DNS Reconnaissance is an information-gathering part for a penetration testing. It is used where penetration testing is being performed. It can gather and collect all types of information on the records and target server. It does not affect any IP addresses; therefore, it is best to use for checking on or disclose the information of any network. This is only possible for those networks or organizations that do not check upon the DNS traffic. So, the types of enumeration that perform include zone transfers reverse lookups domain and host brute force standard record, enumeration, catch snooping, zoom working, and also Google Luca.
Tools:
To gather DNS information, different tools are available. The following are some tools for DNS Reconnaissance.
DNSRecon:
It is used to gather DNS information and was developed by a python script.
NMAP:
This tool is also available in kali, and you can download it from the following link
Maltego:
This tool is not available for free. It was developed by Paterva and is used for open-source intelligence and forensics.
DNSEnum:
This tool is used to enumerate DNS information and to discover non-contiguous IP blocks.
Fierce:
It can automatically transfer to Brute-force from DNS zone transfer. Online tools are also available like DNSdumpster.com but have a limitation to 100 domains only.
Techniques:
Perform DNS zone transfer: the use of this technique can obtain paramount information. However, you cannot use it today because of the implementation of security controls by organizations.
Perform DNS brute force: A file containing a list of names is provided to the tool. By trying each entry in the file tool will resolve the A, AAA, and CNAME records against the domain provided.
Perform a Reverse Lookup: For a given IP range CDIR tool will perform PTR Record lookup.
Zone walking: Internal records are uncovered if the zone is not configured properly. The information allows hackers to map network hosts.
Not all tools can perform the given techniques. Usage of more than one tool is preferred to obtain ideal information.
Step 1 Dig for DNS information:
Dig is a tool to help sort out crazy DNS problems because people do weird things and when you’re trying to set up hosting, you run into the slot. So, let me tell you about the dig. Dig is a simple tool but has a lot of features because DNS has a lot of features, and what dig does is a command-line tool built into Linux by thinking there’s a port you can find for other operating systems. But, it’s a quick way to query directly at different DNS servers to see if there are records that are showing differently from one place to another. Dig is done to get the information about the authoritative name and also to get the server name.
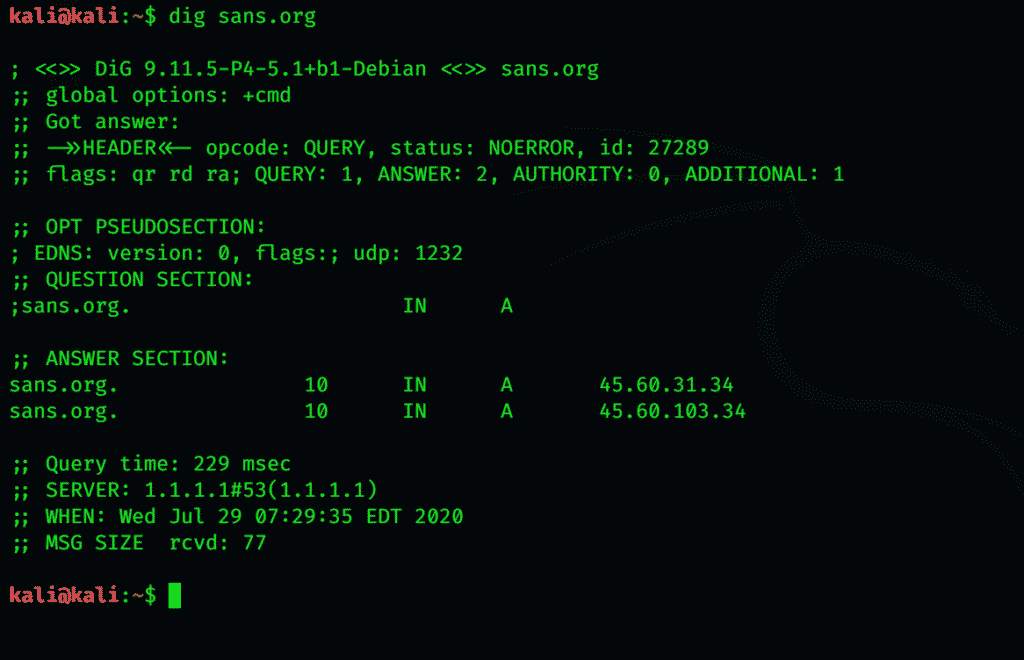
Let’s dig into SANS.
