Open System Interconnect (OSI) model works as a guide for developers and vendors to create interoperable and secure software solutions.
This model describes the intricacies of how data flows in a network, communication protocols such as TCP, and differences between tools and technologies.
Although many argue the relevance of the OSI model layers, it indeed is relevant, especially in the age of cybersecurity.
Knowing the OSI model layers will help you gauge the technical vulnerabilities and risks associated with applications and systems. It can also help teams identify and distinguish data’s location and physical access and define their security policy.
In this article, we will dig deeper into OSI model layers and explore their importance for users and businesses alike.
What Is Open System Interconnect (OSI) Model?
Open System Interconnect (OSI) model is a reference model consisting of seven layers used by computer systems and applications to communicate with other systems over a network.
The model breaks down data transmission processes, standards, and protocols into seven layers, where each of them performs some specific tasks related to data sending and receiving.
The OSI model was developed by the International Organization for Standardization (ISO) in 1984 and is the first standard reference to establish how systems must communicate in a network. This model was adopted by all leading telecommunication and computer companies.
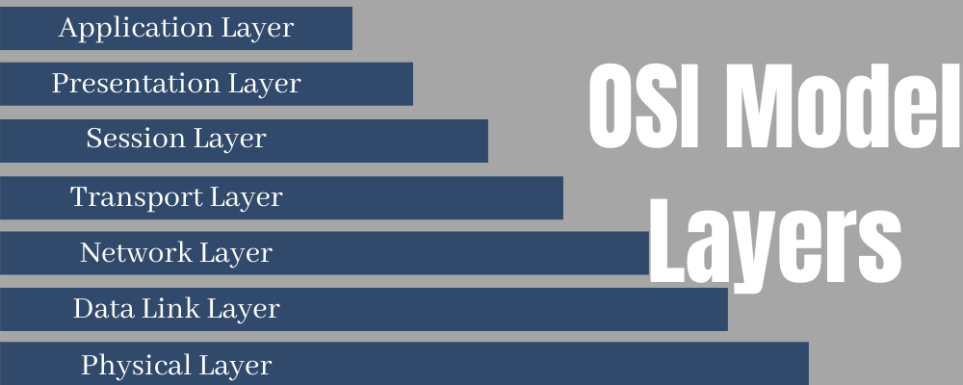
The model represents a visual design where the seven layers are placed on top of one another. In the OSI model architecture, the lower layer serves the upper layer. So, when users interact, data flows down through these layers across the network, beginning from the source device and then goes upwards through the layers to reach the receiving device.
The OSI model includes various applications, networking hardware, protocols, operating systems, etc., to enable systems to transmit signals via physical mediums like fiber optics, twisted-pair copper, Wi-Fi, etc., in a network.
This conceptual framework can help you understand the relationships between systems and aims to guide developers and vendors in creating interoperable software applications and products. In addition, it promotes a framework describing the functioning of telecommunications and networking systems in use.
Why Do You Need to Know the OSI Model?
Understanding the OSI model is important in software development since each application and system work on the basis of one of these layers.
IT networking professionals leverage the OSI model to conceptualize how data flows over a network. This knowledge is valuable not only for software vendors and developers but also for students who want to clear exams like Cisco Certified Network Associate (CCNA) certification.
Some of the advantages of learning the OSI model layers are:
- Understanding data flow: The OSI model makes it easy for network operators to understand how data flows in a network. This helps them understand how the hardware and software are working together. Using this information, you can build a better system with enhanced security and resilience using suitable software and hardware.
- Easy troubleshooting: Troubleshooting the issues becomes easier because the network is divided into seven layers with their own functionalities and components. Also, it takes less time for professionals to diagnose the problem. You can actually identify the network layer responsible for causing the issues so that you can shift your focus on that particular layer.
- Promotes interoperability: Developers can create software systems and devices that are interoperable so that they can easily interact with products from other vendors. This increases the functionality of those systems and empowers the users to work efficiently.
You can define which components and parts with which their products must work. This also enables you to communicate to end-users the network layer at which your products and systems operate, whether across the tech stack or only at a particular layer.
Different OSI Model Layers
Physical Layer
The physical layer is the bottom-most and first layer in the OSI model that describes the physical and electrical representation of a system.
It may include the type of cable, pin layout, radio frequency link, voltages, signal type, connectors type to connect the devices, and more. It is responsible for a wireless or physical cable connection between different network nodes, facilitates raw data transmission, and controls bit rates.
In this layer, raw data in bits or 0’s and 1’s convert into signals and are exchanged. It requires the sender and receiver ends to be synchronized to enable smooth data transmission. The physical layer provides an interface between different devices, transmission media, and topology types for networking. The transmission mode type required is also defined at the physical layer.
The networking topology used can be bus, ring, or star, and the mode could be simplex, full-duplex, or half-duplex. Devices at the physical layer can be Ethernet cable connectors, repeaters, hubs, etc.
