You’ve come to the right place if you want to learn how to detect rootkits on different operating systems and the ways to prevent them.
A rootkit is a sort of covert and deadly malware that hackers employ to take complete control of a computer or network. Using Rootkits, the attacker can easily manipulate and steal the data from the system.
Rootkits may appear as a single piece of software, but they’re usually a set of tools that provide attackers unauthorized administrative access to the target system while actively concealing its presence.
Once a rootkit has been placed in the system somehow, the attacker will have the ability to execute remote files and change the host machine’s system configuration. The easiest way to identify rootkit infection in a system or server is to run a rootkit scan.
Let’s get started.
How to detect Rootkits in a system?
It’s not easy to detect a rootkit manually on a computer or a server. Rootkits always stay in disguise in the form of another application or a file. So it’s challenging to detect their presence. However, there are some command-line tools, software, and methods to detect the rootkits in various operating systems automatically.
Windows
For windows, there are no command-line tools to detect rootkits. However, a powerful and exhaustive scanner application called GMER detects and even removes the rootkit very effectively on the windows system.
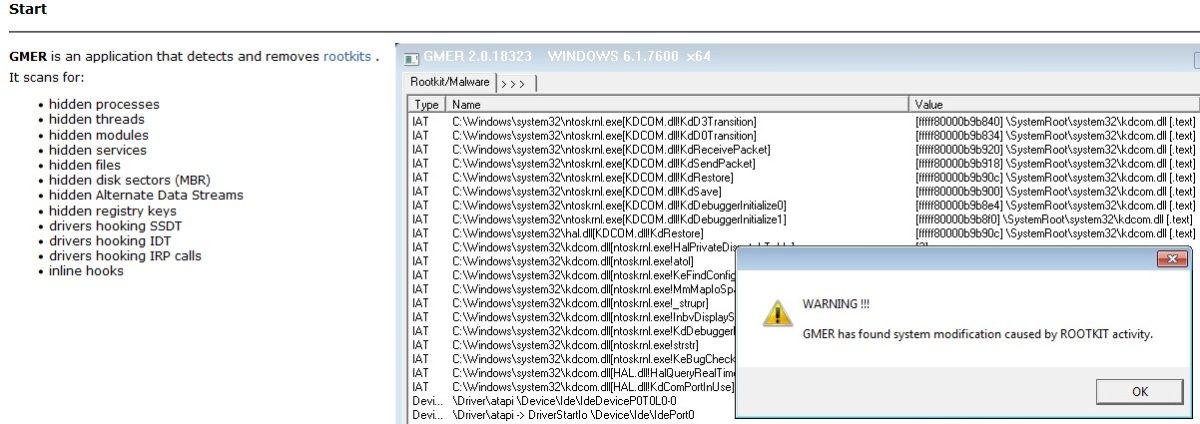
This tool searches the whole system for hidden threads, registry keys, and other hidden processes. Performs all types of analysis like behavior, signature, and integrity checking to detect and remove the rootkit.
This application is beneficial to detect all types of rootkit such as kernel mode, application, memory, and bootloader rootkits. It works on all major Windows OS.
Linux and Mac OS
In all Linux distributions and Mac OS, you can easily detect rootkits using chkrootkit and rkhunter command-line tools.
Using chkrootkit
chkrootkit searches deeply for trojans, malware, and other types of malicious codes in the machine’s binary system. It looks for the changes rootkit makes in system executable binaries. chkrootkit is not pre-installed in Linux distribution.
This tool is simple to use and can be installed with the following command:
sudo apt-get install chkrootkitor you can also install it by cloning the Git repository.
git clone https://github.com/Magentron/chkrootkit.gitNext, navigate to that directory and run the chkrootkit.
./chkrootkitThis command starts the hunt for rootkits in the system. You can use the help command for more instructions on this tool usage.
┌──(root💀kali)-[/home/geekflare/chkrootkit]
└─# ./chkrootkit -help
Usage: ./chkrootkit [options] [test ...]
Options:
-h show this help and exit
-V show version information and exit
-l show available tests and exit
-d debug
-q quiet mode
-x expert mode
-r dir use dir as the root directory
-p dir1:dir2:dirN path for the external commands used by chkrootkit
-n skip NFS mounted dirsThis tool mainly works on signature analysis and integrity checking to hunt down the rootkit in the system or a server.
