☁️ Cloud infrastructure has benefits such as flexibility, scalability, high performance, and affordability. Once you subscribe to a service, such as the Google Cloud Platform (GCP), you do not have to worry about the high capital and maintenance costs of an equivalent in-house data center and associated infrastructure. However, traditional on-premise security practices do not provide sufficient and prompt security for virtual environments.
Unlike an on-premise data center where perimeter security protects the entire installation and resources, the nature of the cloud environment, with diverse technologies and locations, requires a different approach. Usually, the decentralized and dynamic nature of the cloud environment leads to an increased attack surface.
In particular, misconfigurations on the cloud platforms and components expose the assets while increasing the hidden security risks. Sometimes, developers may open a data store when developing a piece of software but then leave it open when releasing the application to the market.
As such, in addition to following security best practices, there is a need to ensure proper configurations as well as the ability to provide continuous monitoring, visibility, and compliance.
Luckily, there are several tools to help you improve security by detecting and preventing misconfigurations, providing visibility into the security posture of the GCP as well as identifying and addressing other vulnerabilities.
Update: for the AWS security scanner, check out this post.
Google Cloud SCC
The Google Cloud SCC is an integrated risk analysis and dashboard system that enables GCP customers to understand their security posture and take remedial actions to protect their cloud resources and assets from a single-pane-of-glass.
