There are many challenges that hackers face, but to deal with reconnaissance is one of the most prominent issues. It is important to know about the target system(s) before beginning to hack. It is essential to know about certain details, like which ports are open, what services are currently running, what the IP addresses are, and which operating system is employed by the target. To begin the hacking process, it is necessary to have all this information. In most cases, hackers will take extra time in reconnaissance instead of exploiting immediately.
The tool used for this purpose is called Nmap. Nmap starts by sending crafted packets to the targeted system. It will then see the system’s response, including which operating system is running, and what ports and services are open. But sadly, neither a good firewall nor a strong network intrusion detection system will easily detect and block such types of scans.
We will discuss some of the best methods to help in carrying out stealthy scans without being detected or blocked. The following steps are included in this process:
- Scan using the TCP Connect protocol
- Scan using the SYN flag
- Alternate scans
- Drop below the threshold
1. Scan Using the TCP Protocol
First, begin scanning the network using the TCP connect protocol. The TCP Protocol is an effective and reliable scan because it will open the connection of the target system. Remember that the -P0 switch is used for this purpose. The -P0 switch will restrain the ping of Nmap that is sent by default while also blocking various firewalls.
$ sudo nmap -sT -P0 192.168.1.115
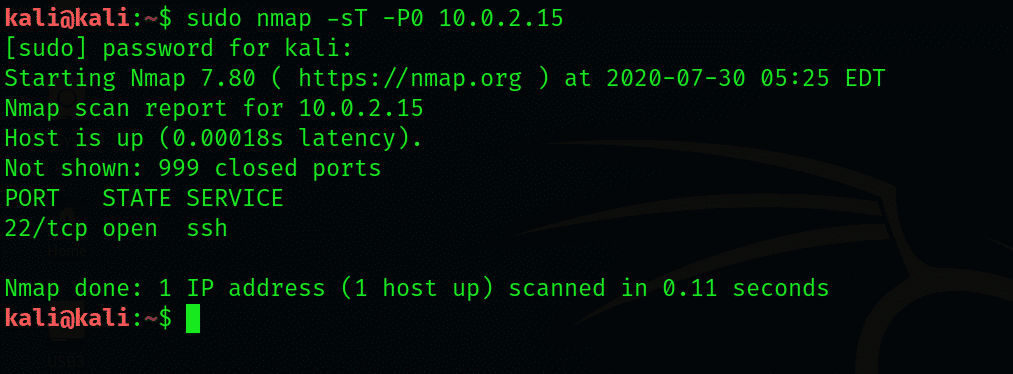
From the above figure, you can see that the most effective and reliable report on the open ports will be returned. One of the main issues in this scan is that it will turn on the connection along the TCP, which is a three-way handshake for the target system. This event may be recorded by Windows security. If by chance, the hack is successful, it will be easy for the system’s admin to know who performed the hack, because your IP address will be revealed to the target system.
2. Scan Using the SYN Flag
The primary advantage of using the TCP scan is that it turns on the connection by making the system more easy, reliable, and stealthy. Also, the SYN flag set can be used along with the TCP protocol, which will never be logged, due to the incomplete three-way handshake. This can be done by using the following:
$ sudo nmap -sS -P0 192.168.1.115
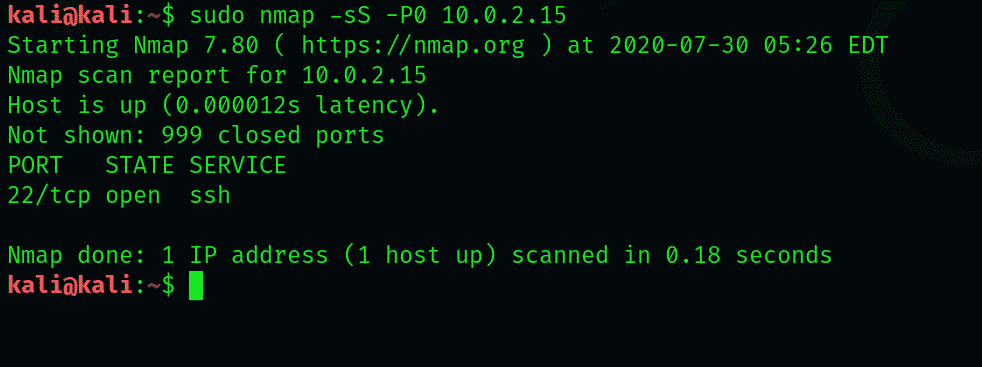
Notice that the output is a list of open ports because it is quite reliable with the TCP connect scan. In the log files, it does not leave any trail. The time taken to perform this scan, according to Nmap, was only 0.42 seconds.
