Geekflare is supported by our audience. We may earn affiliate commissions from buying links on this site.
Cybersecurity issues are growing and becoming more complicated as technology advances.
Though you can’t stop cybercriminals from getting smarter, you can employ security systems like IDS and IPS to reduce the attack surface or even block them. This brings us to the battle – IDS vs. IPS to choose what’s better for a network.
And if you want the answer to that, you need to understand what these technologies are in their essence, how they work, and their types. It will help you choose the better option for your network.
That said, both IDS and IPS are secure and effective, each with its pros and cons, but you can’t take a chance when it comes to security.
This is why I’ve come up with this comparison – IDS vs. IPS to help you understand their capabilities and find the better solution to safeguard your network.
Let the battle begin!
IDS vs. IPS: What Are They?
Before we start comparing IDS vs. IPS, let’s find out what they are in the first place, starting with IDS.
What Is an IDS?
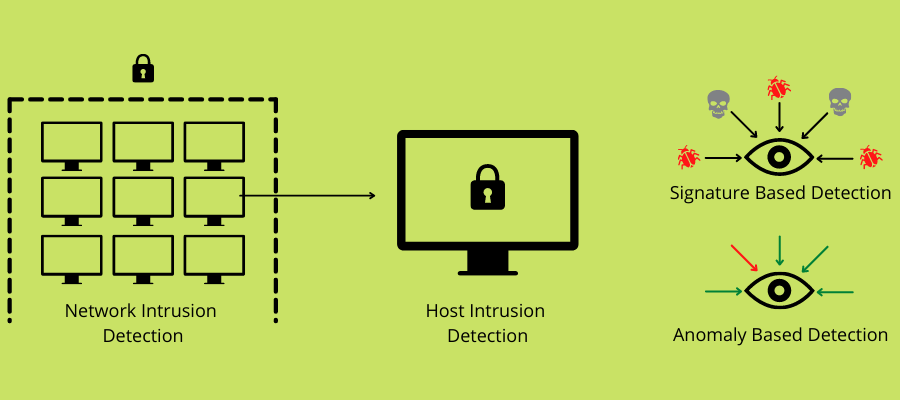
An Intrusion Detection System (IDS) is a software solution that monitors a system or network for intrusions, policy violations, or malicious activities. And when it detects an intrusion or violation, the software reports it to the administrator or security personnel. It helps them investigate the reported incident and take suitable remedies.
This passive monitoring solution can alert you to detect a threat, but it can’t take direct measures against it. It’s like a security system installed in a building that can notify the security guard about an incoming threat.
An IDS system aims to detect a threat before it infiltrates a network. It gives you the power to take a look at your network without obstructing the network traffic flow. Apart from detecting policy violations, it can guard against threats like information leaks, unauthorized access, configuration errors, Trojan horses, and viruses.
It works best when you don’t want to obstruct or slow down the traffic flow even when an issue surfaces but to safeguard your network assets.
What Is An IPS?
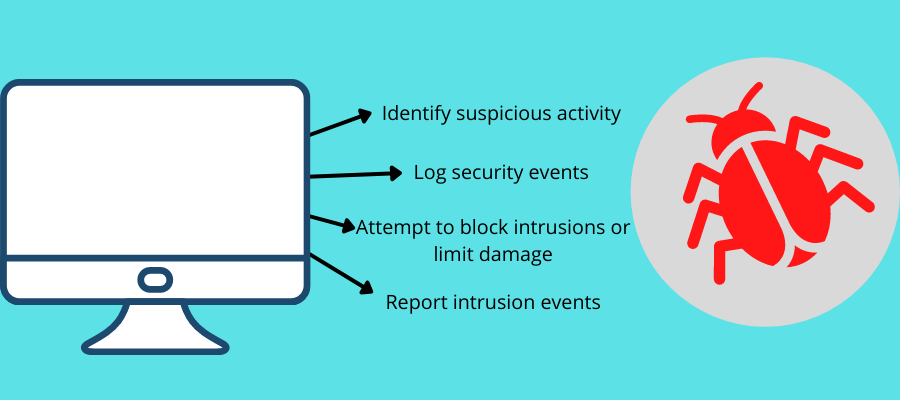
Intrusion Prevention System (IPS) is also called Intrusion Detection & Prevention System (IDPS). It is a software solution that monitors a system or network activities for malicious incidents, logs information on these activities, reports them to the administrator or security personnel, and attempts to stop or block them.
