The traditional perimeters of networks have disappeared. Access to an organization’s applications and digital assets occurs from far places, and controlling those accesses becomes a serious challenge. The days when network borders could be protected are long gone. Now is the time for new zero-trust security strategies.
When a company’s digital assets have to traverse long distances on the unsafe paths of the Internet, the stakes are so high that you can trust nothing and no one. That’s why you should adopt the zero-trust network model to restrict all users’ access to all network resources at all times.
In zero-trust networks, any attempt to access a resource is restricted from a user or a device, regardless of whether they have previously accessed the same resource. Any user or device must always go through an authentication and verification process to access resources, even when they are physically within the organization. These authentications and verifications must be fast to avoid that the security policies degrade the performance of the applications and users’ experience.
Zero-trust vs. VPN

The zero-trust network model is replacing the VPN model traditionally used by companies for their employees to access their digital assets remotely. VPNs are being replaced because they have a major flaw that zero-trust networks can resolve. In VPNs, any breach that occurs in the encrypted channel that connects a user to the organization’s network grants potential attackers unlimited access to all company resources connected to the network.
On old, on-premises infrastructures, VPNs worked well, but they generate more risks than solutions on cloud or mixed infrastructures.
Zero-trust networks fix this shortcoming of VPNs but add a potential downside: they can lead to additional complexity in terms of implementation and maintenance, as authorizations must be kept up-to-date for all users, devices, and resources. This requires extra work, but IT departments achieve greater control over resources and a reduction in vulnerabilities in return.
Fortunately, the benefits of a zero-trust network can be realized without the need for added maintenance and deployment efforts, thanks to tools that automate and assist in network administration tasks. The tools discussed below help you apply zero-trust policies with minimal effort and costs.
Perimeter 81
Perimeter 81 offers two approaches to managing and keeping an organization’s applications and networks secure, both on cloud and on-premises environments. The two proposals start from offering zero-trust networks as a service. To do this, Perimeter 81 uses a software-defined perimeter architecture, which provides great flexibility to onboard new users and offers greater visibility into the network. In addition, the service is compatible with the main cloud infrastructure providers.
Zero Trust Application Access is based on the assumption that every company has critical applications and services that most users do not need access to. The service allows raising barriers to specific users based on their roles, devices, locations, and other identifiers.
Meanwhile, Zero Trust Network Access defines a segmentation of the organization’s network by trust zones, which allows the creation of trust limits that control the flow of data with a high granularity level. Trusted zones are made up of sets of infrastructure elements with resources that operate at the same level of trust and provide similar functionality. This reduces the number of communication channels and minimizes the possibility of threats.
Perimeter 81’s Zero Trust Network Access service offers a complete and centralized view of the organization’s network, ensuring the least privileged access possible for each resource. Its security features respond to Gartner’s SASE model, as security and network management are unified on a single platform.
The two Permiter 81 services are included in a pricing scheme with a wide range of options. These options range from a basic plan with the essentials to secure and manage a network to an enterprise plan that can scale unlimitedly and provides dedicated 24/7 support.
ZScaler Private Access
ZScaler Private Access (ZPA) is a cloud-based, zero-trust network service that controls access to an organization’s private applications, regardless of whether they are located in a proprietary data center or a public cloud. With ZPA, applications are completely invisible to unauthorized users.
In ZPA, the connection between applications and users is carried out following an inside-out strategy. Rather than extending the network to include users (as it should be done if using a VPN), users are never inside the network. This approach substantially minimizes the risks by avoiding the proliferation of malware and the risks of lateral movement. In addition, ZPA’s scope is not limited to web applications but any private application.
ZPA uses a micro tunnel technology that allows network administrators to segment the network by application, avoiding the need to create artificial segmentation in the network or apply control by firewall policies or managing access control lists (ACLs). The micro tunnels employ TLS encryption and custom private keys that strengthen security when accessing corporate applications.
Thanks to its API and ML (machine learning) enhancements, ZPA lets IT departments automate zero-trust mechanisms by discovering apps and creating access policies for them and by generating segmentation automatically for each different app workload.
Cloudflare Access
Cloudflare’s zero-trust network service is supported by a proprietary network with access points distributed throughout the world. This enables IT departments to provide high-speed, secure access to all of an organization’s resources — devices, networks, and applications.
Cloudflare’s service replaces traditional, network-centric security perimeters, using instead secure, close-range accesses that ensure optimal speed for distributed workgroups.
