, websites, cloud infrastructures, and networks.
AppCheck penetration testing solution integrates with development tools such as TeamCity and Jira to conduct assessments through all the stages of an application life cycle. A JSON API allows it to integrate with development tools not natively integrated.
With AppCheck, you can launch scans in a matter of seconds, thanks to prebuilt scan profiles developed by AppCheck’s own security experts. You don’t have to download or install any software to begin scanning. Once its work is done, findings are reported with extensive detail, including easy-to-understand narratives and remediation advice.
A granular scheduling system lets you forget about launching scans. Using this system, you can configure allowed scan windows, together with automatic pauses and resumes. You can also configure automatic scan repetitions to be sure that no new vulnerability will go unnoticed.
A configurable dashboard gives a full and clear view of your security posture. This dashboard allows you to spot vulnerability trends, track remediation progress, and get a glance at the areas of your environment that are most at risk.
AppCheck licenses impose no limitations, offering unlimited users and unlimited scanning.
Qualys
Qualys Web Application Scanning (WAS) is a penetration testing solution that discovers and catalogs all web applications on a network, scaling from a few to thousands of applications. Qualys WAS allows web applications to be tagged and then used in control reports and to limit access to scan data.
WAS’s Dynamic Deep Scan feature covers all applications in a perimeter, including apps in active development, IoT services, and APIs that support mobile devices. Its scope covers public cloud instances with progressive, complex, and authenticated scans, providing instant visibility into vulnerabilities such as SQL injection, cross-site scripting (XSS), and all of OWASP Top 10. To carry out penetration testing, WAS employs advanced scripting with Selenium, the open-source browser automation system.
To perform scans more efficiently, Qualys WAS can operate across a pool of multiple computers, applying automatic load balancing. Its scheduling functions allow you to set the exact start time of the scans and their duration.
Thanks to its malware detection module with behavior analysis, Qualys WAS can identify and report existing malware in your applications and websites. The vulnerability information generated by automated scans can be consolidated with information collected from manual penetration tests so that you have a complete picture of your web application’s security posture.
Ready to go premium?
As your web application infrastructure grows in surface area and criticality, open-source or free-to-use penetration testing solutions begin to show weaknesses. This is when you should consider a premium penetration testing solution. All the options presented here offer different plans for different needs, so you should evaluate the most suitable for you to start testing your applications and anticipate the action of malicious attackers.



