Nikto is a state of the art web scanner that rigorously forages for vulnerabilities within a website or application and presents a detailed analysis of it, which is used to further the exploitation of that website. It is an open-source utility that is used in many industries all over the world.
One of the distinguishing aspects of Nikto that separates it from other scanners and legitimizes it as strictly a pentester is that it cannot be used stealthily. So a blackhat misusing it is easily detected. And this is very fortunate of us, as Nikto is otherwise a juggernaut that far outdoes its alternatives when it comes to web scanning.
Unlike other web scanners, where the information is presented in a complicated, and almost indecipherable format, Nikto unambiguously calls attention to each and every vulnerability and within the first draft of the report that it presents. This why it is often regarded as industry standard among several whitehat communities around the globe.
Let’s see how we can set up and start pen-testing with Nikto.
1-Setting up Nikto
Check the vulnerability analysis category within Kali Linux to see if it is there; otherwise, you can get Nikto from its GitHub since it is open source or use the apt install command in Kali Linux:
Mac users can use Homebrew to install Nikto:
2-Getting started
Use the –Help to see a detailed guide on all the inputs Nikto can take and what each input does. Recommended for those who’re new to this.
3-The scanning basics
Let’s discuss all the basic syntax we can instruct Nikto with.
Substitute the default IP or hostname with a hostname of your choice:
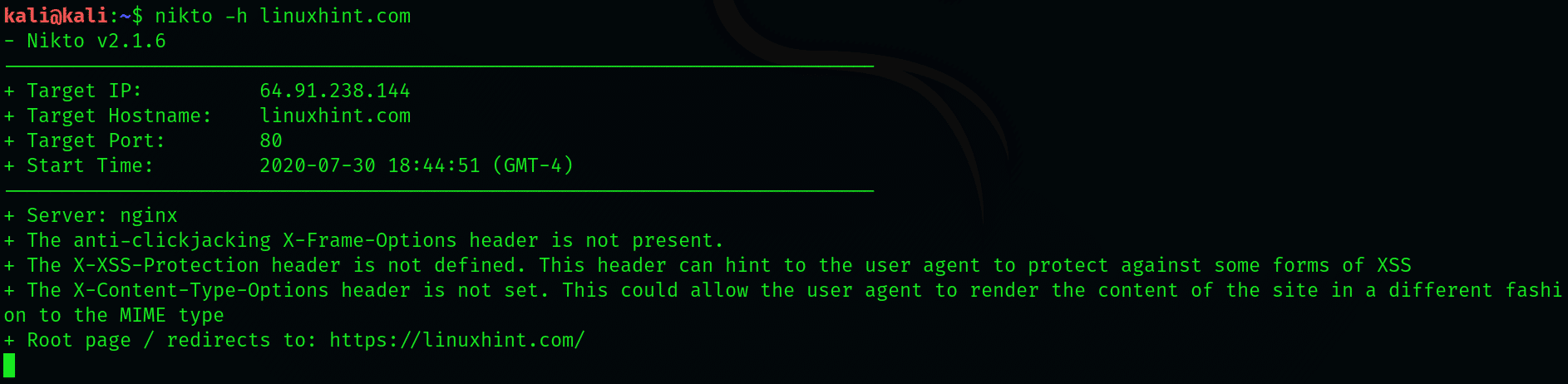
We can perform a basic scan to look for port43 and SSL, which has widespread use in HTTP websites. Although Nikto doesn’t need you to specify the type, specifying helps Nikto save some time with scanning.