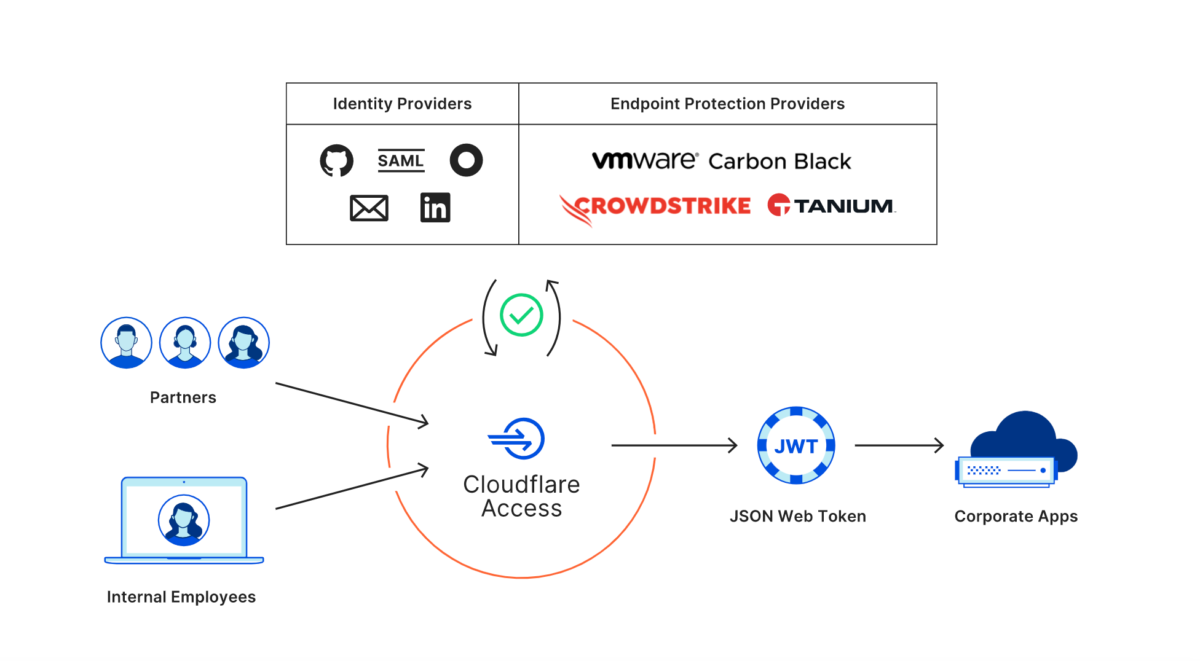
Cloudflare’s zero-trust access operates overall applications in an organization, authenticating users through its own global network. This allows IT managers to record each event and each attempt to access a resource. In addition, it makes it easy to maintain users and to add additional users.
With Cloudflare Access, the organization can maintain its identity, protection providers, device posture, location requirements per application, and even its existing cloud infrastructure. For identity control, Cloudflare integrates with Azure AD, Okta, Ping, and device posture, with Tanium, Crowdstrike, and Carbon Black.
Cloudflare offers a free version of its service that provides the main tools and allows you to protect up to 50 users and applications. You must choose the paid versions of the service to scale to many users or applications, which add other benefits such as 24x7x365 telephone and chat support.
Wandera Private Access
Wandera Private Access zero-trust networking solution offers fast, simple, and secure remote access to an organization’s applications, whether they operate in SaaS or are deployed internally. The service stands out for its simplicity, with installation procedures that can be completed in minutes and don’t require specialized hardware, certificates, or sizing.
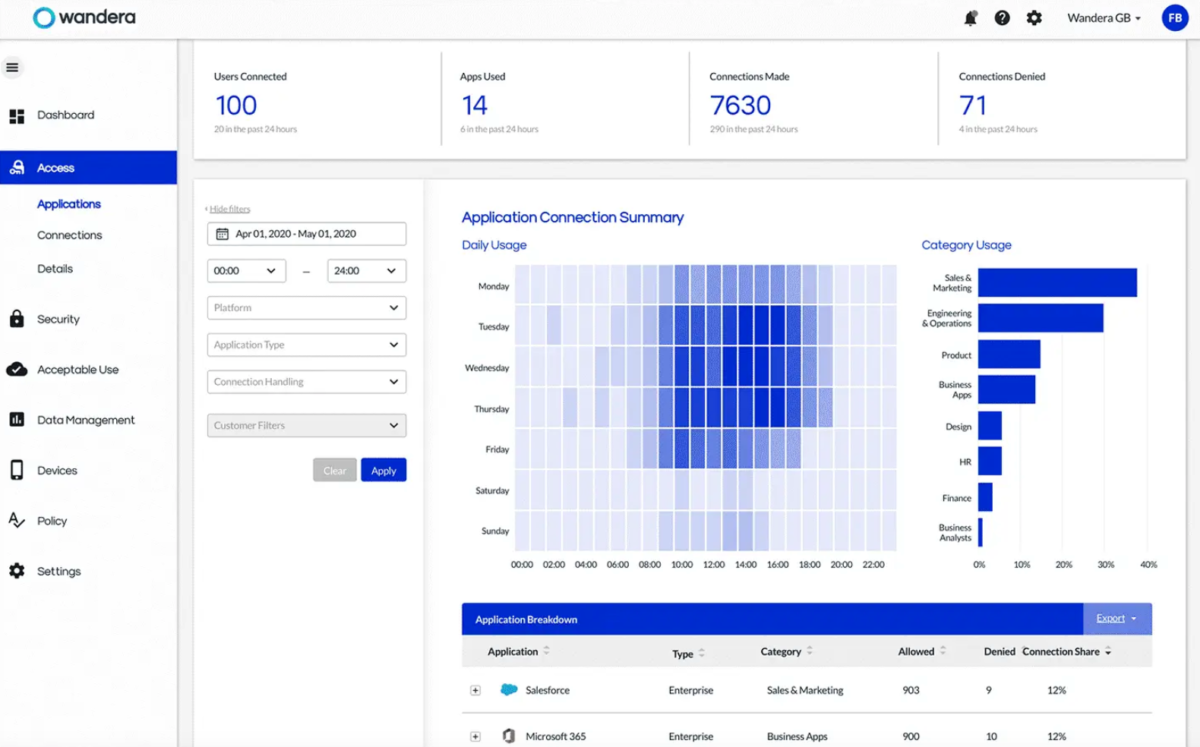
Wandera Private Access offers flexibility for distributed work teams, operating on heterogeneous platforms, with managed or owned devices (BYOD). The solution provides real-time visibility into application access, identifying shadow IT, and automatically restricting access from infected or insecure devices, thanks to risk-aware access policies.
With Wandera Private Access, identity-centric security models can be implemented, ensuring that only authorized users can connect to the organization’s applications. The use of application-based micro tunnels connects users only to the applications they are authorized to access. The application of security policies remains consistent across all infrastructures, be it cloud, data-center, or SaaS applications.
Wandera’s protection system is powered by an intelligent threat detection engine called MI:RIAM. This engine is fed daily with the information provided by 425 million mobile sensors, which ensures protection against the widest range of known and zero-day threats.
Okta
Okta offers a zero-trust security model that encompasses a wide range of services, including application, server, and API protection; unified and secure user access to on-prem and cloud applications; adaptive, context-based, multi-factor authentication, and automatic off-boarding to mitigate orphan account risks.

