
As a system administrator or Cloud administrator, it might be quite challenging to figure out how secure your environment is. This is usually due to the vast number of systems your business has put in place and the complex networking involved.
Infection Monkey is an open source tool that might make your work easier and be able to answer questions such as ‘How secure is your cloud?’. With Infection Monkey, you can simulate a number of security attacks to your cloud environment such as Credential theft, network attacks and many other simulations on a web interface.
You will also get a detailed report about the scans and the vulnerabilities discovered, and of course a recommendation of what needs to be done to secure your environment.
All you need is to install Infection Monkey on a Debian host, access it on web UI, configure the kind of attacks you want to simulate then let the Monkeys do their thing as you sip a cup of coffee.
In this tutorial we shall install Infection Monkey on Ubuntu 18.04. Follow the steps below:
Download and install Infection Monkey on Ubuntu
- Register on Infection Monkey download page to get the .deb file.
- Download the .deb file on to your server from the link that will be shared to your email.
- Make sure your Ubuntu system is updated.
$ sudo apt update && sudo apt upgrade -y- Install the .deb file using the
apt installto install all the dependencies needed to run the system
$ sudo apt install ./monkey-island-debian.debThis installs Infection Monkey on Ubuntu including the needed dependencies.
Upon successful install, you will get a notification that the server can be accessed via https://:5000/
$ sudo apt install ./monkey-island-debian.deb
....
Generating csr in /var/monkey/monkey_island/cc/server.csr...
Generating certificate in /var/monkey/monkey_island/cc/server.crt...
Signature ok