To specify an SSL website, use the following syntax
$ nikto -h linuxhint.com -ssl
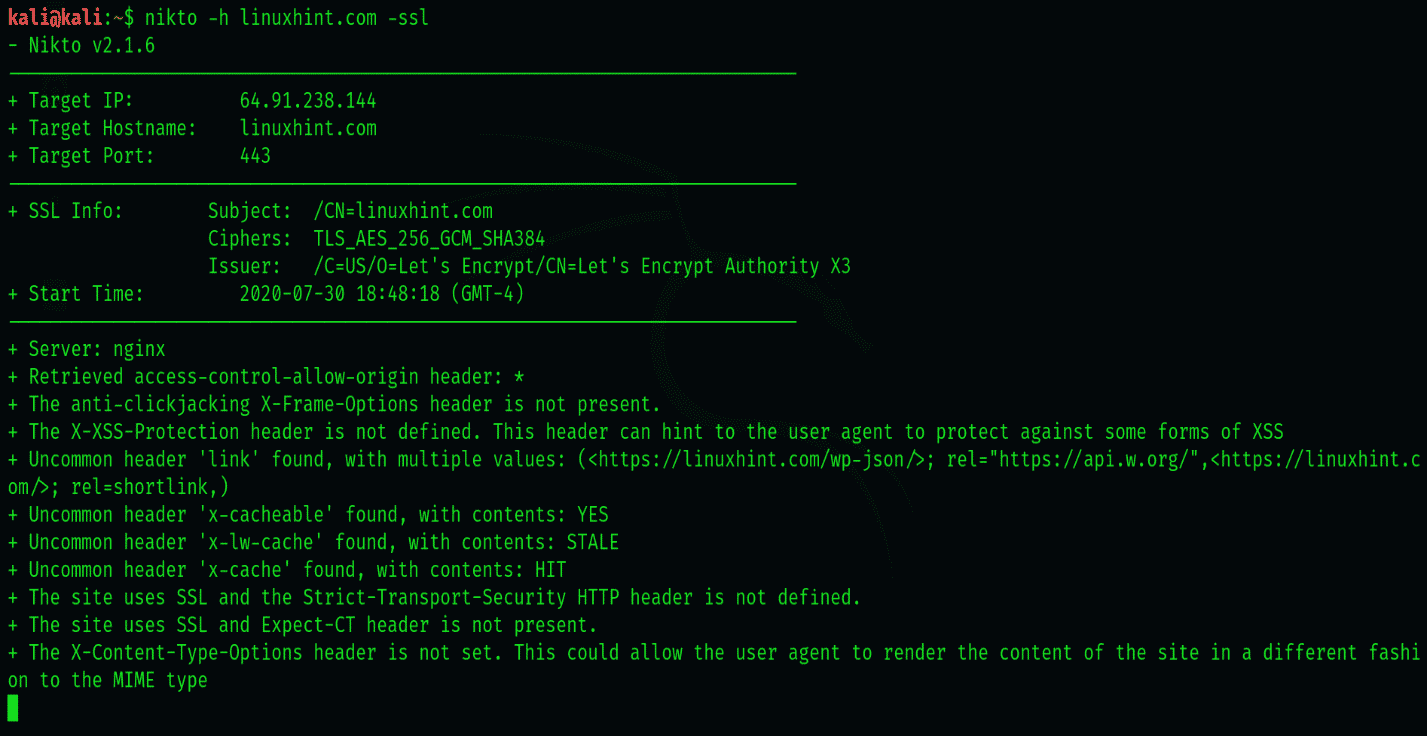
4-Scanning SSL enabled websites with Nikto
Here, we’re scanning pbs.org for demonstration. We shall also learn in this section about the different information Nikto reports once it’s finished with scanning. To initiate scanning, type:
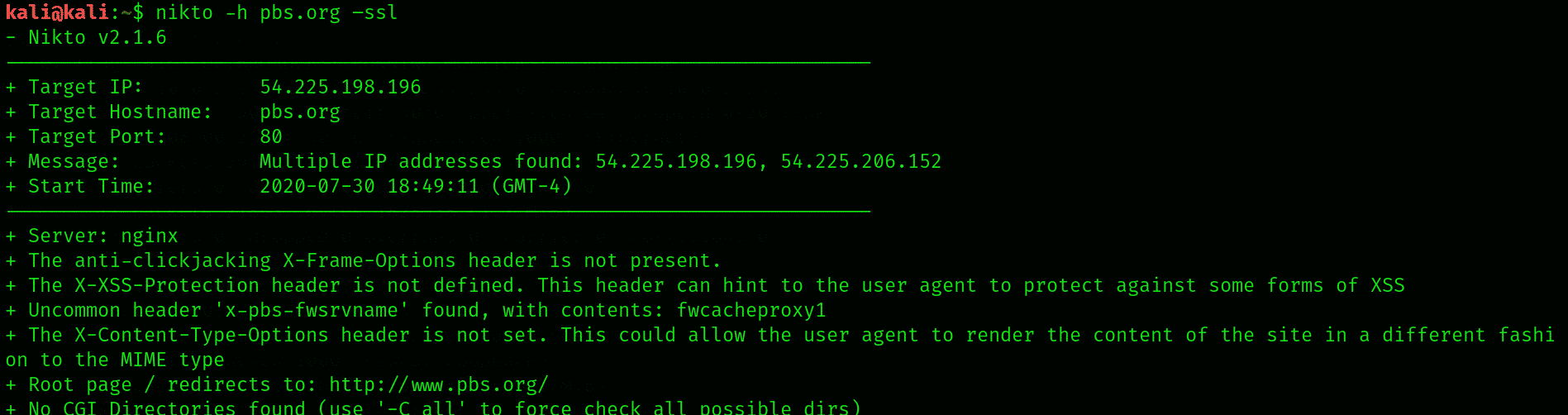
We’ve performed a quick scan of pbs.org
Upon connecting to port 443, it displays some info about the cipher that we can examine. The information here is not very relevant to what we’re trying to do, so we’ll move on to performing more elaborate scans.
