Let’s find out how you can leverage RASP to protect your applications.
The reason is obvious – rampant cybersecurity breaches across the globe, giving a hard time to individuals and businesses.
Now, applications are one of the favorite targets for cybercriminals, who are always on the lookout for finding vulnerabilities in your app. When they are successful in finding that, then God forbid, there’s a high chance they will pull off a data breach and harm you.
With such security issues around, finding an effective solution is naturally challenging.
So, what’s the solution for this?
One way of dealing with this issue is to let your apps protect themselves.
Confused?
Let me put it this way, there’s a technology that goes by the name of Runtime Application Self-Protection (RASP). And using this, your applications can surround themselves with a shield that will identify and block online threats in real-time.
In this article, we are going to discuss how your apps can become self-reliant for their protection through RASP tools that will help you incorporate this technology into your applications.
Let’s start!
What is RASP?

Runtime Application Self-Protection (RASP) is the technology that comes into the picture when an app runs. And when it starts running, RASP protects it against malicious inputs by analyzing the app behavior plus the context of this behavior. It continuously monitors and detects attacks and mitigates them immediately without requiring human intervention.
RASP incorporates security onto a running app no matter where in the server the app resides. It intercepts the calls from your apps to systems to ensure they are secure and validates requests inside your app directly. It protects both non-web and web apps and never affects your app design.
A RASP software is built within or integrated with the runtime environment of an application to execute its function in protecting the app.
How does it differ from a traditional WAF?
RASP is different from a traditional WAF or web application firewall. It’s because WAFs are coupled tightly with application codes that are susceptible to exploits.
A WAF inspects all the HTTP requests incoming for attack payload as well as suspicious usage patterns, and blocks or reports the request in case it finds something wrong. But, it cannot tell how the app will process those data and might result in false positives.
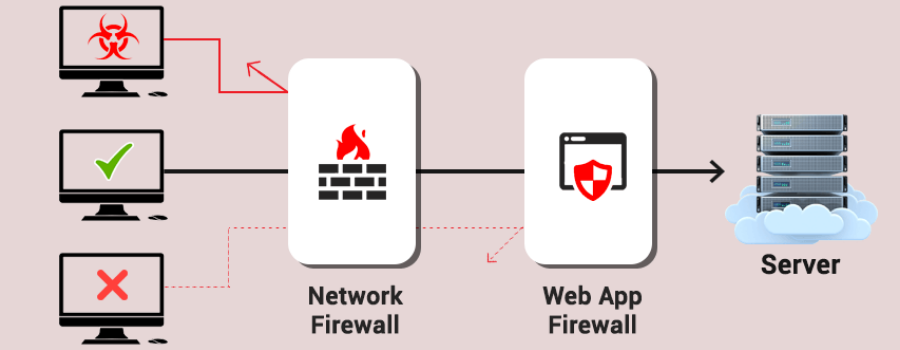
Besides, modern app development has shifted towards the model of continuous deployment which leads to constantly changing attack surfaces. Hence, it becomes highly difficult for a WAF to keep pace with the approach of usage patterns.
RASP, on the other hand, enables easier deployments, provides better controls no matter what the programming language is, and performs with better accuracy. Unlike WAFs, RASP automatically adapts to any environment or language and utilizes contextual awareness to monitor threats.
Instead of any blind guesses for a payload, RASP technology detects the complete data, which sometimes may include transformed data, based on how your app will utilize it and that’s exactly what contextual means here.
RASP typically has much lower false positives as compared to WAFs. Furthermore, while a WAF provides a strong wall to secure the app on the frontline, RASP provides a robust shield to protect your app from inside out through its innovative capabilities.
Benefits of using RASP
- As RASP makes informed decisions based on contextual detection along with rich application architecture combining static and dynamic view, there are significantly lower false positives.
- RASP is capable of protecting your app from a variety of risks including OWASP’s top 10 vulnerabilities, injections, insecure deserialization, weak randomness, IDOR, suspicious client activity, SSRF/CSRF, and more.
- Quick adaptability to app architectures, and can even safeguard non-web standards like RPC or XML.
- With no blacklists, traffic rules for configuration, or learning process, RASP solutions are easy to maintain. This is why people love this, rely on it, and appreciate the time and cost it saves.