Cloud SCC (Security Command Center) provides visibility into what assets are running on the Google cloud environment as well as risky misconfigurations, hence enabling teams to reduce their exposure to threats. Also, the comprehensive security and data risk management tool help the GCP clients to enforce security best practices.
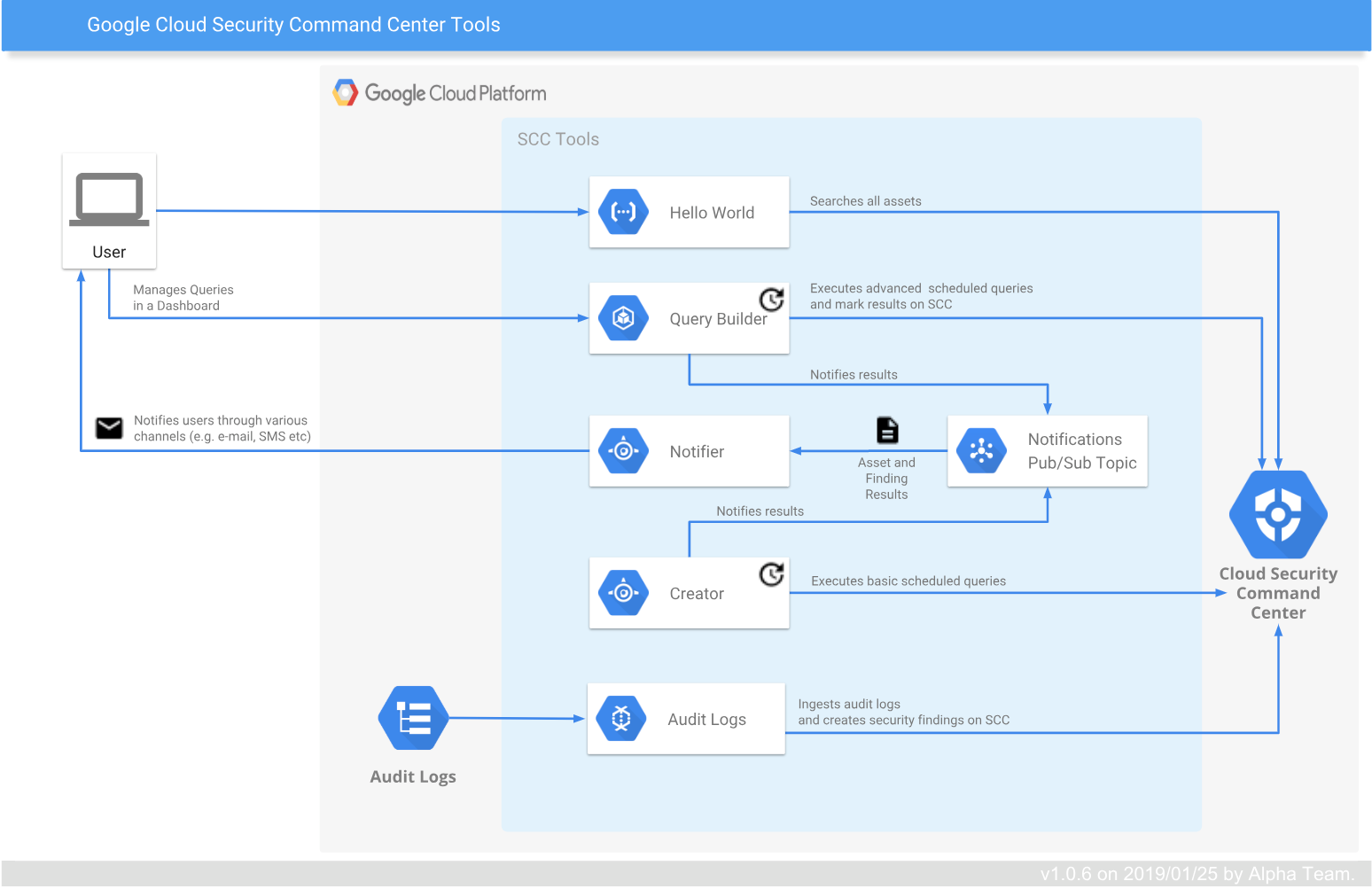
The basic command center comprises of several security tools from Google. However, it is a flexible platform that integrates with a wide range of third party tools to enhance security and increase coverage in terms of components, risks, and practices.
Features
- View and address misconfigured issues such as firewalls, IAM rules, etc.
- Detect, respond and prevent threats and compliance issues
- Identify most of the vulnerabilities and risks such as mixed content, flash injection, and more while allowing you to easily explore the results.
- Identify publicly exposed assets such as VMs, SQL instances, buckets, datasets, etc.
- Asset discovery and inventory, identifying vulnerabilities, sensitive data, and anomalies,
- Integrates with third-party tools to enhance the identification and addressing of compromised endpoints, network attacks, DDoS, policy and compliance violations, instance security vulnerabilities, and threats.
Generally, the security command center is a flexible solution to meet every organization’s needs. The tool integrates with various Google security tools such as Cloud Data Loss Prevention, Web Security Scanner, as well as third party security solutions like McAfee, Qualys, CloudGuard, and more.
Forseti
Forseti is an open-source, that helps you to gain visibility of your GCP environment, address vulnerabilities as well as monitor and understand policies and compliance. It consists of various core modules that you can easily enable, configure, and execute independently.
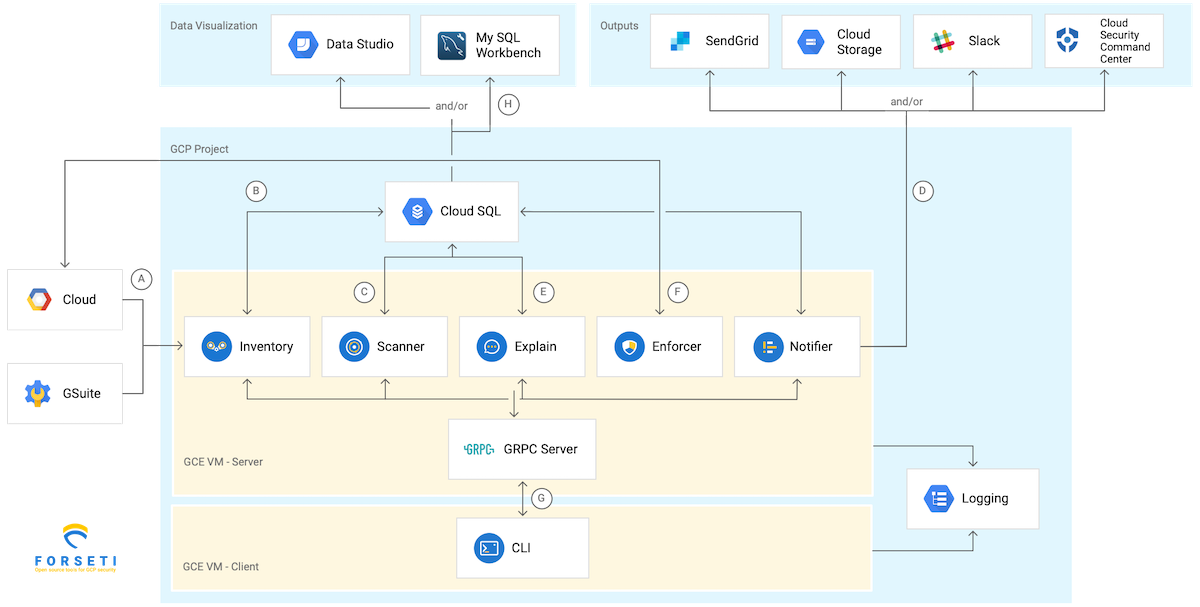
There are also several add-on modules to enhance Forseti capabilities and customization.