5-Scanning IP addresses
Nikto can also be used on the local network to search for any embedded servers. To do that, we’ll need to know our IP address. Type the following in command terminal to see the IP address of your local machine’s use.
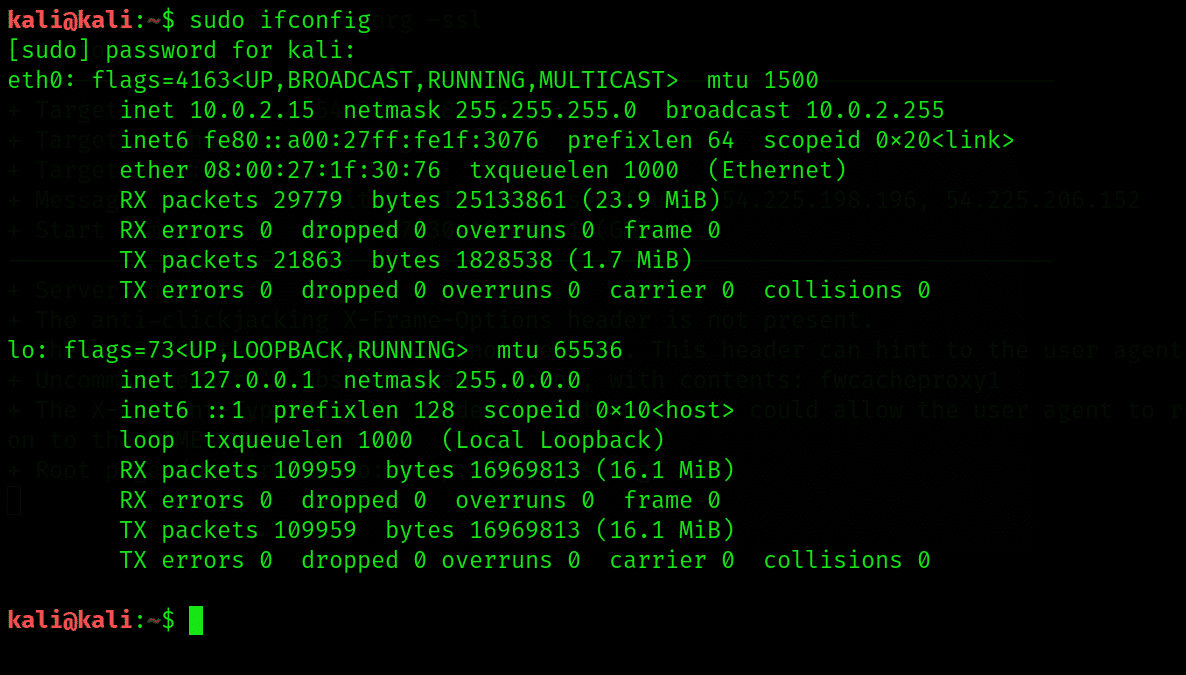
The IP address that we require is the one followed by ‘inet’, so note it down. You can work out your network range by running an ipcalc on it, which you can easily download and install with apt install ipcalc if you don’t have it installed already.