Okta’s universal directory service provides a single, consolidated view of every user in an organization. Thanks to the integration of user groups with AD and LDAP, and connections with HR systems, SaaS applications, and third-party identity providers, Okta Universal Directory integrates all kinds of users, whether they are company employees, partners, contractors, or customers.
Okta stands out for its API protection service since APIs are regarded as a new form of shadow IT. Okta’s API access management reduces hours of designing and applying XML-based policies to a matter of minutes, facilitating onboarding of new APIs and integration with partners for the use of APIs. Okta’s policy engine allows implementing best practices in API security, easily integrating with identity frameworks such as OAuth. API authorization policies are created based on applications, user context, and group membership to ensure that only the right users can access each API.
Okta’s integration network avoids vendor lock-in, giving organizations the freedom to choose from more than 7,000 pre-built integrations with cloud and on-prem systems.
CrowdStrike Falcon
The CrowdStrike Falcon Identity Protection zero-trust security solution quickly stops security breaches due to compromised identities, protecting identities for all users, locations, and applications in an organization using zero-trust policies.
Falcon Identity Protection aims to reduce costs and risks and increase the ROI of tools in use by reducing engineering resource requirements and eliminating redundant security processes.
The unified control of all identities makes it easy to implement Conditional Access and Adaptive Authentication strategies, as well as ensuring a better user experience and greater coverage of multi-factor authentication (MFA), even for legacy systems.
The CrowdStrike remote access solution offers complete visibility into the authentication activity of all accounts and endpoints, providing location data, source/destination, type of login (human or service account), among others. In turn, it protects the network from insider threats, such as deprecated privileged accounts, misassigned service accounts, abnormal behavior, and credentials compromised by side-movement attacks.
By integrating with existing security solutions, the deployment of Falcon Identity Protection is carried out in minimal time and without friction. In addition to offering direct integration with security solutions for critical assets, such as CyberArk and Axonius, CrowdStrike offers high-performance APIs that allow companies to integrate with virtually any system.
Conclusion
The new normal seems to stay, and IT administrators need to get used to it. Remote work will continue to be a daily reality, and organization networks will never again have clearly defined boundaries.
In this context, IT administrators must adopt zero-trust network and application solutions as soon as possible if they do not want to put their organizations’ most precious digital assets at risk.



