 by Chandan Kumar | February 9, 2020 | Security
by Chandan Kumar | February 9, 2020 | Security
Don’t let someone bypass Cloudflare protection and misuse your origin server!
Cloudflare is one of the popular CDN and security platform, powering millions of sites from small to enterprise. When you implement Cloudflare for your website, all the traffic is secured and accelerated. But this is true when a site is accessed using a domain name. How about if someone finds out the actual server IP (Origin) and misuse it?
Finding server IP for the site behind Cloudflare doesn’t take much. You can find out how, as explained here and here. You see, just implementing CDN and Cloud-based WAF is not enough. You should also consider protecting origin.
So, what’s the solution?
Argo Tunnel – a smart solution by Cloudflare to protect the origin server from direct attack.
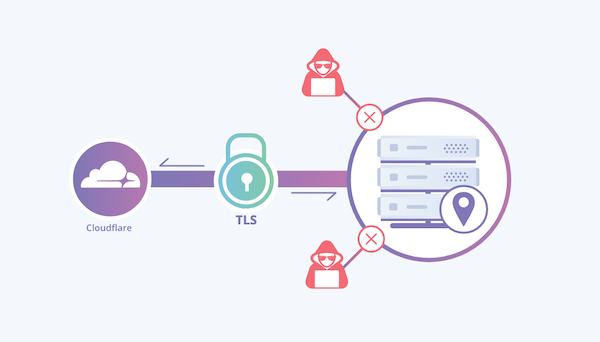
It is a daemon that you need to install on your server that creates an encrypted tunnel between server to Cloudflare network. There is zero complicated ACL/IP table configuration.
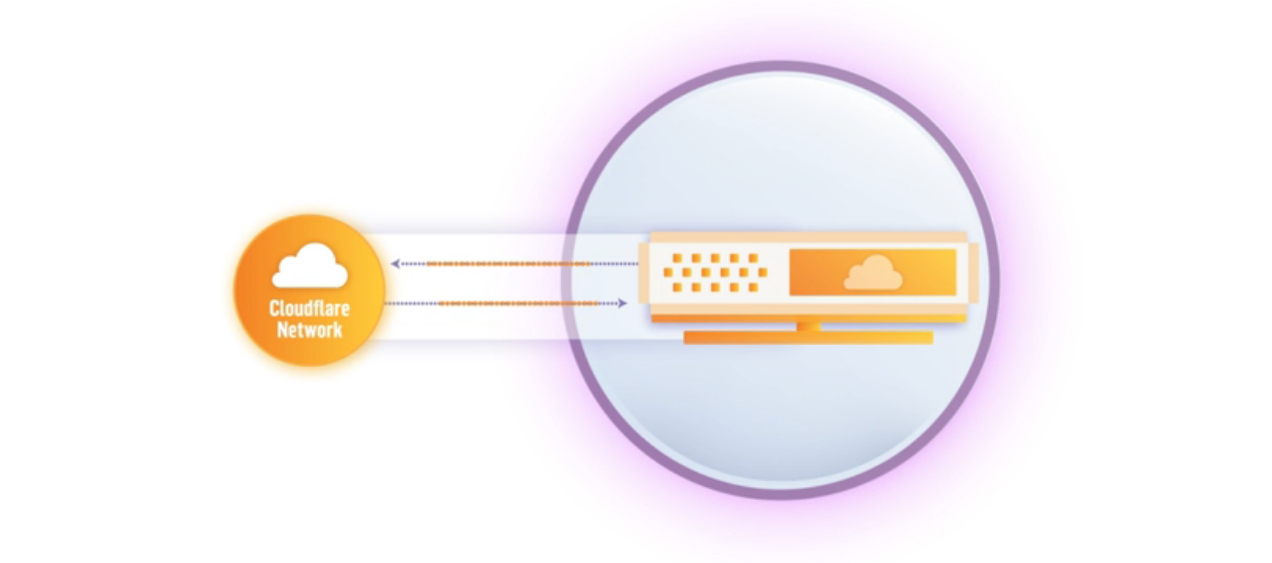
The good news is you don’t need to be under PRO or higher plan. You can get it started even you are under the FREE plan. All you pay is for Argo subscription, which starts from $5 per month.
Let’s get it started with installation and setup.
Installing Cloudflare daemon
- Login to the origin server with root or sudo privilege
- Download the latest stable package. I am on Ubuntu so, .deb file for other OS, check out the official download page.
wget https://bin.equinox.io/c/VdrWdbjqyF/cloudflared-stable-linux-amd64.deb- Install the downloaded package
dpkg -i cloudflared-stable-linux-amd64.deb- Let’s verify the version to ensure it has installed
[email protected]:~# cloudflared --version
cloudflared version 2020.2.0 (built 2020-02-07-1653 UTC)
[email protected]:~#Great!
Authenticate Daemon
Next would be to authenticate to Cloudflare using the daemon. Run the below command
cloudflared tunnel login- It will prompt you the URL which you can use to login to Cloudflare and authorize the site.
[email protected]:~# cloudflared tunnel login
Please open the following URL and log in with your Cloudflare account:
https://dash.cloudflare.com/argotunnel?callback=https://login.argotunnel.com%XXXXX-XXX-XXXXXX;
Leave cloudflared running to download the cert automatically.
INFO[0030] Waiting for login...
INFO[0060] Waiting for login...
INFO[0090] Waiting for login...
INFO[0120] Waiting for login...
You have successfully logged in.
If you wish to copy your credentials to a server, they have been saved to:
/root/.cloudflared/cert.pem
[email protected]:~#- Once authorized, you should see something like this.
Starting the tunnel
Let’s start the tunneling below.
cloudflared tunnel --hostname [HOSTNAME] http://localhost:80Ex:
[email protected]:~# cloudflared tunnel --hostname tunnel.geekflare.com http://0.0.0.0:80
WARN[0000] Cannot determine default configuration path. No file [config.yml config.yaml] in [~/.cloudflared ~/.cloudflare-warp ~/cloudflare-warp /usr/local/etc/cloudflared /etc/cloudflared]
INFO[0000] Version 2020.2.0
INFO[0000] GOOS: linux, GOVersion: go1.12.7, GoArch: amd64
INFO[0000] Flags hostname=tunnel.geekflare.com proxy-dns-upstream="https://1.1.1.1/dns-query, https://1.0.0.1/dns-query"
INFO[0000] cloudflared will not automatically update when run from the shell. To enable auto-updates, run cloudflared as a service: https://developers.cloudflare.com/argo-tunnel/reference/service/
INFO[0000] Starting metrics server addr="127.0.0.1:35597"
INFO[0000] Proxying tunnel requests to http://0.0.0.0:80
INFO[0000] Connected to LAX connectionID=0
INFO[0001] Each HA connection's tunnel IDs: map[0:xxx] connectionID=0
INFO[0001] Route propagating, it may take up to 1 minute for your new route to become functional connectionID=0
INFO[0003] Connected to LAXCongratulations! origin is locked down now. Try to access your website using origin IP, and you should see the “connection refused” message.
Starting Argo Tunnel at Boot
Let’s ensure the Argo Tunnel is started when the server reboot. Run the below command on the server.
cloudflared service installConclusion
Cloudflare Argo Tunnel looks promising. Just in around 30 minutes, you can protect the origin server.
Tags: Cloudflare