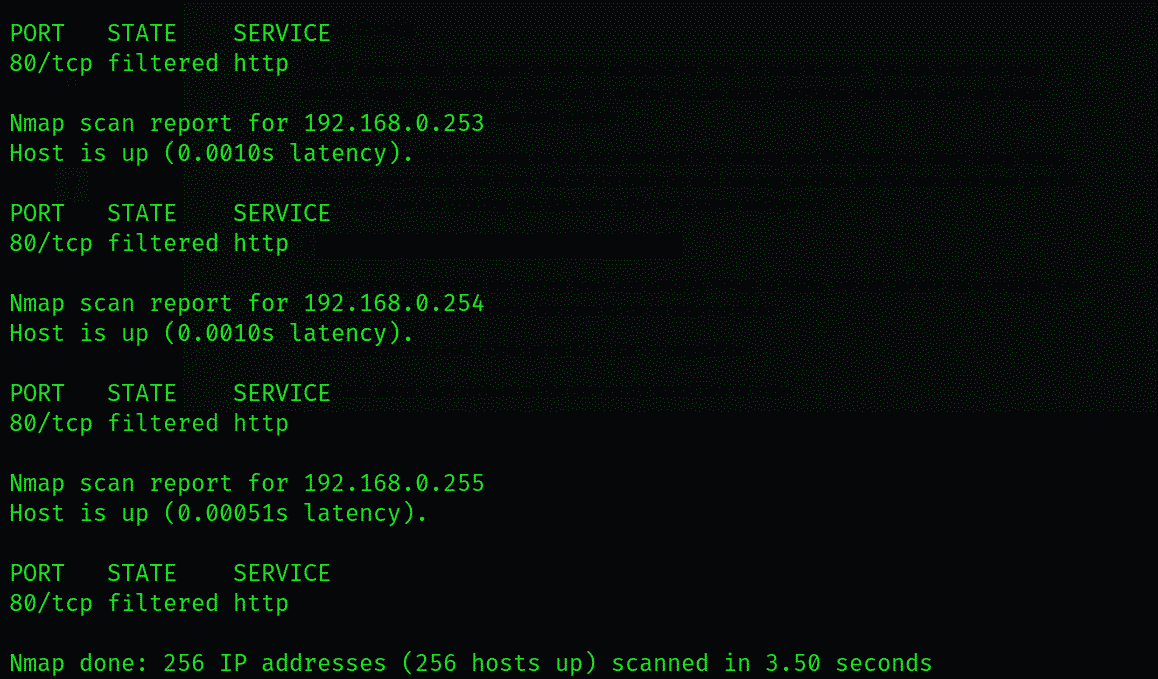
Let’s scan for services running on our local network by scanning port 80 within our range using Nmap. This will extract only the hosts that are currently up and running, as these are the ones with their port 80 open. Here, we’re exporting this data into a file we’ll name nullbye.txt:
$ sudo nmap -p 80 192.168.0.0/24 -oG linuxhint.txt
To forward the list of all the current hosts extracted by Nmap to Nikto, we can use the cat to read the file we exported the info to. Here’s the code to run to do so:
$ cat linuxhint.txt | awk ‘/Up$/{print $2}’ | cat >> targetIP.txt

Let’s talk about each element in the previously stated line of code.
awk– searches for the pattern within the targeted file that follows ‘cat’ in the syntax
Up– about the fact that the host is up
Print $2– means you’re instructing to print out the second word in each line of the .txt file
targetIP.txt is just a file we’re sending our data to, which in your case you can name it whatever you want.
Now we can access our new file, which is targetIP in our case, to see what IP addresses have port 80 open.
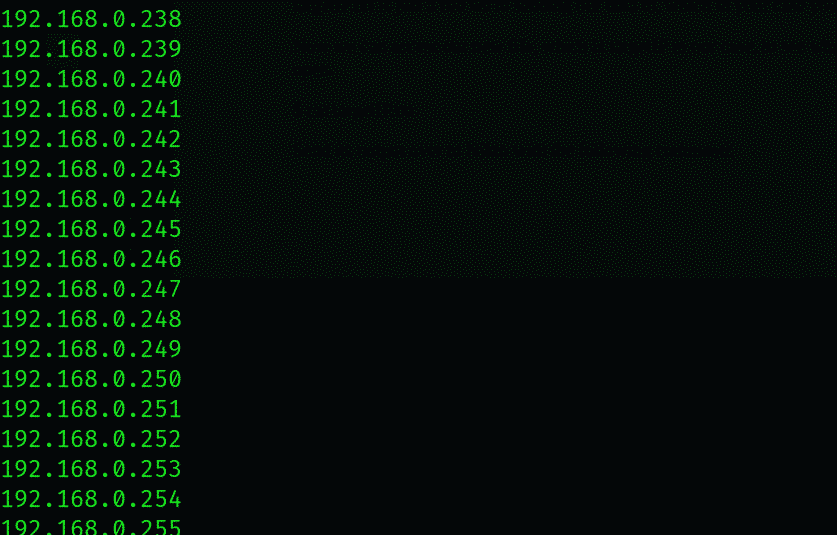
Send its output over to Nikto with the following command:
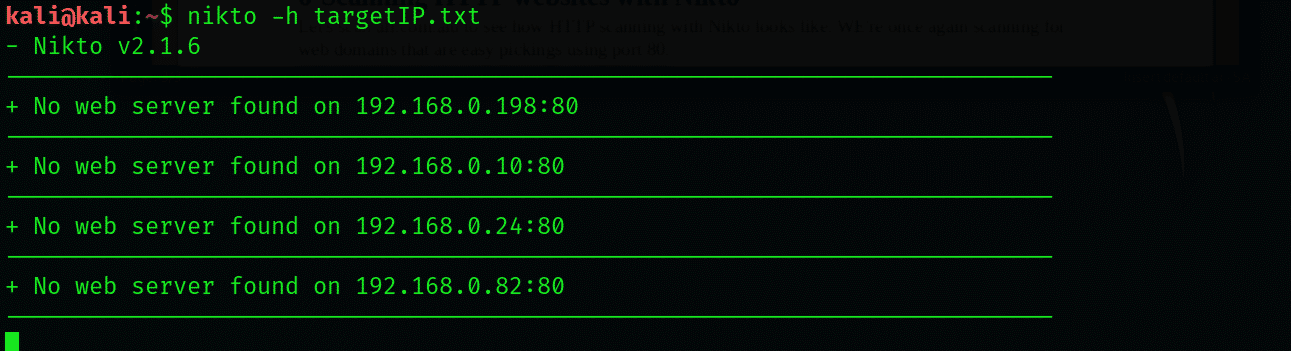
Notice how similar the results here are when compared to those we received in SSL web scanning.