Features
- Monitor your GCP resources to ensure that the security features such as access controls are in place and protected against unauthorized modifications.
- Take inventory of the resources and keep track of your GCP environment.
- Understand and enforce security and firewall policies and rules
- Evaluate the settings and ensure that they are in compliance and that they do not expose any or your GCP resources.
- Gain visible insights into your Cloud Identity and Access Management (Cloud IAM) policies in addition to showing what access users have to the resources.
- Has a Visualizer that helps you to understand your GCP security structure as well as identifying policy adherence and violations.
CloudGuard
CloudGuard is a cloud-native agentless security solution that assesses and visualizes the security posture of the GPC platform, hence enabling teams to protect their cloud assets and environment. The solution analyzes various assets, including the compute engine, databases, virtual machines, and other services, as well as the network firewalls and more.
Features
- Provide continuous monitoring of the security policies and events, detect changes, and check compliance.
- Identify and address misconfigurations as well as vulnerabilities and related security risks.
- Harden security and ensure compliance and best practices.
- Powerful visualizations and security posture of the GCP network assets
- Integrates seamlessly with the GCP as well as other public clouds such as Amazon web services and Microsoft Azure.
- Enforcing governance policies that suite the organization’s unique security needs.
Cloudsploit
Cloudsploit is a powerful solution that checks and automatically detects security configuration issues in the Google Cloud Platform as well as other public cloud services such as Azure, AWS, Github, and Oracle.
The security solution connects to the GCP projects, where it provides monitoring of the various components. It provides detection of security misconfigurations, malicious activities, exposed assets, and other vulnerabilities.
Features
- Easy to deploy and use security configuration monitoring solution with an alerting feature
- Fast and reliable to-the-point scans and reports
- Provides insights into the security posture and compliance
- Checks the systems while analyzing the privileges, roles, networks, certificates, usage trends, authentication, and various configurations.
- Provides account level overviews that enable you to see and easily identify trends and relative risk levels over time.
- An API-based design that makes it easy to integrate the tool with various CISO dashboards and other reporting systems.
Prisma Cloud
Prisma cloud is an integrated, cloud-native solution for ensuring proper implementation and maintenance of the security and compliance of the GCP environment, applications, and resources.
The comprehensive tool has APIs that integrate seamlessly with the GCP service to provide continuous insights, protection, and reporting in addition to compliance enforcement.