3. Alternate Scans
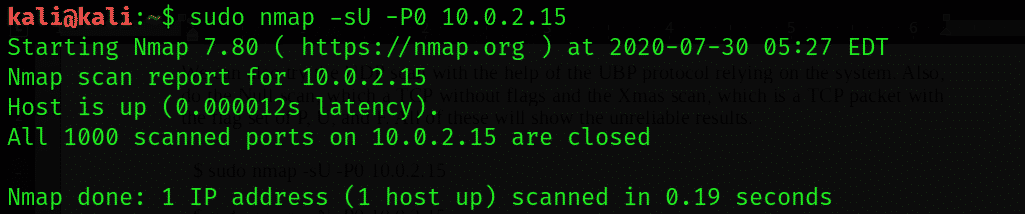
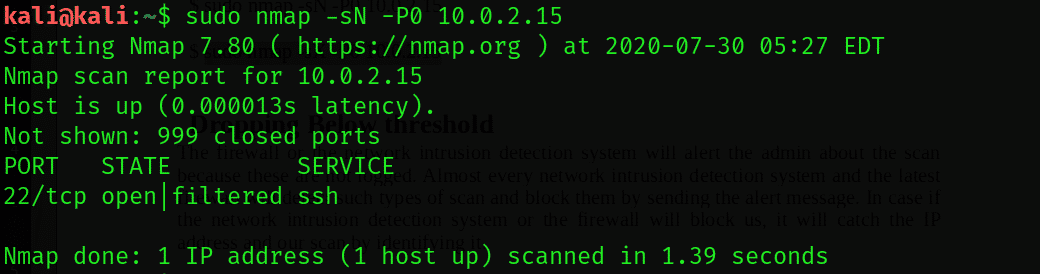
You can also try the UDP scan with the help of the UBP protocol relying on the system. You can also perform the Null scan, which is a TCP without flags; and the Xmas scan, which is a TCP packet with the flag set of P, U, and F. However, all of these scans produce unreliable results.
$ sudo nmap -sU -P0 10.0.2.15
$ sudo nmap -sN -P0 10.0.2.15
$ sudo nmap -sX -P0 10.0.2.15
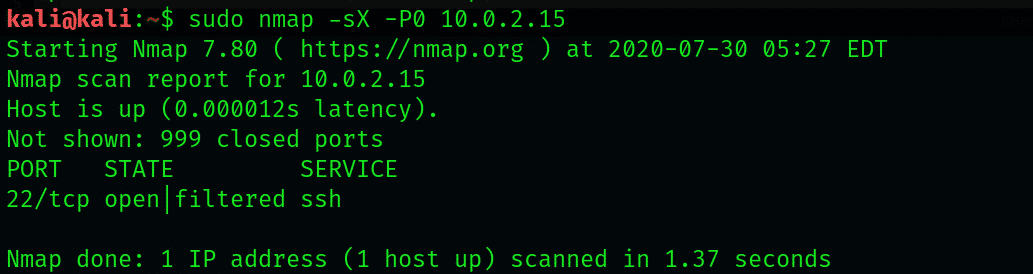
4. Drop Below the Threshold
The firewall or network intrusion detection system will alert the admin about the scan because these scans are not logged. Almost every network intrusion detection system and the latest firewall will detect such types of scans and block them by sending the alert message. If the network intrusion detection system or the firewall blocks the scan, it will catch the IP address and our scan by identifying it.
SNORT is a famous, popular network intrusion detection system. SNORT consists of the signatures that are built on the ruleset for detecting scans from Nmap. The network-set has a minimum threshold because it will go through a greater number of ports each day. The default threshold level in SNORT is 15 ports per second. Therefore, our scan will not be detected if we scan below the threshold. To better avoid the network intrusion detection systems and firewalls, it is necessary to have all the knowledge available to you.
Luckily, it is possible to scan using different speeds with the help of Nmap. By default, Nmap consists of six speeds. These speeds can be changed with the help of the –T switch, along with the speed name or number. The following six speeds are:
paranoid 0, sneaky 1, polite 2, normal 3, aggressive 4, insane 5
The paranoid and sneaky speeds are the slowest, and both are under the threshold of SNORT for various port scans. Use the following command to scan down at the sneaky speed:
$ nmap -sS -P0 -T sneaky 192.168.1.115
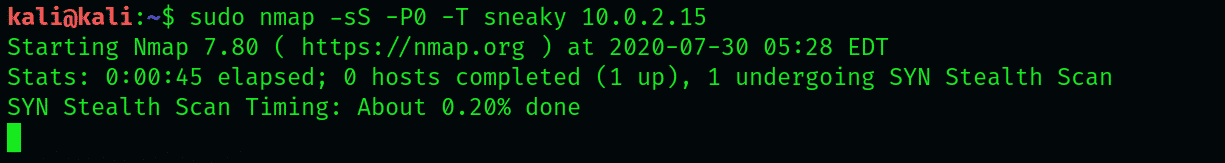
Here, the scan will sail past the network intrusion detection system and the firewall without being detected. The key is to maintain patience during this process. Some scans, like the sneaky speed scan, will take 5 hours per IP address, while the default scan will take only 0.42 seconds.
Conclusion
This article showed you how to perform a stealth scan using the Nmap (Network Mapper) tool in Kali Linux. The article also showed you how to work with different stealth attacks in Nmap.
About the author

Younis Said
I am a freelancing software project developer, a software engineering graduate and a content writer. I love working with Linux and open-source software.



