Digital Forensics is an essential part of cybersecurity, involving identification, preservation, analyzing, and presenting digital evidence.
It is a lot of things to know in 5 minutes or less. However, we have summarized everything essential for you in the initial section of this article.
The evidence is collected and maintained using a scientific process that ensures it is admissible in a court of law.
Why Do We Need Digital Forensics?
Without Digital Forensics, we cannot detect if systems are vulnerable or compromised. Even if we detect a breach, we need the help of digital forensics to trace what happened, why it happened, and how it happened.
So, enterprises or other cybersecurity professionals can patch the security issues and ensure that the same kind of cyberattack does not get through the next time.
As the data and technology we interact with get complex daily, digital forensics and forensic investigation tools ensure we can hold cybercriminals accountable for modifying, stealing, or any other malicious activities.
When Should Businesses Use Digital Forensics?
There can be various situations when a business needs to use digital forensics.
The most common one is a data breach, where digital forensics (usually experts from out of the organizations also come in help) lets them evaluate the impact and countermeasures and how to deal with it the next time.
Other scenarios might include a rogue employee, a phishing scam, a data leak from within the organization, etc.
Advantages of Digital Forensics
Digital forensics is not just limited to the purpose of catching cyber criminals, it has several other advantages as well.
Some of them include:
- It is helpful for data recovery (using the extraction methods)
- It protects the data and, thus, any precious value it holds
- It helps you collect evidence for criminal activity or proof to refute an allegation
- Investigation of cybercriminal activity at any scale
- It ensures the integrity of the system
- Identifying criminals
- Prevents future cyber crimes using the insights gained
Different Types of Digital Forensics
The types of digital forensics depend on the medium or platform involved. So, the number of types is not limited to the ones described below. We have included some of the major ones for you to get a head start:
Computer Forensics: The identification, preservation, collection, analysis, and reporting of evidence on computers are what all this is about. Of course, it includes laptops/PCs and attached storage drives as part of it. The mobile storage drives are also included.
Network Forensics: When the investigation process is focused on the network and its traffic, it is called network forensics. The terms are a bit different as it includes monitoring, capturing, storing, and analyzing malicious traffic, breaches, and anything suspicious on the network.
Mobile devices Forensics: The forensics that deals with evidence recovery from mobile phones, smartphones, SIM cards, and anything that is remotely mobile (or portable).
Digital Image Forensics: The photographs can be stolen, digitally modified, and misused. Digital image forensics come in handy in such situations where they check the metadata and any associated data to validate the image. Image forensics can be pretty interesting and challenging, as we are already living in the age of media dominance.
Digital Video/Audio Forensics: The forensics involves audio clips and video files, and here, you get to validate and check the file’s origins for authenticity and if it has been modified.
Memory Forensics: The evidence recovered from the RAM of a computer. Usually, mobile devices aren’t part of this. This might change as the memory of mobile devices gets more sophisticated and crucial.
Process of Digital Forensics
As mentioned above, digital forensics follows a scientific process that ensures the evidence collected is admissible in a court of law, regardless of the activity being verified/investigated.
The process includes three phases for any digital forensics:
- Data Collection
- Examination and Analysis
- Reporting
If we break down the process involved with it, we can summarize them as follows:
With Identification, you identify the evidence, the associated device, the source of the original data, the source of the attack, and so on. Once you know what you are dealing with and know all the potential sources of evidence, you can further analyze it.
Preservation is crucial as it records/stores the evidence as it was found without tampering. The data/evidence can often be sensitive. So, the preservation process needs to be handled with care.
The collection is about extracting/copying/saving the evidence found in different mediums. Sounds easy, but the collection process is vital to everything, and the methods used will affect the quality of the data being collected.
Analysis of evidence collected will be examined further to get takeaways from the incident and reach a conclusion depending on the type of evidence and the amount of data involved. Sometimes it might prompt the need to ask for help from other forensics experts.
Reporting is about presenting and organizing the insights/evidence found in the process. This should help anyone else (other experts) continue the investigation without any hassle.
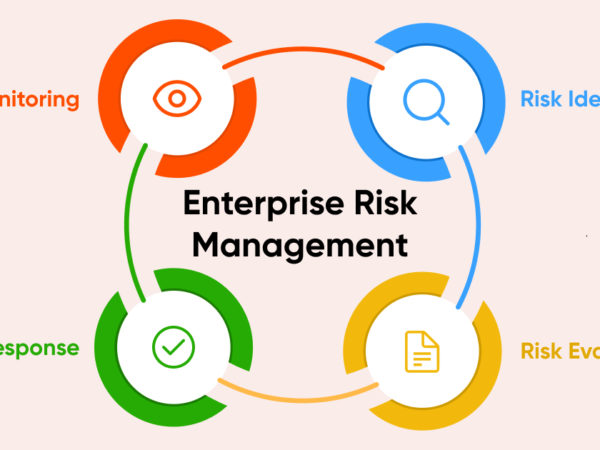
Phases of Digital Forensics
While I mentioned the phases of digital forensics before getting down to the process, let me highlight some more details on it:
#1. First Response
This is the first phase of any digital forensic process, where the situation is reported. So the digital forensics team can act upon it.