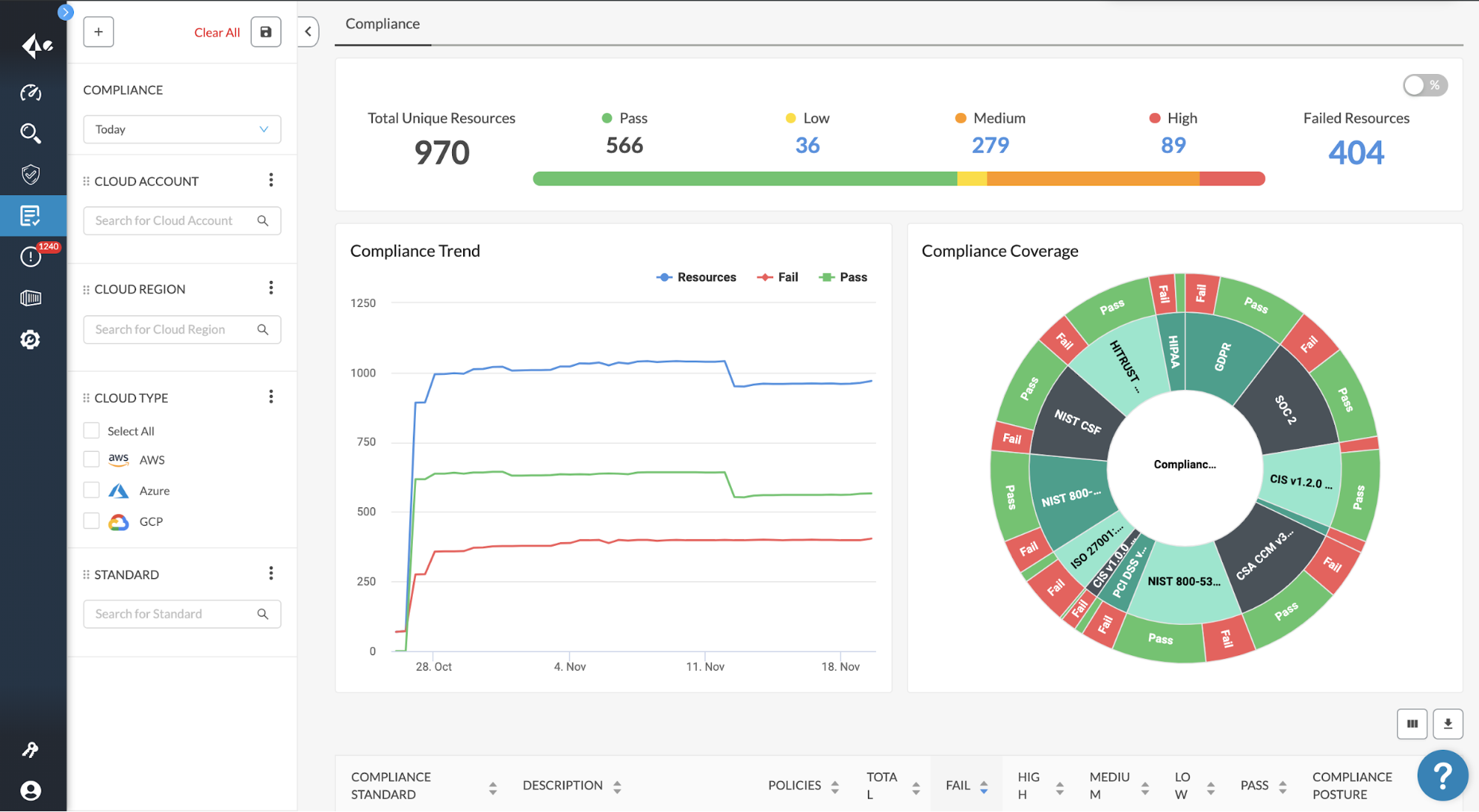
Features
- Comprehensive, scalable, API-based security solution that provides insights, continuous monitoring, threat detection, and response.
- Complete visibility that allows you to identify and address misconfigurations, workload vulnerabilities, network threats, data leakage, insecure user activity and more
- Protects workloads, containers, and apps running across the Google Cloud Platform.
- Custom enforcement of security policies based on applications, users, or devices.
- Easily enforce governance policies and compliance with a wide range of standards including, but limited to, NIST, CIS, GDPR, HIPAA, and PCI.
Cloud Custodian
Cloud custodian is an open-source, flexible, and lightweight rules engine for cloud security and governance. The solution enables you to manage your GCP accounts and resources securely. In addition to security, the integrated solution helps to optimize costs by managing resource usage hence enabling you to save money.
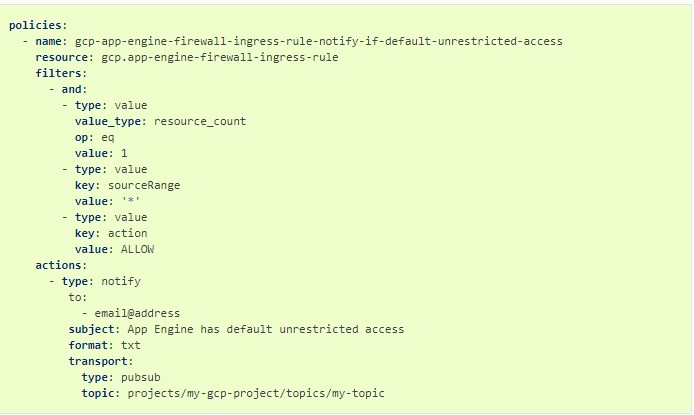
Features
- Real-time enforcement of security policies and compliance in areas such as access management, firewall rules, encryption, tags, garbage collection, automated off-hours resource management, etc.