subject=C = GB, ST = London, L = London, O = Global Security, OU = Monkey Department, CN = monkey.com
Getting Private key
2 0 records in
2 0 records out
2048 bytes (2.0 kB, 2.0 KiB) copied, 0.000205939 s, 9.9 MB/s
Starting services...
Monkey Island installation ended.
The server should be accessible soon via https://:5000/
To check the Island's status, run 'sudo service monkey-island status'- Allow port 5000 through the firewall
sudo ufw allow 5000/tcp- You can now access the server via https://:5000
You will be required to create a username and a password upon first-time access.
You then need to configure your simulation by selecting ‘Configure Monkey‘ option.
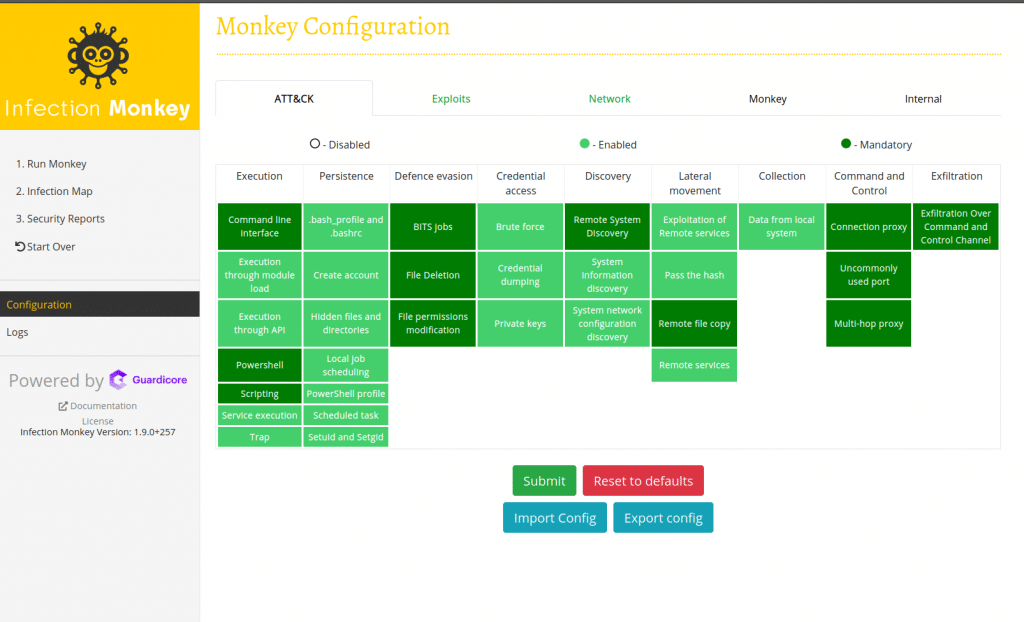
Select the types of simulation you want to run and Submit
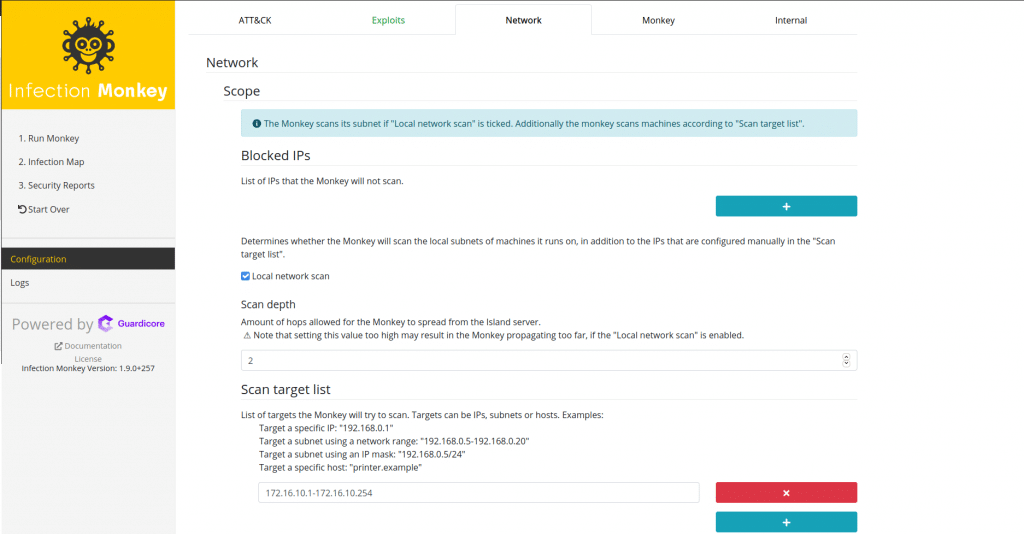
You can also configure network options in the network tab such as the range to scan or an entire subnet. You can also configure subnets that are supposedly segmented, with this option, Infection Monkey will try to see if devices in the segmented subnets can communicate.
Now go to the left pane and click Run Monkey. This is where the fun begins. There are two options in this tab.
- Run on Monkey Island Server – This starts the monkey on the server and all exploits are centered on the Monkey server.
- Run on a machine of your choice – This allows you to run a script on the client servers that sends reports to the Monkey server.
You can also choose to run both, where the tests are done both on the Monkey server and the client servers.
When you choose the ‘Run on a machine of your choice‘ you will be required to choose the type of client machine that you will run the script on and the network interface of the Monkey server that the client machine that the clients will use to connect/send stats and reports.
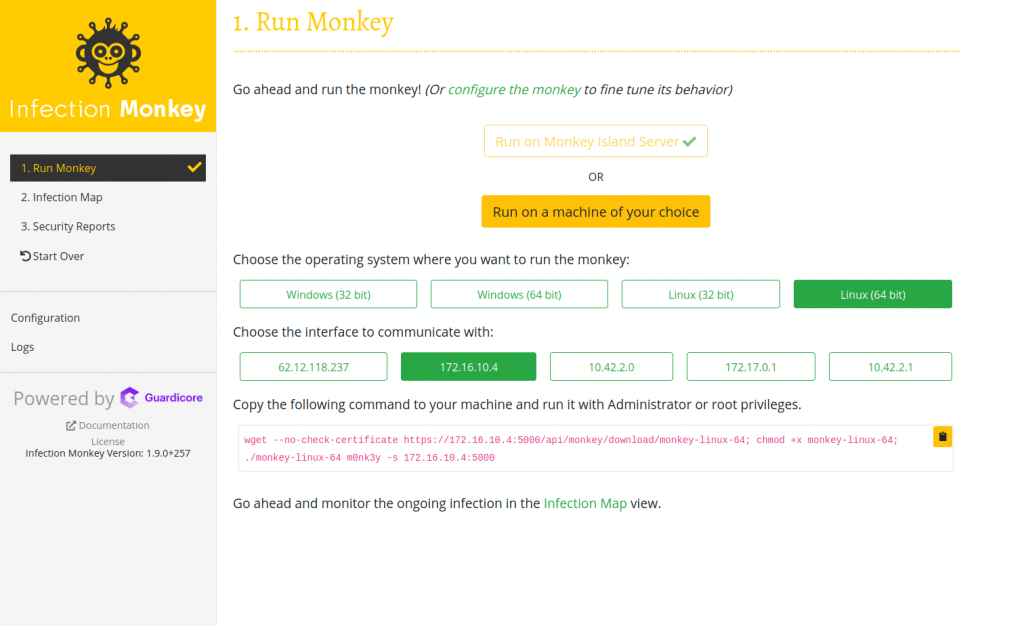
Copy the script provided and run it on the client machines’ terminals.
