Previously I showed you how to set up SPF and DKIM on CentOS/RHEL mail server. Two common pieces of software that can do DKIM signing and verification on Linux are OpenDKIM and Amavis. In that tutorial I used Amavis, because at the time OpenDKIM isn’t included in any CentOS 8/RHEL 8 repository. As of now, OpenDKIM is included in the EPEL repository. Some folks prefer to use OpenDKIM so I will show you how in this tutorial.
What is DKIM?
DKIM (DomainKeys Identified Mail) is a type of TXT records in DNS that can help with preventing email spoofing and making legitimate emails delivered into the recipient’s inbox instead of spam folder. DKIM uses a private key to add a signature to emails sent from your domain. Receiving SMTP servers verify the signature by using the corresponding public key, which is published in your domain’s DNS records.
Disabling DKIM in Amavis
If you followed my previous Amavis tutorial, but now you want to use OpenDKIM, you need to disable DKIM in Amavis. Edit the main configuration file.
sudo nano /etc/amavisd/amavisd.conf
Find the following lines.
$enable_dkim_verification = 1; # enable DKIM signatures verification $enable_dkim_signing = 1; # load DKIM signing code, keys defined by dkim_key
Add a # character at the beginning of each line to comment them out.
#$enable_dkim_verification = 1; # enable DKIM signatures verification #$enable_dkim_signing = 1; # load DKIM signing code, keys defined by dkim_key
Save and close the file. Then restart Amavis.
sudo systemctl restart amavisd
Step 1: Install and Configure OpenDKIM on CentOS 8/RHEL8
First enable the EPEL (Extra Packages for Enterprise Linux) repository and install OpenDKIM.
sudo dnf install epel-release sudo dnf install opendkim
Edit OpenDKIM main configuration file.
sudo nano /etc/opendkim.conf
Find the following line.
Mode v
By default, OpenDKIM runs in verification mode (v), which will verify the DKIM signature of incoming email messages. We need to sign outgoing emails, so change this line to the following to enable signing mode.
Mode sv
Then find the following lines.
## Specifies whether or not the filter should generate report mail back ## to senders when verification fails and an address for such a purpose ## is provided. See opendkim.conf(5) for details. SendReports yes ## Specifies the sending address to be used on From: headers of outgoing ## failure reports. By default, the e-mail address of the user executing ## the filter is used ([email protected]). # ReportAddress "Example.com Postmaster" <[email protected]>
When a signature verification fails and the signature included a reporting request (“r=y”) and the signing domain advertises a reporting address (i.e. ra=user) in a reporting record in the DNS, OpenDKIM will send a structured report to that address containing details needed to reproduce the problem. You may want to use a particular From email address to send the report. Uncomment the ReportAddress parameter and change email address. Note that this will not create the backscatter problem, because report emails will sent to an email address specified in the sender domain’s DNS record.
Find the following line and comment it out, because we will use separate keys for each domain name.
KeyFile /etc/opendkim/keys/default.private
Next, find the following 4 lines and uncomment them.
# KeyTable /etc/opendkim/KeyTable # SigningTable refile:/etc/opendkim/SigningTable # ExternalIgnoreList refile:/etc/opendkim/TrustedHosts # InternalHosts refile:/etc/opendkim/TrustedHosts
Save and close the file.
Step 2: Create Signing Table, Key Table and Trusted Hosts File
Edit the signing table file.
sudo nano /etc/opendkim/SigningTable
Add the following line at the end of this file. This tells OpenDKIM that if a sender on your server is using a @your-domain.com address, then it should be signed with the private key identified by 20200308._domainkey.your-domain.com.
*@your-domain.com 20200308._domainkey.your-domain.com
20200308 is the DKIM selector. A domain name might have multiple DKIM keys. The DKIM selector allows you to choose a particular DKIM key. You can use whatever name for the DKIM selector, but I found it’s convienent to use the current date (March 8, 2020) as the DKIM selector. Save and close the file. Then edit the key table file.
sudo nano /etc/opendkim/KeyTable
Add the following line, which specifies the location of the DKIM private key.