- Provides unified metrics and reports
- Integrates seamlessly with the Google Cloud Platform functions
- Automatically provision GCP AuditLog and other serverless functions.
McAfee MVISION
The McAfee MVISION is a security solution that integrates with Google Cloud SCC to provide teams with the visibility into the security posture of their GCP resources, detect and address vulnerabilities and threats.
Also, the cloud-native solution provides configuration audits that enable security teams to identify and address hidden risks. It has cloud policy engines that enhance the GCP queries hence the ability to find a wide range of security misconfigurations on various GCP services.
Features
- Provides insights that help teams to identify and address security and compliance issues.
- Enhances and comprehensive configurations audit to find hidden vulnerabilities, hence allow teams to enforce best practices.
- Provides visibility to empower teams with the ability to investigate security incidents, anomalies, violations, and threats hence enabling quick remedial actions in the cloud security command center.
- Notifications when there are a security threat or policy violations.
- Visualize vulnerabilities and threats on Google Cloud SCC dashboards.
Netskope
Netskope enables you to quickly identify and address security issues, threats, and misconfigurations that expose your digital assets to threats and attacks.
In addition to complementing GSCC in protecting the compute instances, object storage, databases, and other assets, Netskope goes deeper and broader to give insights into misconfigurations, advanced threats, and risks.
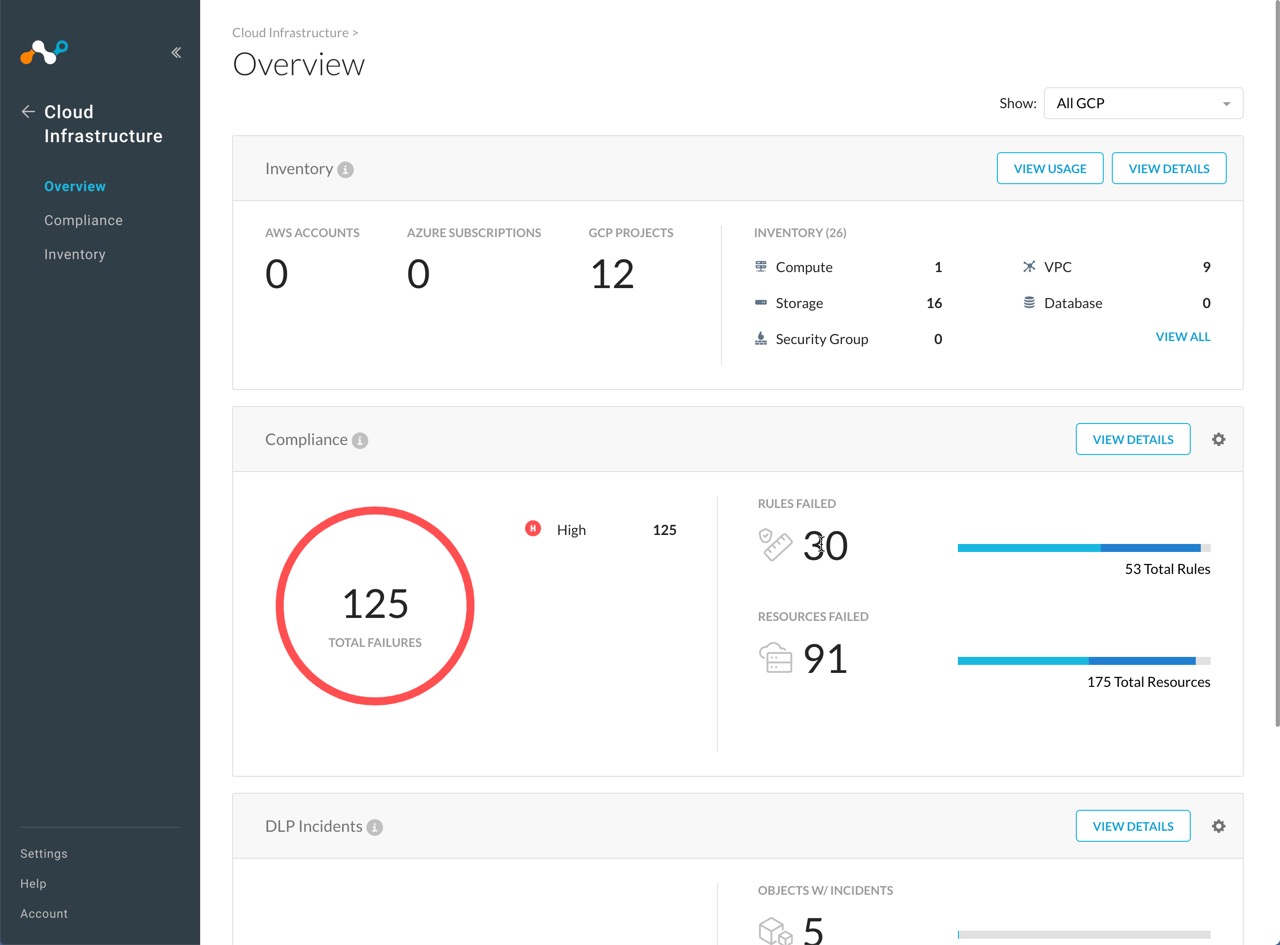
Features
- Gain valuable, real-time visibility into threats, vulnerabilities, misconfigurations, and compliance on your Google cloud platform.
- Identify and address any vulnerabilities, misconfigurations, compliance, and security risks.