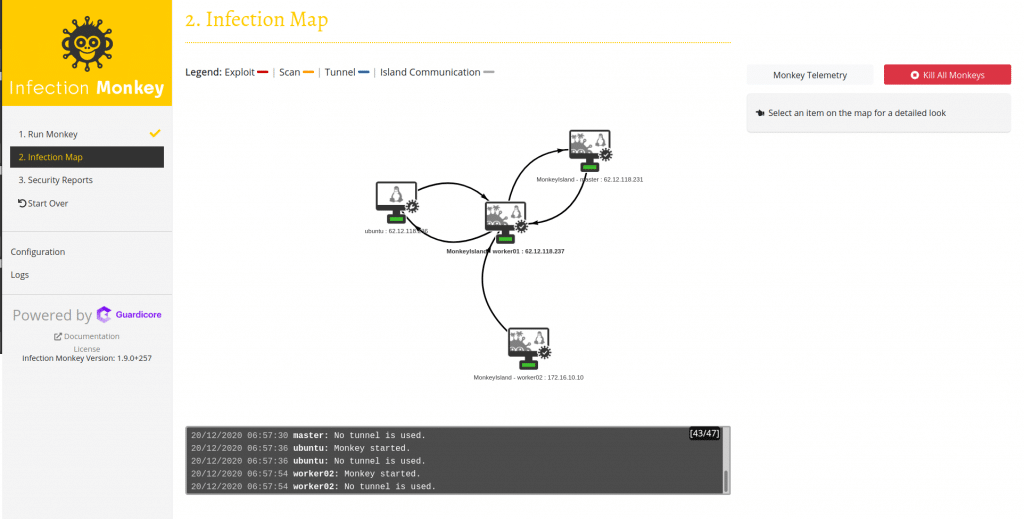
You can now go to the Infection Map tab to see the progress of the simulation. At first, you will only see the connections to the hosts that have the script running, but as the tests continue, you will be able to see more hosts within the network connected to the simulation.