20200308._domainkey.your-domain.com your-domain.com:20200308:/etc/opendkim/keys/your-domain.com/20200308.private
Save and close the file. Next, edit the trusted hosts file.
sudo nano /etc/opendkim/TrustedHosts
127.0.0.0.1 and ::1 are included in this file by default. Now add the following line. This tells OpenDKIM that if an email is coming from your own domain name, then OpenDKIM should not perform DKIM verification on the email.
*.your-domain.com
Save and close the file.
Step 3: Generate Private/Public Keypair
Since DKIM is used to sign outgoing messages and verify incoming messages, we need to generate a private key for signing and a public key for remote verifier. Public key will be published in DNS.
Create a separate folder for the domain.
sudo mkdir /etc/opendkim/keys/your-domain.com
Generate keys using opendkim-genkey tool.
sudo opendkim-genkey -b 2048 -d your-domain.com -D /etc/opendkim/keys/your-domain.com -s 20200308 -v
The above command will create 2048 bits keys. -d (domain) specifies the domain. -D (directory) specifies the directory where the keys will be stored. I use 20200308 as the DKIM selector. Once the command is executed, the private key will be written to 20200308.private file and the public key will be written to 20200308.txt file.
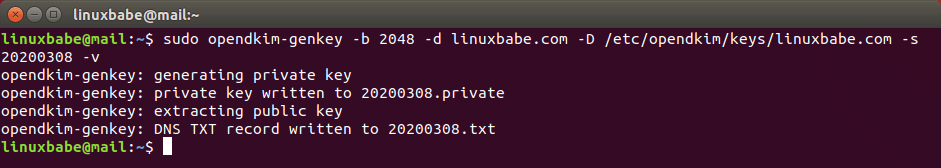
By default, only root can read and write to the key files. Make opendkim as the owner of the private key.
sudo chown opendkim:opendkim /etc/opendkim/keys/ -R
Step 4: Publish Your Public Key in DNS Records
Display the public key
sudo cat /etc/opendkim/keys/your-domain.com/20200308.txt
The string after the p parameter is the public key.
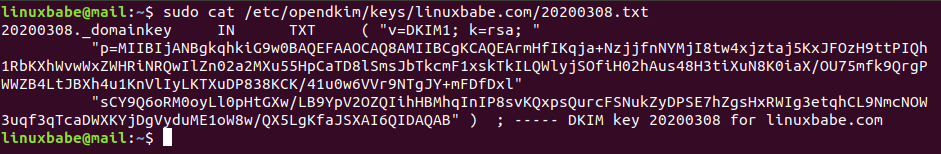
In you DNS manager, create a TXT record, enter 20200308._domainkey in the name field. (You need to replace 20200308 with your own DKIM selector.) Then go back to the terminal window, copy everything in the parentheses and paste it into the value field of the DNS record. You need to delete all double quotes and line breaks in the value field. If you don’t delete them, then key test in the next step will probably fail.
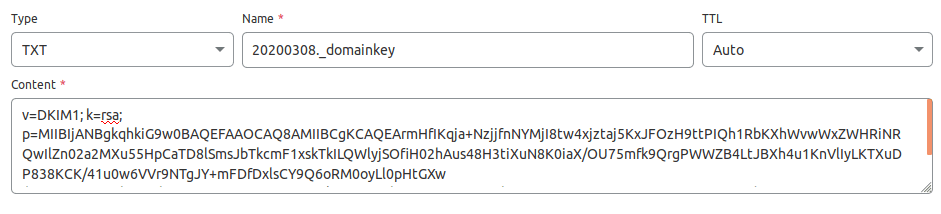
Step 5: Test DKIM Key
Enter the following command on your CentOS 8/RHEL 8 server to test your key.
sudo opendkim-testkey -d your-domain.com -s 20200308 -vvv
If everything is OK, you will see the key OK message.
opendkim-testkey: using default configfile /etc/opendkim.conf opendkim-testkey: checking key '20200308._domainkey.linuxbabe.com' opendkim-testkey: key OK
If you see “Key not secure”, don’t panic. This is because DNSSEC isn’t enabled on your domain name. DNSSEC is a security standard for secure DNS query. Most domain names haven’t enabled DNSSEC. You can continue to follow this guide.