- Continuously monitor your security configuration and check them against best practices. Identify issues and enforce standards based on the best practices and CIS benchmarks.
- Compliance reporting – takes inventory of your GCP resources to determine and report misconfigurations and anomalies.
Tripwire
Tripwire Cloud Cybersecurity is a comprehensive solution that enables organizations to implement effective security configurations and controls, hence prevent exposing their digital assets. It combines configurations management, a cloud management assessor (CMA), and file integrity monitoring capabilities to identify publicly exposed resources and data on the GCP.
Key features
- Discover and address publicly exposed GCP storage buckets or instances to ensure proper configuration and data security.
- Gathers, analyses, and then scores the GCP configuration’s data, thereby enabling you to identify and address misconfigurations.
- Monitor configuration changes that compromise the GCP cloud or expose assets
- The Tripwire cloud management assessor monitors the Google Cloud Platform for misconfigurations upon which it alerts the security teams for remediation.
Scout Suite
The Scout Suite is an open-source security audit tool for GCP and other public clouds. It enables security teams to assess the security posture of their GCP environments, identify misconfiguration and other vulnerabilities.
The Scout Suite configuration review tool easily interacts with the APIs, that Google exposes, to gather and analyze the security posture data. It then highlights any vulnerabilities that it identifies.
Aqua Security
Aqua Security is a platform that provides organizations with visible insights into GCP and other AWS, Oracle Cloud, Azure. It helps to simplify and enforce policies and compliance.
Aqua integrates with Google’s Cloud Security Command Center, other third-party solutions, as well as analysis and monitoring tools. This provides you with the ability to view and manage your security, policies, and compliance from a single place.