6-Scanning HTTP websites with Nikto
Let’s scan afl.com.alu to see how HTTP scanning with Nikto looks like. WE’re once again scanning for web domains that are easy pickings using port 80.
$ nikto -h www.afl.com.au
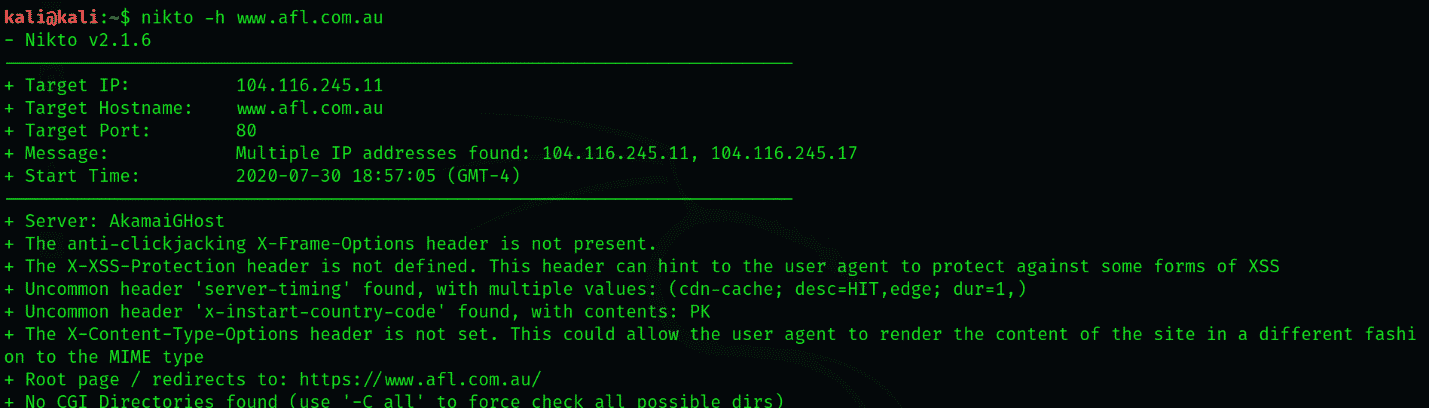
The information herewith most relevant to our users is the directories it has located. We can use these to acquire any user credentials, among other things that were either misconfigured or were unintentionally left open to be accessed.
Coupling Nikto with Metasploit
Once you’re done with web scanning, you’re eventually going to move on to perform the actual pen testing, preferably with Metasploit. So it’s a good thing that Nikto comes with functionality that lets you export information to other reconning tools.
To export information into a format readable by Metasploit, you may perform the scan as we’ve explained above, but add -Format msf after the code, like:
$ nikto -h linuxhint.com -Format msf
![]()
Wrapping things up:
This was a short guide to help you get started with Nikto, the most praised and trusted webscanner among pen-testers. We’ve looked at ways to determine soft spots to test vulnerabilities with nikto and how to export it to Metasploit to perform more accurate exploitation. For its ability to detect over 6700 dangerous files/CGIs, and ability to capture cookies and prints, we recommend novices to explore this intricate tool.
Stick around for the updates and followups and, meanwhile, read some of the other tutorials on pen-testing.
About the author
Younis Said
I am a freelancing software project developer, a software engineering graduate and a content writer. I love working with Linux and open-source software.