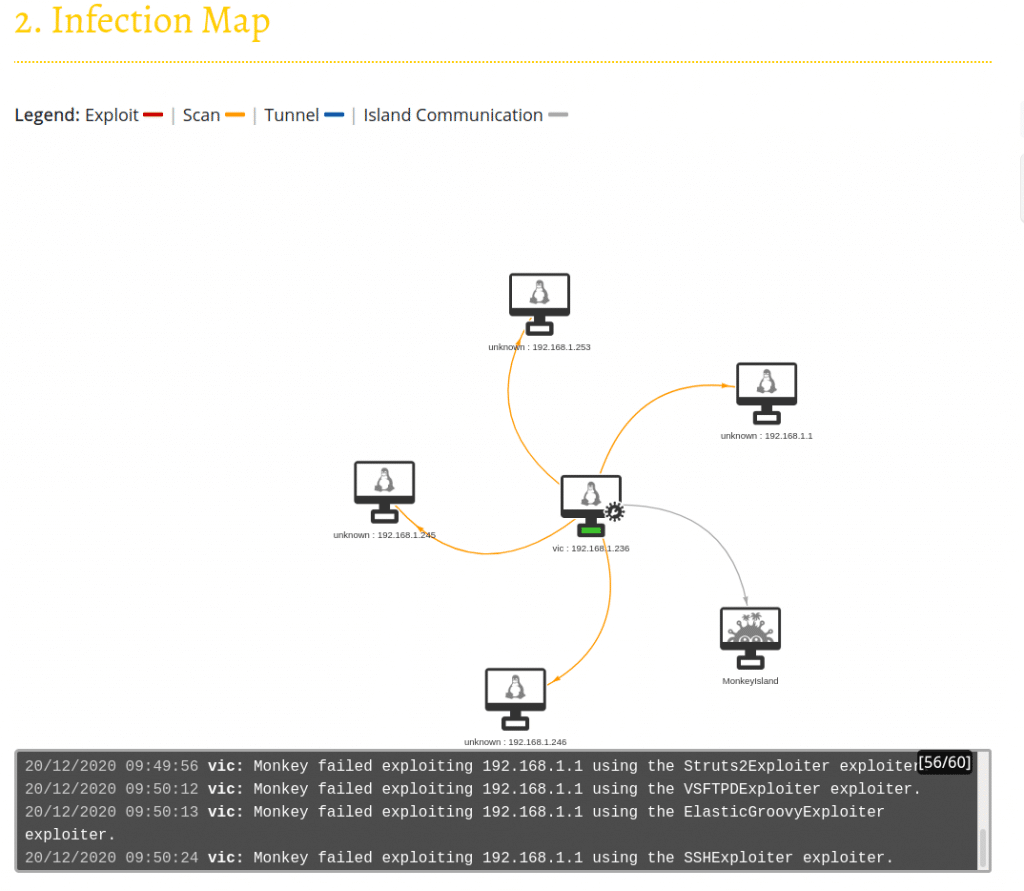
In a small network, the scan takes less time and you will see few devices on the scan:
You will have to wait longer (minutes or hours) if your network is vast and you will get a broader view of the scan as below:
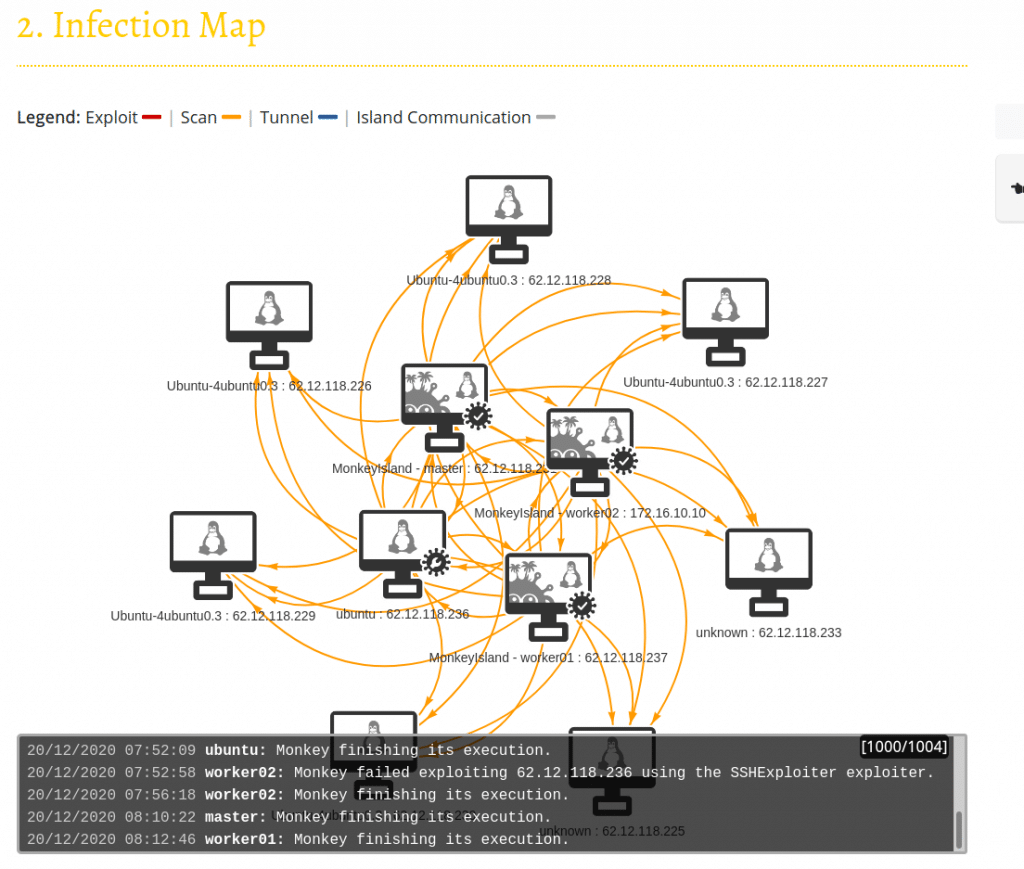
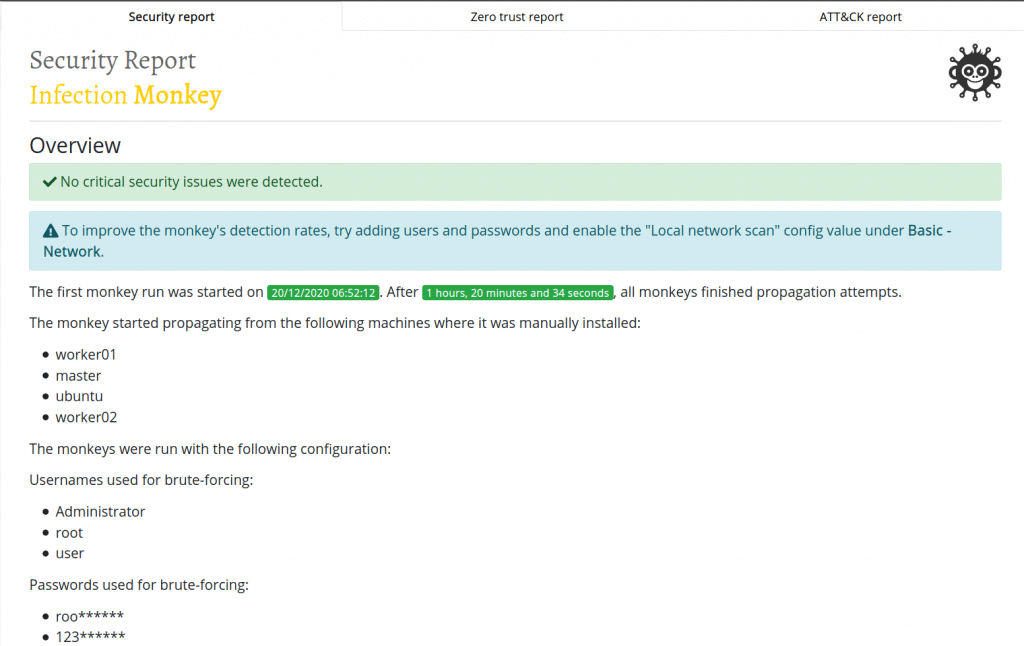
When the scan is done on all devices, you will be able to obtain the reports at the Security Reports tab.
You can check the number of devices found on the scan and if there was any vulnerability found.