This is an active monitoring and prevention system. You can consider it as an extension of IDS because both methods monitor malicious activities. However, unlike IDS, IPS software is placed behind the network firewall communicating in line with the incoming traffic and blocking or preventing detected intrusions. Think of it as the (cyber) security guard for your network.
Upon detecting a threat, IPS can take various actions such as sending alarms, dropping identified malicious packets, blocking the malicious IP address from accessing the network, and resetting connections. In addition, it can also correct errors related to cyclic redundancy check (CRC), defragmented packet streams, clean up extra network layers and transport options, and mitigate errors associated with TCP sequencing.
IPS is the best option for you if you want to block attacks as soon as the system detects them, even if you have to close all traffic, including the legitimate ones, for security. Its goal is to mitigate damage from both external and internal threats in your network.
IDS vs. IPS: Types
Types of IDS
IDS is divided based on where the threat detection happens or what detection method is employed. IDS types based on the place of detection, i.e., network or host, are:
1. Network Intrusion Detection Systems (NIDS)
NIDS is a part of network infrastructure, monitoring packets flowing through it. It co-exists with the devices with a tap, span, or mirroring ability like switches. NIDS is positioned at a strategic point(s) within a network to monitor incoming and outgoing traffic from all the connected devices.
It analyzes traffic passing through the whole subnet, matching those traffic passing the subnets to the known attack library. Once NIDS identifies the attacks and senses an abnormal behavior, it alerts the network admin.
You can install a NIDS behind the firewalls on the subnet and monitor whether or not someone tries to infiltrate your firewall. NIDS can also compare similar packets’ signatures with matching records to link malicious detected packets and stop them.
There are two types of NIDS:
- On-line NIDS or in-line NIDS deals with a network in real-time. It analyzes Ethernet packets plus applies specific rules to determine whether it’s an attack or not.
- Off-line NIDS or tap mode deals with collected data. It passes the data through some processes and decides the outcome.
Furthermore, you can combine NIDS with other security technologies to increase prediction and detection rates. For example, NIDS based on Artificial Neural Network (ANN) can analyze massive data volumes smartly because its self-organizing structuring allows INS IDS to recognize attack patterns more efficiently. It can predict attacks based on previous mistakes that led to the intrusion and helps you develop an early-stage earning system.
2. Host-based Intrusion Detection Systems
Host-based Intrusion Detection Systems (HIDS) are the solution running on separate devices or hosts on a network. It can only monitor incoming and outgoing data packets from the connected devices and alert the admin or users upon detecting suspicious activity. It monitors system calls, file changes, application logs, etc.
HIDS takes snapshots of the current files in the system and matches them to the previous ones. If it finds that a critical file is deleted or modified, the HIDS sends an alert to the admin to investigate the issue.
For example, HIDS can analyze password logins and compare them against known patterns utilized to carry out brute force attacks and identify a breach.
These IDS solutions are used widely on mission-critical machines whose configurations are not expected to change. As it monitors events directly on hosts or devices, a HIDS solution can detect threats that a NIDS solution might miss.
It is also effective in identifying and preventing integrity breaches such as Trojan horses and working in encrypted network traffic. This way, HIDS protects sensitive data like legal documents, intellectual property, and personal data.
Apart from these, IDS can also be of other types, including:
- Perimeter Intrusion Detection System (PIDS): Acting as the first line of defense, it can detect and locate intrusion attempts on the central server. This setup usually consists of a fiber optic or electronic device sitting onto a server’s virtual perimeter fence. When it senses a malicious activity such as someone trying to attempt access through a different method, it alerts the admin.
- VM-based Intrusion Detection System (VMIDS): These solutions can combine the IDS mentioned above or one of them. The difference is that it is deployed remotely using a virtual machine. It’s relatively new and mainly used by managed IT service providers.