Now we can start the opendkim service.
sudo systemctl start opendkim
And enable auto-start at boot time.
sudo systemctl enable opendkim
OpenDKIM listens on 127.0.0.1:8891.
Step 6: Connect Postfix to OpenDKIM
Edit Postfix main configuration file.
sudo nano /etc/postfix/main.cf
Add the following lines at the end of this file, so Postfix will be able to call OpenDKIM via the milter protocol. Note that you should use 127.0.0.1 as the address. Don’t use localhost.
# Milter configuration milter_default_action = accept milter_protocol = 6 smtpd_milters = inet:127.0.0.1:8891 non_smtpd_milters = $smtpd_milters
Save and close the file. Then add postfix user to opendkim group.
sudo gpasswd -a postfix opendkim
Restart postfix service.
sudo systemctl restart postfix
Step 7: SPF and DKIM Check
Now you can use your desktop email client or webmail client to send a test email to [email protected] and get a free email authentication report. Here’s the report I got from port25.com.

You can also send a test email from your mail server to your Gmail account to see if SPF and DKIM checks are passed. On the right side of an opened email message in Gmail, if you click the show original button from the drop-down menu, you can see the authentication results.
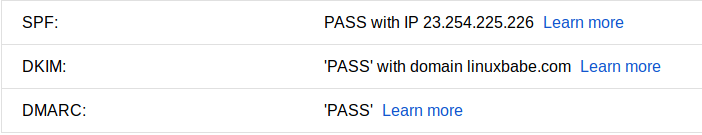
If your message is not signed and DKIM check failed, you may want to check postfix log (/var/log/maillog) to see what’s wrong in your configuration.
Your email server will also perform DKIM verification on incoming emails. You can see the results in the email headers. The following is SPF and DKIM check on a sender using Gmail.
Received-SPF: Pass (mailfrom) identity=mailfrom; client-ip=2607:f8b0:4864:20::c2d; helo=mail-yw1-xc2d.google.com; [email protected]; receiver= Authentication-Results: email.linuxbabe.com; dkim=pass (2048-bit key; unprotected) header.d=gmail.com [email protected] header.b="XWMRd2co"; dkim-atps=neutral
How to Configure OpenDKIM For Multiple Domains
I have written a guide to hosting multiple domains on CentOS 8/RHEL 8 mail server with PostfixAdmin. In that article, I used Amavis for DKIM signing and verification. I you use OpenDKIM, then you need to skip step 3 in that article.
To configure OpenDKIM for multiple domains, you need to add the other domains in the signing table, key table and trusted hosts file like below.
Signing table:
*@domain1.com 20200308._domainkey.domain1.com *@domain2.com 20200308._domainkey.domain2.com
Key table:
20200308._domainkey.domain1.com domain1.com:20200308:/etc/opendkim/keys/domain1.com/20200308.private 20200308._domainkey.domain2.com domain2.com:20200308:/etc/opendkim/keys/domain2.com/20200308.private
Trusted hosts:
127.0.0.1 localhost *.domain1.com *.domain2.com
Then generate the DKIM Private/Public keypair and add the DKIM public key in DNS as mentioned in step 3, step 4 and step 5 for other domains. Restart OpenDKIM and you are done.
sudo systemctl restart opendkim
Wrapping Up
I hope this tutorial helped you install and configure OpenDKIM on CentOS 8/RHEL 8 mail server. As always, if you found this post useful, then subscribe to our free newsletter to get more tips and tricks. Take care 🙂
Rate this tutorial
[Total: 0 Average: 0]