Scams exist for long, very long. Digital scams, since the early days of digital communication.
Not long after the email was invented, email scams emerged. At that time, we all trusted emails, so nobody believed they could become a scam vector. And it proved to be a very effective one. As of 2004, phishing attacks against electronic banking clients increased exponentially. E-banking customers received emails with links conducting them to fake websites with a very real and professional look. Victims fell into the trap, typing in all their account numbers and passwords, and handing them to the attackers in silver platters. Losses caused by this kind of attack totaled $ 929 million between May 2004 and May 2005.
After the first massive email phishing campaigns, email systems began to add intelligent filters for unwanted and malicious messages, and the success of basic email phishing tactics was reduced. But it did not disappear. Actually, more sophisticated tactics emerged, together with other forms of phishing, such as messaging phishing, voice phishing, and many others. They all exploit the weakest link in the cybersecurity chain: the end-user. Therefore, any anti-phishing initiative should start by making the user aware of the tactics that phishers employ. So let’s review them.
Email phishing and beyond
Email messages with suspicious attachments or links are easily detected by security filters, so phishers needed to design a new kind of email attack. They came up with business email compromise (BEC) attacks, based in messages with no malicious content at all –no links and no attachments, just a simple message from someone you know from your work environment.

To perform this kind of targeted attack, perpetrators need information about the victim and the person they pretend to be, in order to keep a fluid dialogue. After the first messages, the attacker will ask for sensitive information or send its victim a file or document with malicious content.
Website spoofing
In general, spoofing is involved in all kinds of phishing attempts, since there’s always someone or something pretending to be someone or something else. In particular, website spoofing is about making a webpage look legitimate. A spoofed website resembles the login page of a real site –not only it mimics the overall look and feel, but it also uses a similar domain name (as we discuss below).
Usually, these phony sites need other types of phishing —email, messaging, SMS, etc.– to conduct the victim towards them. Once the victim tries to log in on the spoofed site, its sensitive data falls in the attackers’ hands.
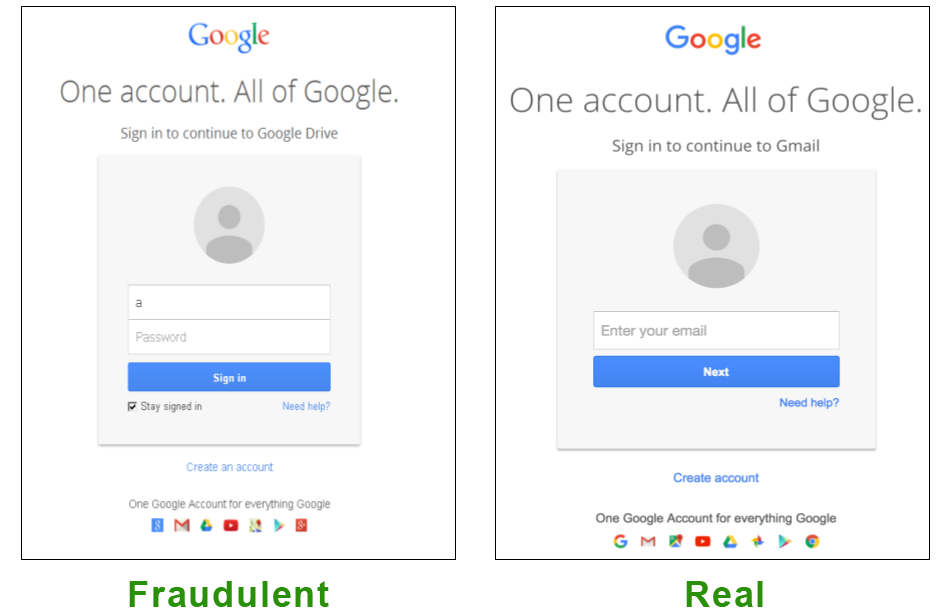
A type of attack related to website spoofing is a homograph attack. This kind of attack takes advantage of the new internet standards that allow the use of non-ASCII letters in URLs. Since different languages contain different (although very similar) characters, attackers can use these characters to register domain names that closely resemble existing web addresses. And these domain names are linked to spoofed websites.
For example, a basic character replacement used for homograph attacks consists of replacing “o” letters for “0” (zeroes). More complex techniques use differently encoded characters that look the same, like the letters “a,” “c” and “p” in Latin and Cyrillic. A slightly more sophisticated trick takes advantage of the resemblance between the ASCII slash (“/”) and the mathematical division operator (“∕”). Using this trick, anyone could think these addresses are the same:
somewebsite.com∕folder.com/
somewebsite.com/folder.com/
In this case, the spoofed domain name is somewebsite.com∕folder.com, and the real one is somewebsite.com.
Outsmarting filters
If an email filter sees that a message is supposedly sent by a very known company such as Microsoft (for example), but the source address is different from Microsoft, it will mark the message as malicious. But if the word “Microsoft” doesn’t appear in any part of the message, the filter will let it go through.