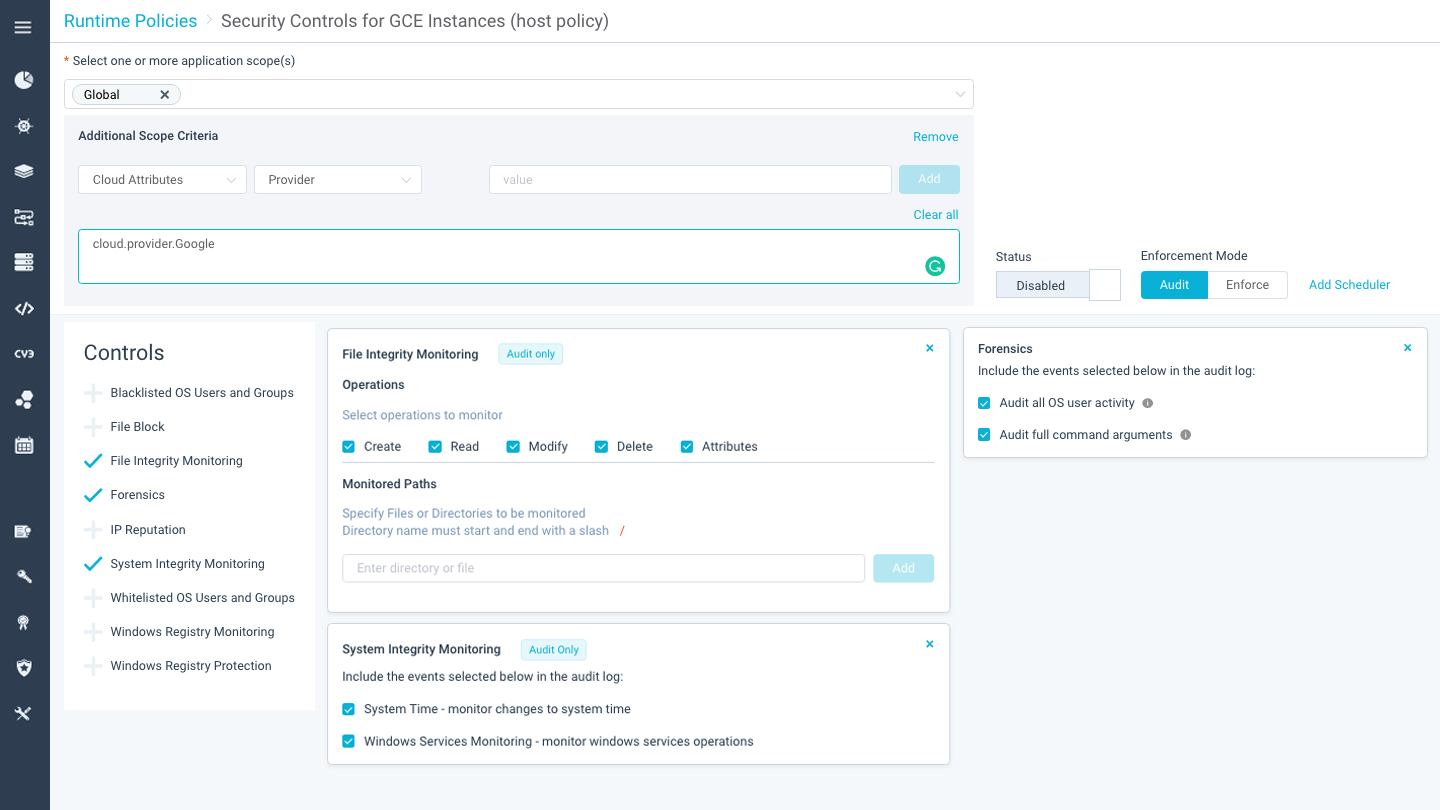
Features
- Scan, identify and address misconfigurations, malware, and vulnerabilities on images
- Enforce the integrity of the images across the entire application life cycle
- Define and enforce privileges and compliance standards such as PCI, GDPR, HIPAA, etc.
- Provides enhanced threat detection and mitigation measures for the GCP container workloads.
- Create and enforce image assurance policies to prevent compromised, vulnerable or misconfigured images from running in your Google Kubernetes Engine environment
- It helps you to build an audit trail for forensics and compliance.
- It provides continuous scanning of the settings to find vulnerabilities and anomalies.
GCPBucketBrute
The GCPBucketBrute is a customizable and effective open-source security solution for detecting open or misconfigured Google Storage buckets. Generally, this is a script that enumerates Google storage buckets to establish if there are insecure configuration and privilege escalations.