It is not just about getting notified, but how efficiently the forensics team responds to tackle the situation and lays out all of its cards to do the work quickly.
#2. Search and Seizure
As soon as the crime has been reported, the forensics team starts searching/identifying and seizing the medium/platforms involved to stop any associated activity.
The effectiveness of this phase makes sure that no further damage is done.
#3. Evidence Collection
The evidence is carefully extracted and collected for further investigation.
#4. Securing the Evidence
Usually, the experts ensure the best ways to preserve the evidence before collecting them all. But, once collected, they have to ensure their safety of it. So the evidence can be processed further.
#5. Data Acquisition
The data is gathered from the evidence using required industrial processes that keep the evidence’s integrity and do not alter anything collected.
#6. Data Analysis
Once the data is acquired, the experts start examining what they have to be admissible in court.
#7. Evidence Assessment
The evidence collected will be checked by the forensics team to know the relation of it with any related cyber criminal activity reported.
#8. Documentation and Reporting
Once the investigation is complete, the documentation and reporting phase begins, where every minute detail is included for future reference and to be presented to the court.
#9. Expert Witness Testimony
For the last phase, an expert comes in handy to validate and give their view of the data to be used in the court.
Note that the entire digital forensics process is extensive and can vary depending on the technology and methodology being used. The process used in the real world might be way more complex than what we discuss here.
Digital Forensics: Challenges
Digital Forensics is a vast area with many things involved. There are no single experts to help with it. You always need a team of experts for it.
Even with all that, some challenges include:
- The complexity of data increases every day
- Hacking tools easily accessible to everyone
- Storage spaces get bigger, which makes it difficult to extract, collect, and investigate
- Technological advancements
- Lack of physical evidence
- The authenticity of data gets more brutal as data tampering/modification techniques evolve.
Of course, with technological advancements, some of the challenges may fade away.
Not to forget, AI tools coming into the scene also try to overcome the challenges that come into the situation. But, even then, the challenges would never vanish.
Use-Cases of Digital Forensics
While you know that it involves cyber crimes, what exactly? Some of the use cases include:
Intellectual Property (IP) Theft
IP Theft happens whenever an asset/information unique to the company is passed on to a competitor company without authorization. Digital forensics help identify the source of the leak and how to minimize or mitigate the threat that emerged after the exchange.
Data breach
Compromising the data of an organization for any malicious purpose will be considered a data breach. The digital forensics process will help identify, evaluate, and analyze how the data breach occurred.
Employee leaks
A rogue employee can misuse the authorization and leak information without anyone realizing it at first.
The digital forensics team can analyze what exactly was leaked and investigate the timeline of this happening to take action against the rogue employee in a court of law.
Fraud/Scams
Fraud/Scams can happen in a variety of shapes and sizes. Digital forensics helps us know how it happened, what helped it happen, and how to stay safe. The source/actor responsible for it should also be analyzed in the process.
Phishing
There are phishing campaigns that lead to data breaches and a variety of cyber security incidents.
Some of them are targeted, and some can be random. So, digital forensics analyzes the roots of it, identifies the objective, and suggests how not to get fooled into such campaigns.
No matter how tech-savvy the organization is, phishing is something that can always leave someone vulnerable at any point without realizing it.
Misuse of data
We deal with lots of data; anyone can misuse any piece of information for various reasons. Digital forensics helps prove what happened and prevents the damage or mitigates that happened because of it.
Investigating to prove the claims made by an organization
You need concrete evidence to prove what you claim. So, whenever there is a dispute, digital forensics helps collect proof that you can utilize to reach a conclusion.
Learning Resources
If you find digital forensics intriguing, you can refer to some of the learning resources (books) that you can find on Amazon. Let me give you a quick overview of some of them:
#1. The Basics of Digital Forensics
The basics of digital forensics are the perfect resource to get a head start in your journey of exploring digital forensics.
The book tackles the fundamentals, the methods used, the concepts you need to understand, and the tools needed to work with them. In addition, the book also includes real-world examples to help you understand things better while adding pointers to every step of the process involved.
You can find details on digital forensics for computers, networks, cell phones, GPS, the cloud, and the internet as well.
#2. Digital Forensics and Incident Response
This resource of digital forensics and incident response helps you learn to create a solid incident response framework to manage cyber incidents effectively.
You get to explore real-world incident response techniques that can help with investigation and recovery. The fundamentals, and the frameworks, are all about incident response.
Not limited to it, the book also includes information on threat intelligence that helps with the incident response process and a few bits on malware analysis.
#3. Digital Forensics Workbook
As the name suggests, the digital forensics workbook presents hands-on activities using a comprehensive range of tools.
So, you can practice media analysis, network traffic, memory, and several other steps involved in digital forensics. The answers are explained in such a way that you get to realize the correct order of steps and practice accordingly.
Wrapping Up
Overall, digital forensics is fascinating and overwhelming at the same time. However, if you are into cybersecurity, digital forensics is something you should explore.
Next, You may read about Security Information and Event Management and best SIEM tools to help secure your organization from cyber-attacks.