Attackers can trick the email filters by inserting hidden text within a company name, in such a way that any human reader would think it comes from that company, although the email filter won’t. Another similar trick consists of stuffing a message with white text over white background, unreadable to humans but not to email scanners, who get fooled to believe the message comes from a trusted source.
Identity theft and social media phishing
Millions of social media users have public profiles, exposing photos, personal information, and a list of contacts, just because they want to have a lot of online friends. If this is your case, it will be easy for an attacker to steal some of your photos and data, create a false profile and start chatting with your friends, pretending to be you, and asking them for anything in your name.

Phone numbers and name combinations are also phishing vectors, especially for WhatsApp scams (more on this below). Anyone who knows your name and phone number could contact you via WhatsApp with a convincing message to trick you into doing something, like, for instance, entering a malicious website disguised as a YouTube video you “must-see.”
WhatsApp risks
There are many WhatsApp scams that are as popular as the App itself. But still, many WhatsApp users aren’t aware of the scams and fall for it. WhatsApp Gold is a popular scam that offers users to upgrade to a “Gold” version of the App with special features. Obviously, there is no such version, and what you get if you follow the phishers’ instructions is a malware-infected device.

Another popular scam is a request to pay to keep your account active. This trick is almost as old as the App itself, but unaware users could still fall for it. Keep always in mind that there is no WhatsApp account to keep active, and therefore, no need to pay anything to keep your messaging App working.
Spear phishing and whaling
When a phishing attempt is highly targeted –aimed at specific people, organizations, or companies– it is called spear phishing. It is usually done through email messages or private communications systems, using compromised accounts. The FBI warned of spear phishing scams involving emails allegedly from the National Center for Missing and Exploited Children.
These attacks are often launched by hackers and government-sponsored computer activists. Cybercriminals employ individually designed approaches and social engineering techniques to effectively personalize messages and websites. As a result, the victims end up opening messages they consider safe. That way, cybercriminals steal the data they need to attack the victims’ networks.
Whaling is a special type of spear phishing that targets high-level executives –the “big fishes.” These attacks are aimed at CEOs, CFOs, and other executives responsible for managing the finances and crucial information of corporations. With such narrow targets, bait messages need to be smartly designed to have a credible and reliable appearance. Typically, attackers use information gathered from non-private social media accounts belonging to the victims.
Countermeasures
When you need to strengthen a chain, you should first look for the weakest link and strengthen it. Thus, in the cybersecurity chain, first of all, you should strengthen the user with awareness and knowledge about risks and their mitigation. Here are some tips that everyone should put into practice:
# Be cautious with all communications
Any link or attachment, whether it arrives by email, WhatsApp message, messaging service, SMS, or even through a physical device (a Pendrive, for example), is potentially dangerous. It doesn’t matter if you are sure you know the sender, and it is reliable. Before opening it or clicking on it, double-check it through an alternative medium, as explained below.

The most common phishing messages pretend to be from a known source, such as a bank, a financial services company, or a subscription-based service and tell you to renew your credentials or your subscription. The first thing you should ask yourself is: Am I a customer of this company? If not, just dismiss the message, or better, forward it to law enforcement.
Also, don’t answer suspicious messages from unknown sources. For example, you can be tempted to ask, “Who are you?” when you receive an intriguing message from an unknown number via WhatsApp. Just by asking that question, you are telling the phishers that your number is active and someone is using it, and more targeted phishing attacks could follow.
# Double-check via an alternative medium
Phishers can’t control all communication media. That is a weakness we can use against them, using different media to double-check any suspicious message. For example, if you get an email from a coworker asking you to click on a link, call him by phone and ask what that link is and why you should click on it.
# Report phishers to the authorities
Whenever you confirm that a received message corresponds to a phishing attempt, you should report it to the FTC at ftc.gov/complaint. If it is an email, you can forward it to [email protected] and [email protected] If you fell into a scam and think your private data may be compromised, visit IdentityTheft.gov. You will find detailed instructions according to the stolen information.
Last but not least: Protect yourself
To protect yourself from phishing attacks, you must take the same precautions as to protect yourself from any other threat in the digital world: keep your devices up to date, preferably with auto-updating; use the latest versions of proven anti-virus and security utilities; configure properly your email filters; backup your data; change your passwords periodically; learn to differentiate legitimate warnings from false ones, and read carefully the real warnings.
And, in general, stay informed, and double-check every security warning you get from your friends because most of the time they are false alarms, crafted with the sole purpose of increasing general confusion and facilitating true alarms to be dismissed.