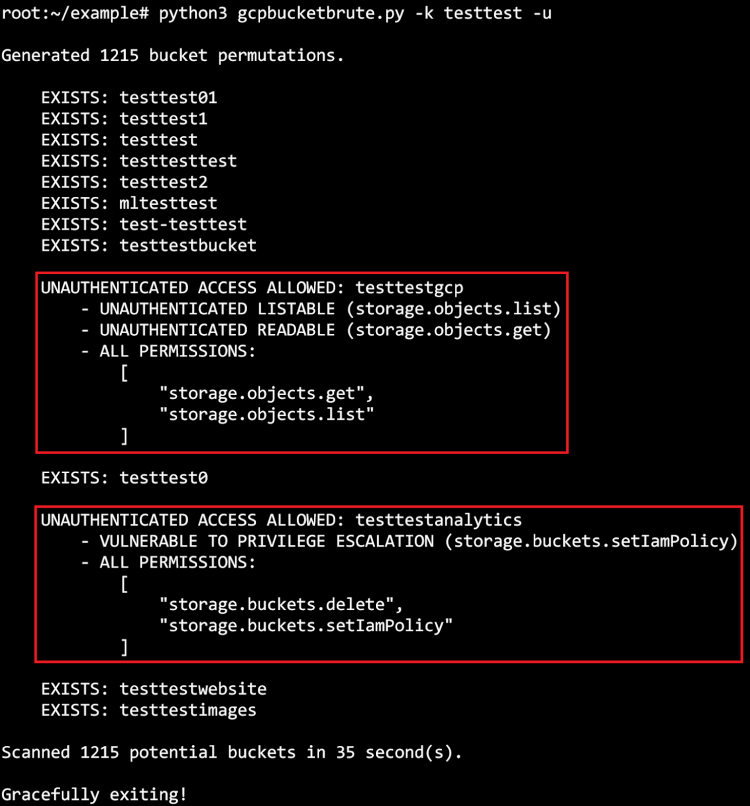
Features
- Discover open GCP buckets as well as risky privilege escalations on cloud instances on the platform.
- Check the privilege in every discovered bucket and determine if they are vulnerable to privilege escalation.
- Suitable for Google cloud penetration tests, red team engagements, and more.
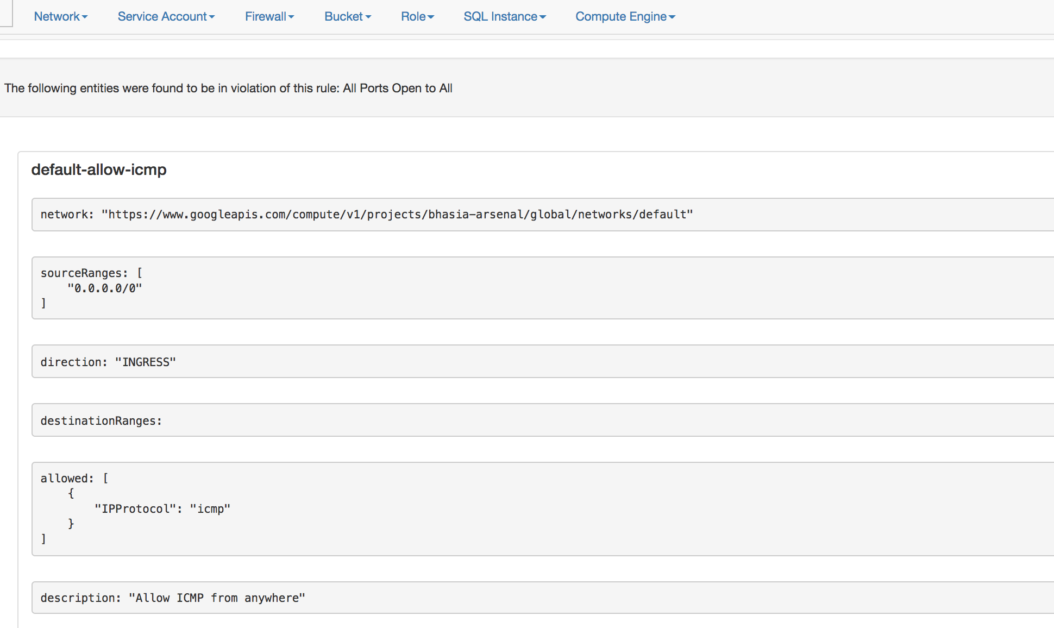
Cloud Security Suite
Security FTW Cloud Security Suite is another open-source for auditing the security posture of GCP infrastructure. The all in one solution helps you to audit the configurations and security of the GCP’s accounts and can identify a wide range of vulnerabilities.
Conclusion
The Google Cloud Platform provides a flexible and highly scalable IT infrastructure. However, just like other cloud environments, it can have vulnerabilities if not configured properly, and bad actors can exploit to compromise the systems, steal data, infect with malware, or commit other cyber attacks.
Luckily, businesses can secure their GCP environments by following good security practices and using reliable tools to continuously protect, monitor, and provide visibility into the configurations and overall security posture.