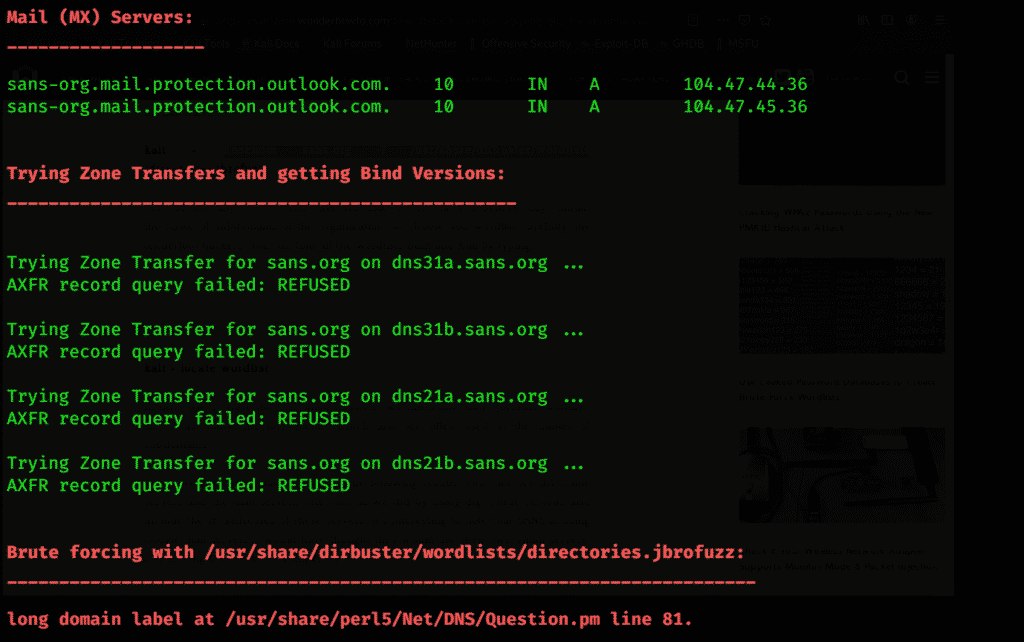
You can see it grabs the IP address of sans.org, i.e., 45.60.31.34
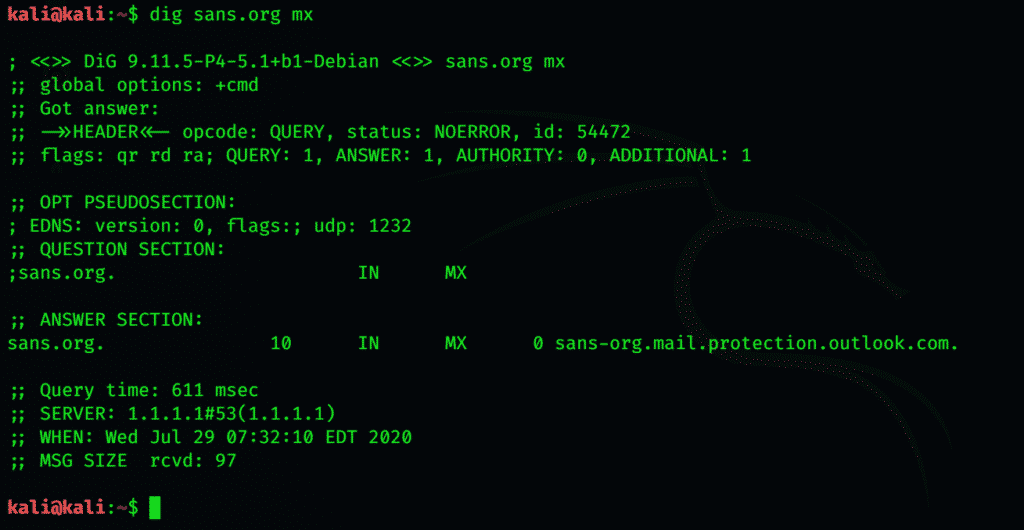
Now if we wish to find their email servers, we simply add mx to the end of command as shown below:
As you can see by using this, we can access email servers that SANS uses if anyone is willing to send anonymous or bulk email.