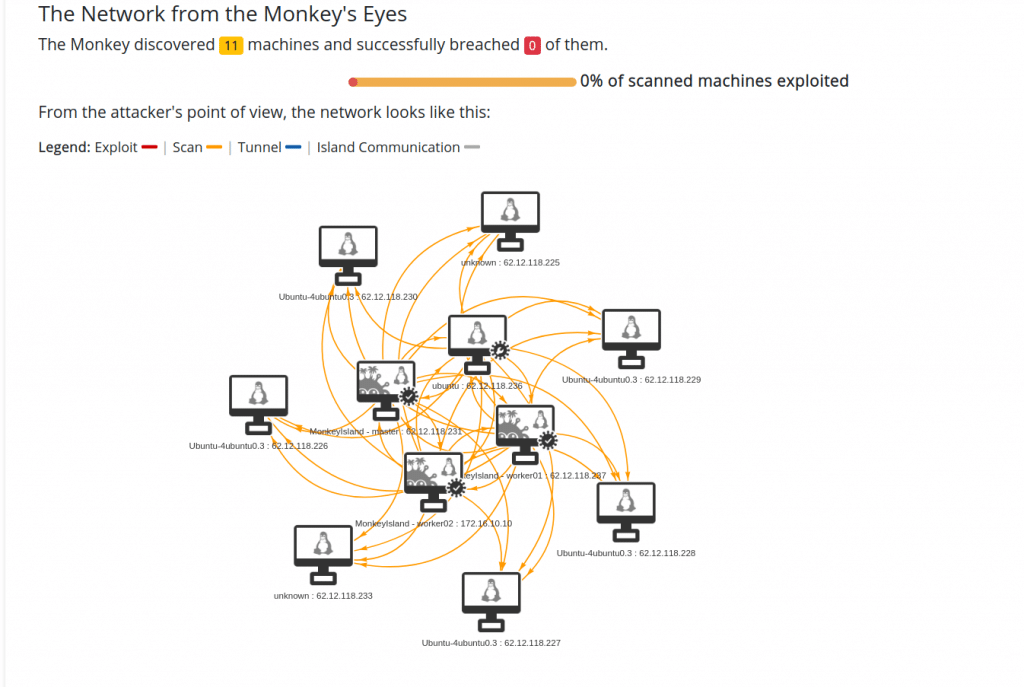
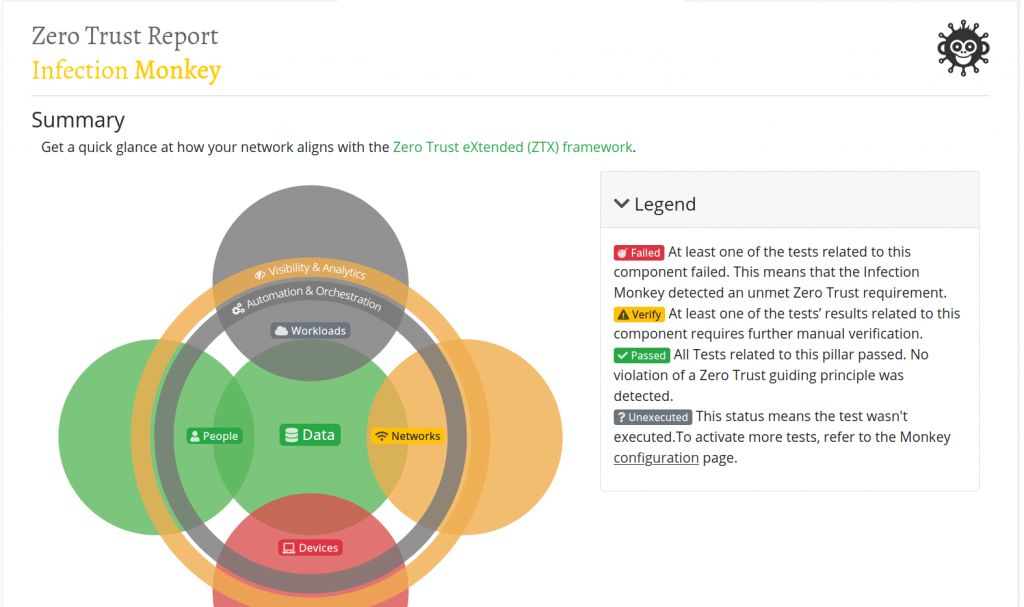
You can navigate further to Zero trust reports to get more reports about the scan.
Wrap Up
As we have seen, Infection Monkey is evidently a handy tool to system/cloud administrators to get held of your environment’s security status with less effort.
Check out these interesting tools on our site:
Forward Server logs and metrics to Elasticsearch using Beats
Faraday – Penetration Testing IDE & Vulnerability Management Platform



