Introduction
Last time, we covered 14 forensic tools that are present in Kali Linux and explained their purpose and special capabilities. Today, we are going to present 14 forensic tools, which are from a famous library, “The Sleuth Kit” (TSK), packaged inside the 2020 update of Kali Linux. You can find these tools in Forensics drop-down list under the name Sleuth Kit Suite tools in Kali Whisker Menu.
blkcalc
The blkcalc tool is a forensic tool that converts unallocated disk points to regular disk points. This program creates a point number that maps two images. One of these images is normal, and the other contains unallocated point numbers of the first image. This tool can support many file system types. If a file system is not defined at the start, blkcalc has the unique feature of autodetection methods to find the file system type.
tsk_comparedir
With the help of the tsk_comparedir tool, the contents of the image are compared to the contents of the comparison directory. This is the best tool in the testing phase for identifying rootkits (malicious code or files). The rootkit test is performed by comparing the contents of the local directory to a local raw device. These rootkits are not hidden when accessed and read from a raw device.
tsk_gettimes
The tsk_gettimes forensic tool is based on a sleuth kit library. This tool collects the MAC times (pieces of file system metadata) from a specified disk image and converts the times into a body file. The tsk_gettimes tool examines every file system in a disk partition or image and processes the data inside. The output of this tool is the disk image data in a MAC time body format, which can then be used as an input to the system to generate a chronology of the file activity. The data is then printed as a file through the STDOUT command.
blkcat
The blkcat tool is a quick and efficient forensic tool packaged inside Kali. The purpose of this tool is to display the contents of the data stored in a file system’s disk image. The output displays the number of data units, starting with the unit’s main address and prints, into different formats that can be specified and sorted. By default, the output format is raw, and it is also called dcat.
tsk_loaddb
The tsk_loaddb tool loads the metadata from the disk image into an SQLite database, which is a usable database for analysis by other software tools. The database is stored in the image directory for easy access. This tool supports many file systems and can calculate the MD5 hash value for every file.
blkstat
The sleuth kit tool blkstat displays all the information concerning the data units of a file system. This tool returns data about the allocation status of a block or a sector of a file system. This tool can use the addr command, which shows the stats of a piece of data, and is also called dstat.
ffind
The ffind tool uses an inode to search for the name of directory or file in a disk image. The files assigned to an inode file identifier on a disk partition have names; by default, this tool will only return the first name it finds. The ffind tool can even find deleted file names, which is the special capability of this tool. In addition, the ffind tool can also find multiple file names.
hfind
The hfind tool searches for hash values in hash databases. The hash values are searched using the binary search algorithm. The purpose of using this algorithm is to allow users to easily create hash databases and quickly identify a file, whether it is known or unknown. This tool uses the NSRL library and returns md5sum. This tool is very efficient, as it creates an index file that is already sorted and has fixed length entries, which makes searching very fast.
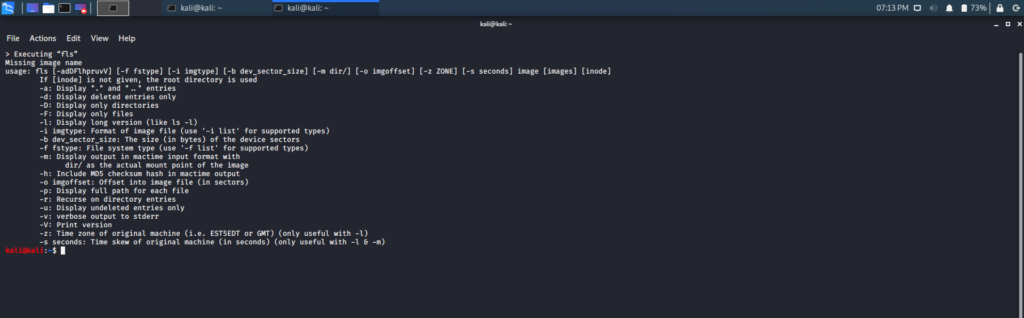
fls
The name fls involves the term “ls,” which stands for listing out the content of a folder. The fls tool lists all the file names and directories in an image file, and can even show names of files that were recently removed. If the file identifier or inode is not used, then the root directory is used.
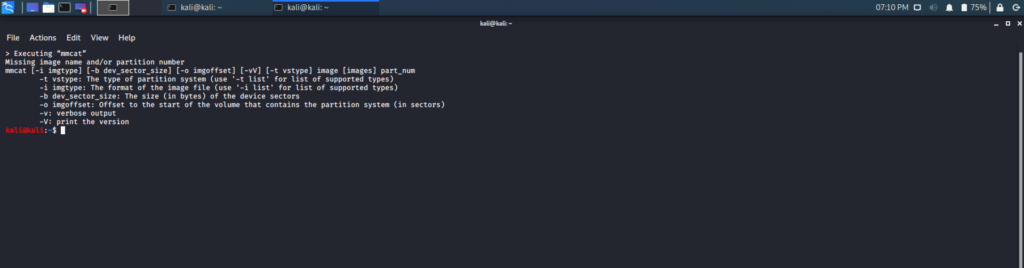
mmcat
The mmcat tool is a forensic tool that returns the contents of a partition through the print function. This tool extracts all the data in a partition into a separate file.
