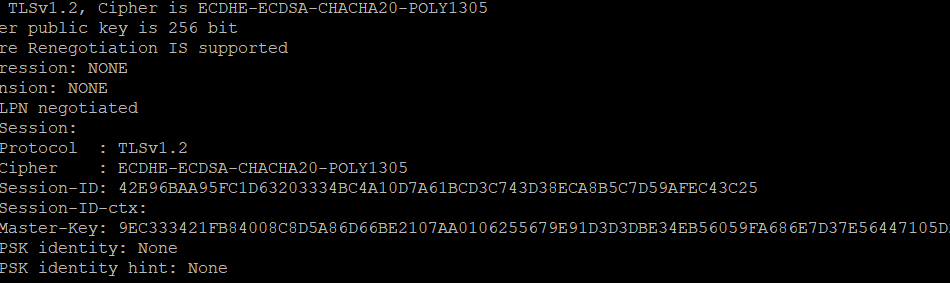
Transport Layer Security (TLS) is an essential part of securing web applications and their communications. Ensuring that your Apache server is using the appropriate TLS version can significantly enhance your website’s security. This article will guide you through the process of configuring your Apache server to use a specific TLS version.
1. Introduction to TLS
Transport Layer Security (TLS) is a cryptographic protocol used to secure communications over a network. It is an updated and more secure version of the Secure Sockets Layer (SSL) protocol. TLS ensures the confidentiality, integrity, and authenticity of data transmitted between clients and servers.
2. Prerequisites
Before proceeding, ensure that you have the following prerequisites in place:
- A Linux-based server with Apache installed.
- Root or sudo access to the server.
- A valid SSL/TLS certificate installed on your server. If you do not have one, you can obtain a free certificate from Let’s Encrypt.
3. Updating Your Apache Server
To ensure that your Apache server supports the desired TLS version, it is crucial to keep your server updated. Run the following commands to update your server and install the latest version of Apache:
- For Debian-based systems:
sudo apt-get updatesudo apt-get upgradesudo apt-get install apache2 - For Red Hat-based systems:
sudo yum updatesudo yum install httpd
4. Configuring Apache to Use a Specific TLS Version
To configure your Apache server to use a specific TLS version, follow these steps:
- Open the Apache configuration file in a text editor. The location of this file may vary depending on your server’s setup. Common locations include:
- /etc/httpd/conf/httpd.conf (Red Hat-based systems)
- /etc/apache2/apache2.conf (Debian-based systems)
- /etc/apache2/sites-available/000-default.conf or /etc/apache2/sites-available/default-ssl.conf (Debian-based systems, for virtual hosts)
- Locate the
block that corresponds to your SSL/TLS-enabled website. - Add or modify the following lines within the
block:SSLProtocol –all TLSv1.2
SSLHonorCipherOrder on
SSLCipherSuite “EECDH AESGCM:EDH AESGCM:AES256 EECDH:AES256 EDH”
Replace TLSv1.2 with the desired TLS version, such as TLSv1.3. The SSLCipherSuite directive specifies a list of ciphers that the server should use in its communications.
You can also enable both TLSv1.2 and TLSv1.3 like: “SSLProtocol -all TLSv1.2 TLSv1.3”
- Save the changes and exit the text editor.
- Restart the Apache server to apply the changes:
sudo systemctl restart apache2or
sudo systemctl restart httpd
5. Testing Your Configuration
To test your configuration and verify that your server is using the specified TLS version, you can use an online tool like Qualys SSL Labs or a command-line tool like openssl:
openssl s_client -connect yourdomain.com:443 -tls1_2
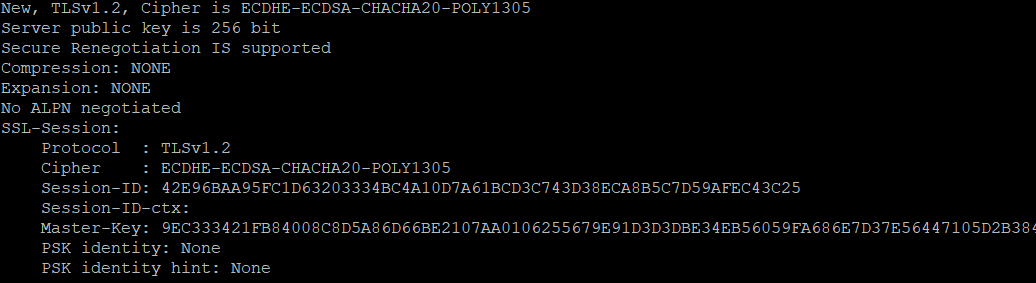
Replace yourdomain.com with your website’s domain and -tls1_2 with the appropriate TLS version flag (e.g., -tls1_3 for TLS 1.3). If your server is configured correctly, you should see a successful connection and the details of your SSL/TLS certificate.
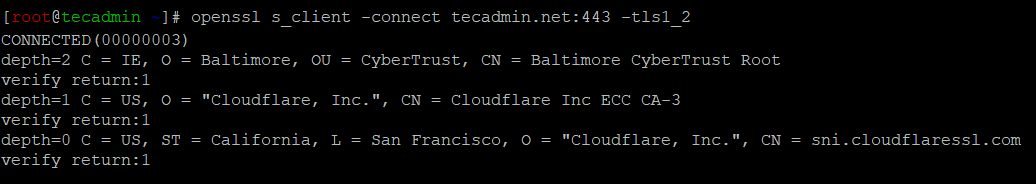
In the above screenshot “CONNECTED(00000003)” for successful connection over TLS 1.2. . You should also scroll down to see complete result.
6. Best Practices for TLS Configuration
When configuring your Apache server to use a specific TLS version, keep the following best practices in mind:
- Disable insecure protocols: Disable older, insecure protocols like SSLv2, SSLv3, and even TLSv1.0 and TLSv1.1 to protect your server from potential vulnerabilities.
- Use strong ciphers: Choose ciphers that provide strong encryption and avoid those with known weaknesses. The Mozilla Foundation offers a recommended list of ciphers for various compatibility levels.
- Enable HTTP Strict Transport Security (HSTS): HSTS is a security feature that instructs web browsers to communicate with your server using only HTTPS. To enable HSTS, add the following line to your block:
Header always set Strict–Transport–Security “max-age=63072000; includeSubDomains; preload”
- Keep your server updated: Regularly update your Apache server and its dependencies to ensure that you are using the latest security patches and features.
- Monitor and test: Regularly test your server’s SSL/TLS configuration using tools like Qualys SSL Labs or openssl to detect and address potential vulnerabilities.
Conclusion
Configuring your Apache server to use a specific TLS version is an essential step in securing your web applications and their communications. By following the steps outlined in this article, you can enhance your server’s security and protect sensitive data from potential threats. Remember to adhere to best practices, keep your server updated, and regularly monitor your SSL/TLS configuration to maintain a secure environment.