Types of IPS
In general, intrusion prevention systems (IPS) are of four types:
1. Network-based Intrusion Prevention System (NIPS)
NIPS can identify and prevent suspicious or malicious activities by analyzing data packets or checking protocol activity throughout a network. It can gather data from the network and host to detect permitted hosts, operating systems, and applications on the network. In addition, NIPS logs data on normal traffic for finding changes from the ground up.
This IPS solution mitigates attacks by limiting bandwidth utilization, sending TCP connections, or rejecting packets. However, NIPS is not effective in analyzing encrypted traffic and handling direct attacks or high traffic loads.
2. Wireless Intrusion Prevention System (WIPS)
WIPS can monitor a wireless network to detect suspicious traffic or activities by analyzing wireless network protocols and taking measures to prevent or remove them. WIPS is implemented typically overlaying the current wireless LAN network infrastructure. However, you can also deploy them standalone and enforce a no-wireless policy in your organization.
This IPS solution can prevent threats like a misconfigured access point, denial of service (DOS) attacks, honeypot, MAC spoofing, man-in-the-middle attacks, and more.
3. Network Behaviour Analysis (NBA)
NBA works on anomaly-based detection, looking for anomalies or deviations from normal behavior to suspicious behavior in the network or system. Therefore, for it to work, the NBA must go through a training period to learn the normal behavior of a network or system.
Once an NBA system learns the normal behavior, it can detect deviations and flag them as suspicious. It is effective, but it won’t work while still in the training phase. However, once it graduates, you can rely on it.
4. Host-based Intrusion Prevent Systems (HIPS)
HIPS solutions can monitor critical systems for malicious activities and prevent them by analyzing their code behavior. What’s best about them is that they can also detect encrypted attacks apart from safeguarding sensitive data related to personal identity and health from the host systems. It works on a single device and is often used with a network-based IDS or IPS.
IDS vs. IPS: How Do They Work?
There are different methodologies used in monitoring and preventing intrusions for IDS and IPS.
How Does An IDS Work?
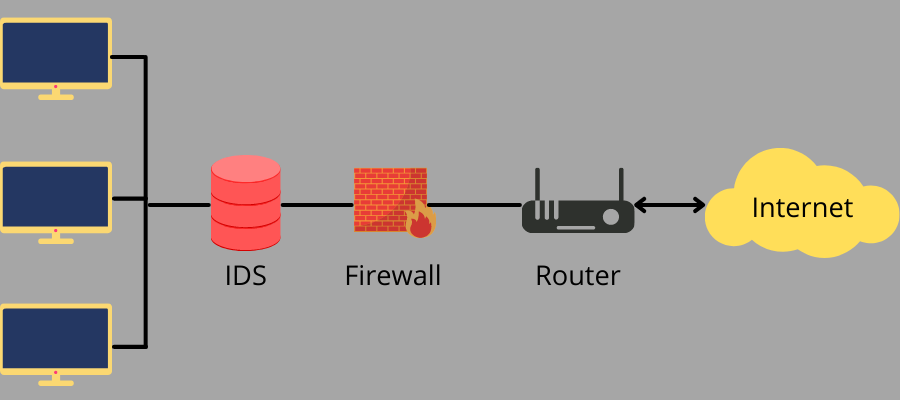
IDS uses three detection methods to monitor traffic for malicious activities:
1. Signature-based or Knowledge-based Detection
Signature-based detection monitors specific patterns like cyberattack signatures that malware uses or byte sequences in the network traffic. It works the same way as antivirus software in terms of identifying a threat by its signature.
In signature-based detection, the IDS can identify known threats easily. However, it may not be effective in new attacks with no available patterns, as this method works solely based on previous attack patterns or signatures.
2. Anomaly-based or Behavior-based Detection
In anomaly-based detection, the IDS monitors violations and intrusions in a network or system by monitoring system logs and determining whether any activity seems anomalous or deviated from normal behavior specified for a device or network.
This method can detect unknown cyberattacks as well. IDS can also use machine learning technologies to build a trusted activity model and establish it as the baseline for a normal behavioral model to compare new activities and declare the outcome.