Using rkhunter
Alternately, there is another command-line tool to find rootkits in Linux distributions. That is rkhunter. This tool can also detect remote exploits and backdoors in the system. Just install this tool using the following command.
$ sudo apt-get install rkhunterThe next step is to run the rkhunter for detecting the backdoors and rootkits.
$ rkhunter -cIt performs the search, and the status will be given by default. If there are any problems, it’ll indicate them in red.
This is a perfect tool for forensic analysis because it performs additional network tests, kernel module checks, and other tests that chrootkit does not.
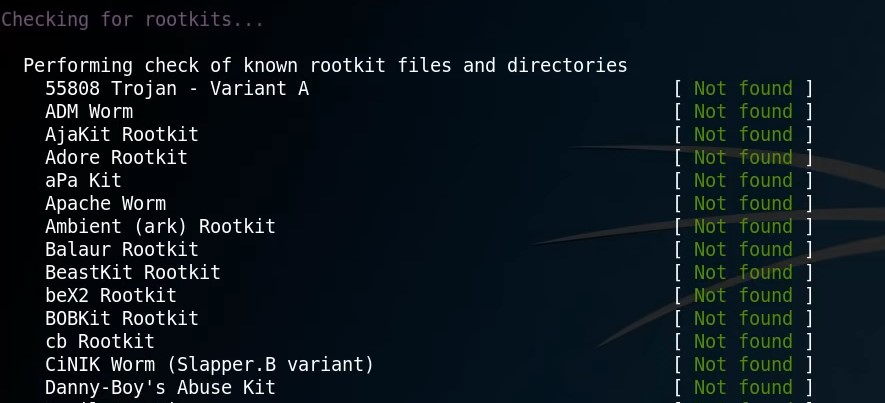
This tool works on behavior analysis, signature analysis and takes a condition of booting on different mediums to detect the rootkit.
Always make sure you update the chkrootkit and rkhunter tools database before performing scanning. Only then you will be able to detect the latest rootkits that are currently out. For that, make sure your Linux system is up to date with the newest patches using the below command.
$ sudo apt update && sudo apt upgradeRootkits Removal Tools
The rootkit removal applications and tools listed below are simple to use and effective. These tools can automatically detect and remove rootkits from the system.
#1. Avast Rootkit Scanner tool is powerful for detecting and removing rootkits from the system signature scanning. Memory dump analysis and system memory search are some of the features. This program also keeps track of all DLL (Dynamic-Link Libraries) library calls that are imported.
It has a comprehensive reporting system that allows you to view current and prior scan results and email alert reports after each scan.
Not just a computer, but you can also remove the rootkit from Android or iOS mobile using Avast.
#2. Malware Bytes prevents rootkit, adware, spyware, and other threats from infecting your computer. This program examines the integrity of the kernel memory and alerts the user to any potential issues. It allows you to scan your system for rootkits with just a single click. This, too, will keep you safe online while keeping your computer working smoothly.
#3. Lynis is an excellent security auditing tool for Linux & BSD systems. It audits several elements of your system’s security and configurations in great detail. Lynis can detect security problems, such as rootkits and backdoors, as well as configuration flaws.
Instead of simply identifying the flaws, it also provides solutions like which file to remove and what to do to evade reinfection.
#4. Malware fox uses its cloud-based rootkit library; it checks the system for all types of rootkits. Advanced rootkits, such as keyloggers, can also be detected. It can detect and remove all kinds of rootkits and close any backdoors that hackers may be utilizing to get access to your computer. Its database is also updated regularly to ensure optimal security.
#5. Sophos is a handy tool that detects and removes rootkits quickly. This tool mainly uses behavior analysis ( examines the behavior of every file and application ), and if any file or program does act similarly to rootkits, they will be removed immediately. It even protects registry keys and file locations from reinfection again.
Conclusion
Install sophisticated and powerful anti-malware software on your computer and be attentive all the time while opening attachments and unknown emails. Download the files and programs only from reliable sources. The greatest protection against rootkit is to set up an automatic and encrypted backup process to cloud storage.
If a rootkit has infected your system very profoundly, the only way to remove it is to reinstall the operating system.
You may also be interested in learning about tools to scan Linux servers for malware and security flaws.