If a networking issue is detected, networking professionals first check whether everything in the physical layer is working fine. They may start with checking the cables if they are connected properly and if the power plug is connected to the system, such, as or router, among other steps.
The main functions of layer-1 are:
- Defining physical topologies, the way devices and systems are arranged in a given network
- Defining transmission mode is how data flows between two connected devices in the network.
- Bit synchronization with a clock that controls receiver and sender at bit level.
- Controlling bit rate of data transmission
Data Link Layer
The data link layer is above the physical layer. It is used to establish and terminate connections between two connected nodes present in a network. This layer divides data packets into different frames, which then go from source to destination.
The data link layer has two parts:
- Logical Link Control (LLC) detects network protocols, synchronizes frames, and checks errors.
- Media Access Control (MAC) utilizes MAC addresses to link devices and set permissions to transmit data.
MAC addresses are unique addresses assigned to each system in a network that helps identify the system. These 12-digit numbers are physical addressing systems supervised at the data link layer for a network. It controls how assorted network components are accessed to a physical medium.
Example: MAC addresses can comprise 6 octets, such as 00:5e:53:00:00:af, where the first three numbers correspond to the organizationally unique identifiers (OUI) while the last three correspond to the Network Interface Controller (NIC).
The main functions of the layer-2 are:
- Error detection: error detection happens at this layer but not error correction, which occurs at the transport layer. In some cases, unwanted signals called error bits are found in the data signals. To counteract this error, the error must be detected first through methods such as checksum and cyclic redundancy check (CRC).
- Flow control: Data transmission between the receiver and the sender over a media must happen at the same speed. If the data as a frame is sent at a faster pace than the speed at which the receiver is receiving the data, some data might be lost. To solve this issue, the data link layer involves some flow control methods so that consistent speed is maintained across the data transmission line. These methods could be:
- The sliding window method where both the ends will decide how many frames must be transmitted. It saves time and resources during transmission.
- The stop-and-wait mechanism requires the sender to stop and start waiting for the receiver after data gets transmitted. The sender must wait till it receives an acknowledgment from the receiver that they have received the data.
- Enable multiple access: The data link layer also allows you to access multiple devices and systems to transmit data via the same transmission media with no collision. For this, it uses carrier sense multiple access or collision detection protocols (CSMA/CD).
- Data syncing: In the data link layer, the devices sharing data must be in sync with one another at each end to facilitate smooth data transmission.
The data link layer also leverages devices such as bridges and layer-2 switches. Bridges are 2-port devices connecting to different LAN networks. It works as a repeater, filters unwanted data, and sends it to the destination endpoint. It connects networks using the same protocol. On the other hand, Layer-2 switches forward data to the subsequent layer based on the system’s MAC address.
Network Layer
The network layer sits on top of the data link layer and is the third one from the bottom of the OSI model. It utilizes network addresses such as IP addresses in order to route data packets to a receiving node operating on different or the same protocols and networks.
It performs two main tasks:
- Divides network segments into different network packets while reassembling the network packers on the destination node.
- Discovers the optimum path in a physical network and routes packets accordingly.
By optimum path, I mean that this layer finds the shortest, most time-efficient, and the easiest route between a sender and receiver for data transmission using switches, routers, and various error detection and handling methods.

In order to do that, the network layer uses a logical network address and the network’s subnetting design. Whether the devices are on the same network or not, use the same protocol or not, and work on the same topology or not, this layer will route the data using a logical IP address and router from a source to a destination. So, its main components are IP addresses, subnets, and routers.
- IP address: It is a globally unique 32-bit number assigned to each device and works as a logical network address. It has two parts: host address and network address. An IP address is typically represented by four numbers separated by a period, for instance, 192.0.16.1.
- Routers: In the network layer, routers are used to communicate data between devices operating in different wide area networks (WANs). Since routers used for data transmission don’t know the exact destination address, the data packets are routed.
They only have information about their network’s location and leverage data collected in the routing table. This helps the routers find the path to deliver the data. When it finally delivers the data to the destined network, the data will then be sent to the destination host in the network.
- Subnet masks: A subnet mask consists of 32 bits of the logical address that a router can use aside from an IP address to discover the destination host’s location to deliver the data. It is important since the host and network addresses are not enough to find the location, whether it lies in a remote network or sub-network. An example of a subnet mask could be 255.255.255.0.
By looking at a subnet mask, you can find out the network address and host address. So, when a data packet arrives from the source with the destination address calculated, the system will receive the data and transmit it to the next layer. This layer does not require the sender to wait for the receiver’s acknowledgment, unlike layer-2.
Transport Layer
The transport layer is the fourth one from the bottom in the OSI model. It takes data from the network layer and delivers it to the application layer. In this layer, the data is called “segments,” and the layer’s primary function is to deliver the complete message. It also acknowledges when data transmission takes place successfully. If there’s any error, it returns the data.
Apart from this, the transport layer performs data flow control, transmits data at the same speed as that of the receiving device to enable smooth transmission, manages errors, and requests data again after finding errors.