You can train these models based on your specific hardware configurations, applications, and system needs. As a result, IDS with behavior detection have enhanced security properties than signature-based IDS. Although it may show some false positives sometimes, it works efficiently in other aspects.
3. Reputation-based Detection
IDS using reputation-based detection methods, recognize threats based on their reputation levels. It is done by identifying communication between a friendly host inside your network and the one attempting to access your network based on their reputation for violations or malicious actions.
It collects and tracks different file attributes like source, signature, age, and usage statistics from users using the file. Next, it can use a reputation engine with statistical analysis and algorithms to analyze the data and determine whether it’s threatening or not.
Reputation-based IDS is used mainly in anti-malware or antivirus software and implemented on batch files, executable files, and other files that might carry unsafe code.
How Does An IPS Work?
Similar to IDS, IPS also works with methods like signature-based and anomaly-based detection, in addition to other methods.
1. Signature-based Detection
IPS solutions using signature-based detection monitor data packets incoming and outgoing in a network and compare them with previous attack patterns or signatures. It works on a library of known patterns with threats carrying malicious code. When it discovers an exploit, it records and stores its signature and uses it for further detection.
A signature-based IPS is of two types:
- Exploit-facing signatures: IPS identifies intrusions by matching signatures with a threat signature in the network. When it finds a match, it tries to block it.
- Vulnerability-facing signatures: Hackers target existing vulnerabilities in your network or system, and the IPS tries to protect your network from these threats that might go undetected.
2. Statistical Anomaly-based or Behavior-based Detection
IDS using statistical anomaly-based detection can monitor your network traffic to find inconsistencies or anomalies. It sets a baseline to define the normal behavior for the network or system. Based on this, the IPS will compare the network traffic and flag suspicious activities that deviate from the normal behavior.
For example, the baseline could be a specified bandwidth or protocol used for the network. If the IPS finds traffic increasing the bandwidth abruptly or detects a different protocol, it will trigger an alarm and block the traffic.
However, you must take care of configuring the baselines intelligently to avoid false positives.
3. Stateful Protocol Analysis
An IPS, using stateful protocol analysis, detects deviations of a protocol state like anomaly-based detection. It uses predefined universal profiles according to accepted practices set by industry leaders and vendors.
For example, the IPS can monitor requests with corresponding responses, and each request must consist of predictable responses. It flags responses falling outside the expected outcomes and analyzes them further.
When an IPS solution monitors your systems and network and finds suspicious activity, it alerts and performs some actions to prevent it from accessing your network. Here is how:
- Strengthening firewalls: The IPS might detect a vulnerability in your firewalls that paved the way for the threat to enter your network. To provide security, the IPS might change its programming and strengthen it while fixing the issue.
- Performing system clean-up: Malicious content or damaged files might corrupt your system. This is why it performs a system scan to clean it up and remove the underlying issue.
- Closing sessions: The IPS can detect how an anomaly has occurred by finding its entry point and blocking it. For this, it might block IP addresses, terminate the TCP session, etc.
IDS vs. IPS: Similarities and Differences
Similarities Between IDS and IPS
The early processes for both IDS and IPS are similar. Both of them detect and monitor the system or network for malicious activities. Let’s see their common grounds:
- Monitor: Once installed, IDS and IPS solutions monitor a network or system based on the specified parameters. You can set those parameters based on your security needs and network infrastructure and let them inspect all the traffic incoming and outgoing from your network.
- Threat detection: Both of them read all the data packets flowing in your network and compare those packets to a library containing known threats. When they find a match, they flag that data packet as malicious.
- Learn: Both of these technologies use modern technologies like machine learning to train themselves for a period and understand emerging threats and attack patterns. This way, they can better respond to modern threats.
- Log: When they detect suspicious activity, they record it along with the response. It helps you understand your protection mechanism, find vulnerabilities in your system, and train your security systems accordingly.
- Alert: As soon as they detect a threat, both IDS and IPS send alerts to security personnel. It helps them to be prepared for every circumstance and take quick action.