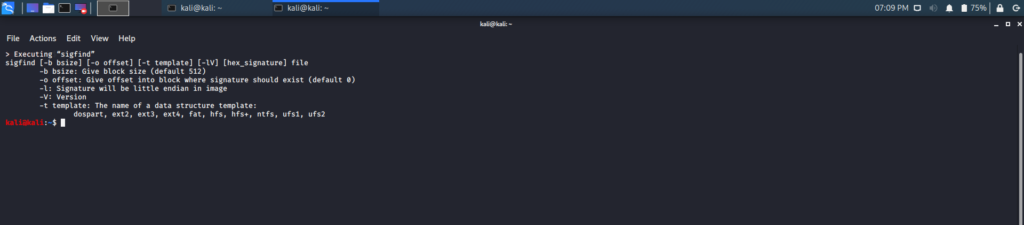
sigfind
This tool finds the binary signature present inside a file. This binary signature is called hex_signature, which is present in each file. This tool can be used to find lost superblocks, partitions or image tables, and boot sectors. The hexadecimal format should be used to find the binary signature.
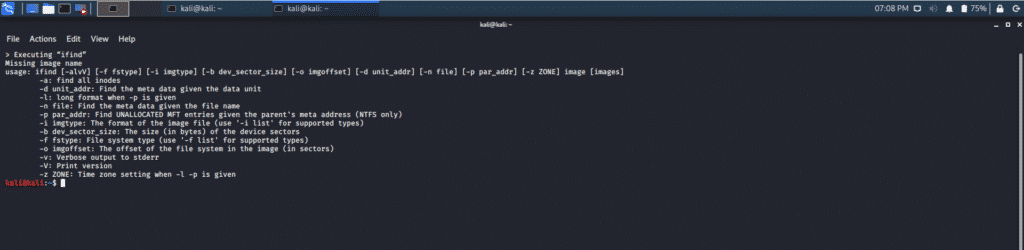
ifind
This tool looks up the raw data structure of a file, which is allocated in a specific disk unit or file name. Sometimes any of these meta-data structures can be unallocated, but this tool will still obtain the results.
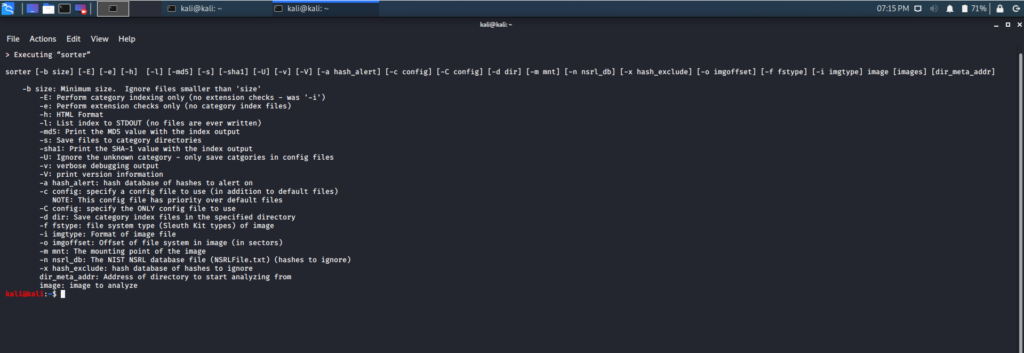
sorter
The sorter tool is a “perl” script tool that performs sorting on a file system to arrange it into allocated and unallocated files, based on the file type. This tool runs a command on every file and sorts the files according to the configuration files. File types include hidden files, hash files for hash databases, files known to be good, and those that should be changed. The configuration files used, by default, are taken from where the tool is installed, but this can be changed with run-time decisions.
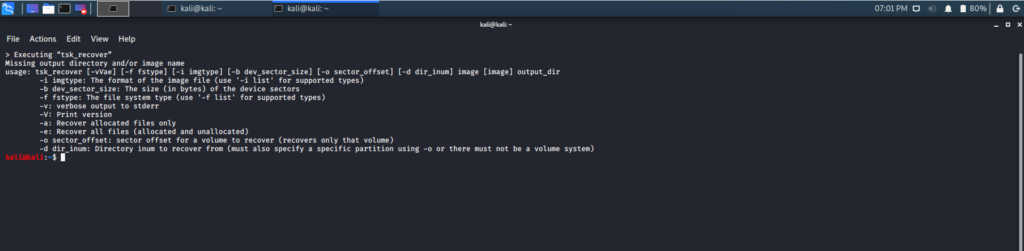
tsk_recover
This tool transfers files from a disk partition into a local root directory. The recovered files are, by default, unallocated files only. Through certain commands, all files can be exported.
Conclusion
These 14 tools come with Kali Linux live, as well as installer images, and they are open-source and freely available. These tools can be found in the Kali whisker menu in a folder named Sleuth Kit Suite. The tools receive frequent updates from TSK for minor bug fixes.
About the author
Younis Said
I am a freelancing software project developer, a software engineering graduate and a content writer. I love working with Linux and open-source software.