- RASP enables cloud support. As they are self-protected, the code remains protected at all times wherever the app goes. Its configuration could be included in build scripts, generating and containerizing your application without having to update the firewall or network rules.
Now that you know about it, let’s explore some of the following best RASP solutions you can deploy to your application.
Fortify
Monitor your applications and protect them against vulnerabilities and common attacks in real-time with Fortify Application Defender by Microfocus.
It differentiates between legitimate requests and dangerous threats in .NET and Java apps while protecting production apps from zero-day attacks. Its end-to-end app security solutions cover your overall development lifecycle.
Fortify offers logging visibility as well as exploit data associated with web applications in addition to line-of-code details. It also allows you to send exploit and log events to a log manager or SIEM without having to change the source code for security visibility and compliance.
You will get a robust and layered defense system that keeps your apps safe and minimizes production environment overheads. It includes 32 security rule categories that protect you from security violations including cross-site scripting, SQL injections, privacy violations, and more.
Get instant security with flexible and quick deployment without changing a single code line or any WAF training. You can control your protection from an easy-to-use and centralized management console.
Sqreen
The unique architecture of Runtime Application Self-Protection (RASP) by Sqreen provides deep visibility and protection for your applications beyond its HTTP layer. Thousands of developers and security teams trust this solution due to its extensive and reliable offerings.
Sqreen’s RASP leverages the complete request context to detect an attack that can exploit vulnerabilities present in the production process. It also mitigates critical attacks with no false positives.
Besides, its security also provides zero-day coverage, shielding your application against the Top 10 Vulnerabilities of OWASP such as XSS, SSRF, SQL injections, and more. It never relies on patterns and signatures that are easy to cut through and can adapt quickly to your application stack.
You get in-application insights to know about the assets, risks, and incidents associated with your application. For this, you get a unified dashboard, and you can turn those insights into real-time action. You can identify attacks beyond separate IPs and fasten the remediation efforts.
All it needs is just a few minutes for Sqreen to set up and then, it performs out-of-the-box by instrumenting 500 points inside your apps, APIs, and microservices dynamically. You can implement it without any code modifications or configurations. It has a distributed architecture that is fail-safe through an embedded virtual machine in sandboxed micro-agents.
Sqreen walks extra miles for your security beyond RASP by embedding various protection solutions into one – in-app WAF, account takeover, content security policy, etc., plus allows you to integrate SDLC.
Signal Sciences
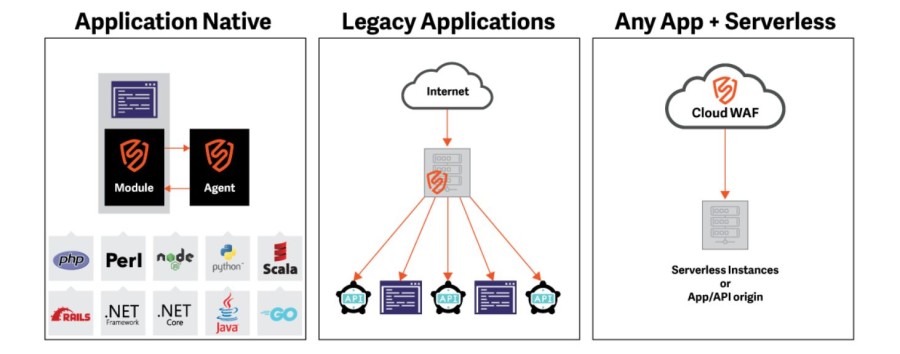
The easy-to-install software of Signal Sciences supports various programming languages and frameworks, including PHP, Scala, Perl, Node.js, Python, Java, Go, .NET, and Rails, and protects them from attacks while maintaining their performance. It can integrate into a DevOps toolchain product for wider, cross-team visibility.
Signal Sciences protects 40k apps per year on average, has managed to provide great customer service, and supports 100 multi-cloud and hybrid platforms.
It is one of the market leaders when it comes to RASP due to its reliability, operational manageability, scalable protection, and various deployment options no matter where your application operates.
You will get protection far beyond Top 10 OWASP vulnerabilities including bad bots, account takeover, app DDoS, API abuse, and more. It supports multiple architectures from an application native to legacy applications, serverless, and containers. As they provide a hybrid-SaaS solution, you can deploy it into your apps directly with only one DNS change, requiring no agents.