Until this, IDS and IPS work similarly, but what happens after differentiates them.
Difference Between IDS and IPS
The main difference between IDS and IPS is that IDS works as a monitoring and detection system while IPS works as a prevention system apart from monitoring and detection. Some differences are:
- Response: IDS solutions are passive security systems that only monitor and detect networks for malicious activities. They can alert you but don’t take any action on their own to prevent the attack. The network admin or security personnel assigned must take action immediately to mitigate the attack. On the other hand, IPS solutions are active security systems that monitor and detect your network for malicious activities, alert, and automatically prevent the attack from happening.
- Positioning: IDS is placed at the edge of a network to collect all events and log and detect violations. Positioning this way gives the IDS the maximum visibility for data packets.IPS software is placed behind the network firewall communicating in line with the incoming traffic to prevent intrusions better.
- Detection mechanism: IDS uses signature-based detection, anomaly-based detection, and reputation-based detection for malicious activities. Its signature-based detection only includes exploit-facing signatures. On the other hand, IPS uses signature-based detection with both exploit-facing and vulnerability-facing signatures. Also, IPS uses statistical anomaly-based detection and stateful protocol analysis detection.
- Protection: If you are under threat, IDS could be less helpful as your security personnel needs to figure out how to secure your network and clean up the system or network immediately.IPS can perform automatic prevention by itself.
- False positives: If IDS gives a false positive, you may find some convenience. But if IPS does so, the whole network would suffer as you will need to block all the traffic – incoming and outgoing the network.
- Network performance: As IDS is not deployed in-line, it does not reduce network performance. However, network performance can reduce due to IPS processing, which is in line with the traffic.
IDS vs. IPS: Why They Are Crucial for Cybersecurity
You may hear various incidences of data breaches and hacks happening in almost every industry with an online presence. For this, IDS and IPS play an important role in safeguarding your network and systems. Here’s how:
Enhance Security

IDS and IPS systems use automation for monitoring, detection, and prevention of malicious threats. They can also use emerging technologies like machine learning and artificial intelligence to learn patterns and remedy them effectively. As a result, your system is secure from threats like viruses, DOS attacks, malware, etc., without requiring extra resources.
Enforcing Policies
You can configure IDS and IPS based on your organizational needs and enforce security policies for your network that every packet entering or leaving the network must adhere to. It helps you protect your systems and network and spot deviations quickly if someone tries to block the policies and break into your network.
Regulatory Compliance
Data protection is serious in the modern security landscape. This is why regulatory compliance bodies like HIPAA, GDPR, etc., regulate companies and make sure they invest in technologies that can help protect customer data. By implementing an IDS and IPS solution, you comply with these regulations and face no legal trouble.
Saves Reputation
Implementing security technologies like IDS and IPS shows you care to protect your customers’ data. It gives your brand a good impression on your customers and elevates your reputation within and outside your industry. In addition, you also save yourself from threats that might leak your sensitive business information or cause reputation damage.
Can IDS & IPS work together?
In a word, Yes!
You can deploy both IDS and IPS together in your network. Deploy an IDS solution to monitor and detect traffic while letting it understand traffic movement comprehensively inside your network. Also, you can use IPS in your system as an active measure to prevent security issues in your network.
This way, you can also avoid the overhead of choosing IDS vs. IPS altogether.
Moreover, implementing both technologies gives you all-around protection for your network. You can understand previous attack patterns to set better parameters and prepare your security systems to fight more effectively.
Some of the providers for IDS and IPS are Okta, Varonis, UpGuard, etc.
IDS vs. IPS: What Should You Choose? 👈
Choosing IDS vs. IPS must be solely based on your organization’s security needs. Consider how big your network is, what your budget is, and how much protection you need to choose the one.
If you ask what’s better in general, it must be IPS as it offers prevention, monitoring, and detection. However, it would help if you chose a better IPS from a trustworthy provider as it can show false positives.
As both have pros and cons, there’s no clear winner. But, as explained in the previous section, you can go for both of these solutions from a reliable provider. It will offer superior protection to your network from both the standpoints – intrusion detection and prevention.