Step 2 Open Dnsenum
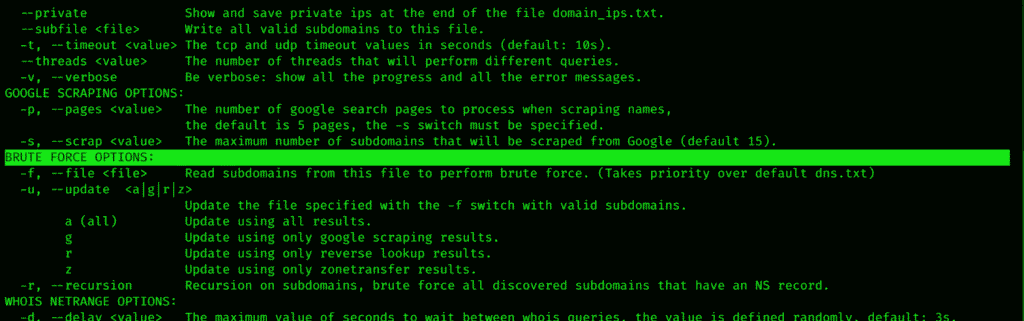
Dnsenum is a tool that kali and Backtrack own that does everything did do and much more. Where to find it? You can find it by approaching DNSenum in the applications.
When you follow the procedure mentioned above, the DNSenum help screen will open as below. DNSEnum finds subdomains that are hidden from the public eye.
Step 3 Run Dnsenum
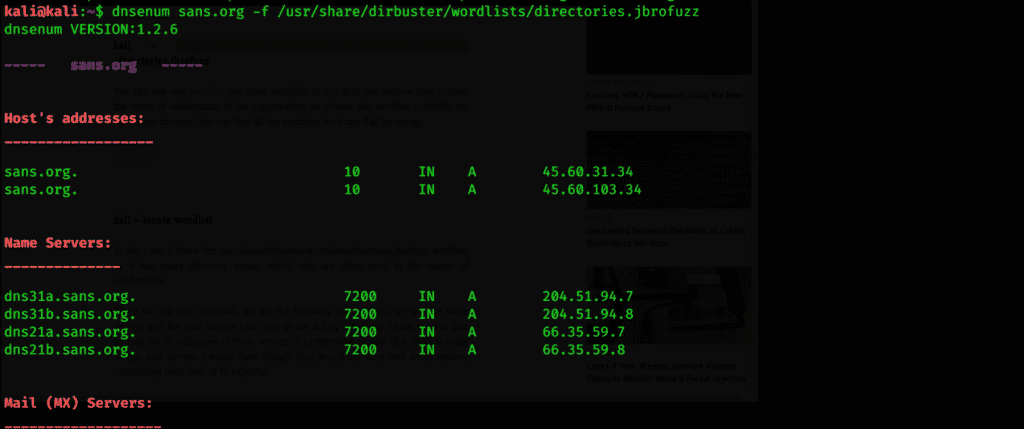
Let’s use this simple yet effective tool against SANS and by querying domain look for any additional information regarding their servers and subdomains. It is important to notice that all this reconnaissance is passive. The victim will never know we are casing their systems because we are not touching their systems at all, just the DNS servers look like normal traffic.
$ dnsenum sans.org -f /usr/share/dirbuster/wordlists/directories.jbrofuzz
You should be really careful while choosing the wordlist. Almost all the subdomains of every organization are mentioned there. It might cause you to face some difficulties.
The next step is to look for subdomains within sans org.
With the help of the DNSenum, we can find subdomains. As mentioned earlier, the wordlist is a crucial part of your success. Generally, subdomain names are simple routine words like training, test, etc.
This process is time-consuming, so it becomes tedious, but you have to remain calm. Wordlist has many benefits. It helps you to find all the hidden information of the servers plus anything that is hidden by you. It will provide you the entire data you have been looking for.
Conclusion
DNS reconnaissance gathers all the information on the server during penetration. The tools of DNS are the best to use on Kali Linux. I hope this brief description of DNS reconnaissance and its tools is enough for you to understand. If it worked for you, you might share it with your friends.
About the author
Younis Said
I am a freelancing software project developer, a software engineering graduate and a content writer. I love working with Linux and open-source software.