Self-serve security insights and alerts help you solidify your security posture and remain proactive always.
Jscrambler
Turn up to Code Integrity by Jscrambler to protect your apps from abuse, tampering, code theft, and piracy with enterprise-level JavaScript obfuscation, defensive techniques, and code locks.
Every time you safeguard your JavaScript codes using Jscrambler, it gives you a highly safe version of it that hides essential logic and keeps its original functionality intact. You would be able to detect tampering and debugging attempts while breaking up your application on purpose to mitigate attackers from modifying or even analyzing your codes.

Jscrambler allows you to lock your codes and run them only in certain domains, browsers, date ranges, and OSes. In case a lock violation occurs, it will break your application. Set up automatic reactions for preventing attacks like attacker redirects, calling custom functions, and real-time notifications.
Jscrambler provides stronger protection through JavaScript Threat Monitoring. It monitors the entire protected codes you have in real-time and warns in case of mishaps. With a clear dashboard, you can access statistics and relevant data regarding your protected applications and tweak the security to ensure their optimal performance.
Integrate Jscrambler seamlessly into your CD/CI pipeline to ensure all your deployed versions are perfectly secure. It is always up-to-date thanks to JS Specialists who can support you all the time. It is compatible with major languages, frameworks, and browsers.
Hdiv
Hdiv empowers your application from the inside out so that they can take care of their protection during development and also protects them no matter where they are. It provides real-time whitelisting, proactive performance, and does not require you to learn how to code.
Hdiv quickly detects security bugs and/or syntax security problems to protect your apps more through their development lifecycle. It incorporates IAST capabilities needed for bug protection with whitelist validation in real-time to safeguard against attacks about your business logic.
Simplicity is another attribute of Hdiv and it is integrated into SDLC without tuning needs during the production phase. It simplifies the entire operation plus deployment of your applications including APIs, web apps, and microservices.
Apart from that, Hdiv helps you implement the necessary compliance needs such as GDPR and PCI, which are applied directly without you worrying about app modifications. So. Just get started with Hdiv in a few minutes by:
- Downloading Hdiv agent through one-line of code
- Configuring it and including Hdiv’s library into your app
- Run it, and then restart your application.
Hdiv supports technologies such as .NET, Java, Spring, React, AngularJS, ASP.NET, REST, and more for your apps that you can deploy in any physical or cloud environment.
Imperva
Get superior security of your apps by Imperva which is a well-known brand when it comes to cybersecurity solutions. It protects apps from online threats of different sorts so you can better focus on your business logic instead of drowning deep in the security issues.
Your cloud-native apps require greater security than perimeter security due to present-day security scenarios, which is why Imperva provides security from inside and walks along with your apps.
Imperva’s RASP is built into an app runtime environment that is capable of protecting from zero-day attacks, OWASP top ten vulnerabilities, it’s highly accurate, and needs no tuning. In addition to those, you get safety from clickjacking, large requests, HTTP response and method tampering, malformed contents, unvalidated redirects, and path traversals.
Using Imperva, you are safe from injection such as command injection, cross-site injections, cross-site scripting, CSS and HTML injection, JSON and XML injection, database access violation, OGNL injection, and SQL injection.
Its in-depth security helps your applications in weaker areas such as insecure cookies and transport, unauthorized network activities, logging sensitive data, weak authentication, browsing caching, and cryptography. When RASP combines with WAF, it gives out-of-the-box security and that’s what Imperva does.
Hence, you get all-around protection from DDoS, script kiddies, malicious bots, external threats, and more. Imperva uses a patented grammar-oriented technique to defend applications without patches or signatures while saving you from extra operational costs.
It is equipped with insider threat protection which is attached to app runtime for safeguarding them from malicious and careless insiders. You get wider visibility of different issues with your apps in one place, including attack classifications, network data, operating system, user sessions, file name, code execution, and databases.
It supports platforms like Java, .NET, Nodejs, Oracle, PostgreSQL, MySQL, SQL Server, IBM DB2, IBM Radar, Elastic, etc, and works for all types of applications including APIs, legacy, containerized.
Conclusion
Cybersecurity is crucial, and it’s something you must not ignore. Save your applications from threats and exploits that can be more dangerous than you might have anticipated.
Instead, you can use an efficient RASP solution like those I have mentioned in this article to protect your application against different types of vulnerabilities and threats.