Let’s understand what happens at each end:
- At the sender’s end, upon receiving the formatted data from the higher layers in the OSI model, the transport layer performs segmentation. It then implements flow and error control techniques to enable smooth data transmission. Next, it will add the port numbers of the source and destination in the header and ends the segments to the Network Layer.
- At the receiver’s end, the transport layer will identify the port number by looking at the header and then sends the received data to the targeted application. It will also sequence and reassemble the segmented data.
The transport layer provides an error-free and end-to-end connection between devices or hosts in a network. It supplies data segments of intra and inter sub-networks.
To enable end-to-end communication in a network, each device must have a Transport Service Access Point (TSAP) or port number. This will help the host recognize the peer hosts by the port number at a remote network. It is generally found manually or by default since most apps use a default port number of 80.
The transport layer utilizes two protocols:
- The transmission control protocol (TCP): This reliable protocol first establishes the connection between the hosts before starting the data transmission. It requires the receiver to send the acknowledgment of whether it has received the data or not. On it receives the acknowledgment, it sends the second batch of data. It also monitors the transmission speed and flow control and corrects errors.
- User Datagram Protocol (UDP): It is considered unreliable and is not connection-oriented. After data transits between the hosts, it doesn’t require the recipient to send the acknowledgment and keeps sending data. This is why it’s prone to cyberattacks such as UDP flooding. It is used in online games, video streaming, etc.
Some functions of the transport layer are:
- Addresses the service points: The transport layer has an address called the port address or service point address that helps deliver a message to the right receiver.
- Error detection and control: This layer offers error detection and control. An error can occur while the segment or data is stored in the memory storage of the router, even if no errors are caught while the data moves through a link. And if an error occurs, the data link layer won’t be able to detect it. In addition, all the links might not be secure; hence, the need for error detection at the transport layer is needed. It is done via two methods:
- Cyclic redundancy check
- Checksum generator and checker
Session Layer
The fifth layer from the bottom of the OSI model is the session layer. It is used to create communication channels, also known as sessions, between different devices. It performs tasks such as:
- Opening sessions
- Closing sessions
- Keeping them open and fully functional when data transmission is happening
- Offering dialogue synchronization between different applications to promote seamless data transmission without loss at the receiving end.
The session layer can create checkpoints to ensure safe data transfer. In case the session gets interrupted, all the devices will resume the transmission from their last checkpoint. This layer allows users using different platforms to create active communication sessions between them.
Presentation Layer
The sixth layer from the bottom is the presentation layer or translation layer. It is used to prepare the data to be sent to the application layer sitting above. It presents data to the end-users that users can easily understand.
The presentation layer describes how two devices in a network must compress, encrypt, and encode data to be received correctly by the receiver. This layer uses data that the application layer transmits and then sends to the session layer.
The presentation layer handles the syntax since the sender and receiver can use different modes of communication, which can lead to inconsistencies. This layer enables systems to easily communicate and understand each other on the same network.
The layer-6 performs tasks such as:
- Encrypting data at the sender’s side
- Decrypting data at the receiver’s side
- Translation, such as ASCII format to EBCDIC
- Compressing data for multimedia before the transmission
The layer splits data containing characters and numbers into bits and then transmits it. It also translates data for a network in the required format and for different devices like smartphones, tablets, PCs, etc., in an accepted format.
Application Layer
The application is the seventh and the topmost layer in the OSI model. End-user software and applications like email clients and web browsers use this layer.
The application layer provides protocols allowing the software systems to transmit data and supply meaningful information to the end-users.
Example: Application layer protocols can be the famous Hypertext Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), Domain Name System (DNS), File Transfer Protocol (FTP), and more.
TCP/IP vs. OSI Model: Differences
The key differences between TCP/IP and the OSI model are:
- The TCP/IP, created by the US Department of Defense (DoD), is an older concept than the OSI model.
- The TCP/IP functional model was built to solve specific communication problems and is based on standard protocols. The OSI model, on the other hand, is a generic model which is protocol-independent that is used to define network communications.
- The TCP/IP model is more straightforward and has fewer layers than the OSI model. It has four layers, typically:
- The network access layer, which combines the OSI layers 1 and 2.
- The Internet layer, which is called the network layer in the OSI model
- Transport layer
- Application layer, which combines OSI layers 5,6, and 7.
- The OSI model has seven layers: the physical layer, data link layer, network layer, transport layer, session layer, presentation layer, and application layer.
- Applications using TCP/IP utilize all the layers, but in the OSI model, most applications don’t utilize all its seven layers. In fact, layers 1-3 are only mandatory for data transmission.
Conclusion
Knowing about the OSI model can help developers and vendors create software applications and products that are interoperable and secure. It will also help you differentiate between different communication tools and protocols and how they work with each other. And if you are a student aspiring to clear a networking exam like CCNA certification, knowing about the OSI model will be beneficial.



