Geekflare is supported by our audience. We may earn affiliate commissions from buying links on this site.
A disaster recovery plan is a foremost measure that an organization must have before an unusual event hits them.
In the IT industry, it starts by creating a formal document containing plans, actions, and procedures on dealing with the disaster and its after-effects.
Disaster is an event that comes suddenly with no prior notice and can be of different types. And when it lands, individuals and organizations face difficulties of many sorts, including financial issues and user experience.
If an attack happens, you must be ready to minimize its effects and restore your operations faster. This is where preparing a practical disaster recovery plan will help you withhold or prevent the disaster. You can also reduce its after-effects in terms of user experience, cost, and downtime.
In addition, you must keep your plans, people, strategies, equipment, and systems ready to get everything back in action. But for this, you must understand disaster recovery in depth.
In this article, I’ll discuss this in detail along with key disaster recovery terminologies so you can fight back bravely and come out stronger in such adverse conditions.
Let’s begin!
What Is a Disaster?

A disaster is an unforeseen event that can happen anywhere, including the IT industry. It occurs either naturally or by people and can interfere with a company’s operations and disturb the fabric of the infrastructure.
As a result, an organization and its customers, vendors, employees, and partners are affected. It puts pressure on the organization in terms of finances, industry reputation, customer trust, and security perimeter.
Hence, you must be ready in advance to overcome such a scenario. For this, you need to recover every operation and data instantly. In simple words, you must prepare your organization to recover everything in the shortest interval possible for your customers.
Disasters are of many types, such as cyber-attacks, sabotage, terrorist attacks, ransomware or physical threats, hurricanes, earthquakes, fires, floods, industrial accidents, power outages, and a lot more.
What Do You Mean by Disaster Recovery?
Disaster recovery is the process of regaining normal operations after suffering from a disaster. It involves resuming access to hardware, software, equipment, connectivity, networking, power, and data. You must set rules and procedures in a documented process to prepare your organization before a disaster.
However, if your organization’s facilities are destroyed, you must extend some of the activities by working on communication, transportation, sourcing, work locations, and more.
Why Is Disaster Recovery Plan Important?
Drafting a perfect plan for recovering from a disaster, either natural or man-made, is essential for every IT industry. Make sure you have the right employee and tools at the right place to carry out the plan smoothly.
Let’s dive deeper into why disaster recovery is crucial.
Limit Damages
A disaster is unpredictable. No one knows when it comes and goes. But, you prepare in advance to control the damage caused to your infrastructure.
For example, in flood-prone areas, you can place your essential documents and types of equipment on the top floor to avoid damage.
Similarly, backup your essential data before cyber attacks can breach data or steal it.
Restoring Services
If you prepare a solid plan for recovering from the disaster, restoring all the services to their normal form is quick and easy. It means in a short interval of time, you can recover almost all the major assets and services.
Minimize Interruption
You can’t know what will happen tomorrow or in the next step of an operation. But, with a perfect recovery plan, you don’t have to worry about the consequences much. Your infrastructure can continue the operations with minimal interruption.
Training and Preparation

An IT infrastructure consists of many employees working under a roof. All must know about the recovery to act immediately as required and expected in case of an emergency.
Proper preparation will also lower the stress levels of everyone associated with your organization. Furthermore, you can train your employees to take necessary actions if an unexpected event occurs.
Disaster Recovery Terminologies
Let’s start with the terminologies to understand disaster recovery from a closer view.
RTO
Recovery Time Objective (RTO) is the amount of time that an organization sets according to the nature of the business to tolerate disaster without affecting financial growth.
While setting the RTO, a company must check the downtimes that may affect your organization in many ways. It is used to study viable strategies to continue your business operations even after a disaster. When customers face any disturbances in the application, they ask how much time an app will take to get back to the action. The answer is RTO for every organization.
Example: Suppose you are an online transaction company like PayPal or Pioneer facing unpredictable events. In this case, your RTO will be quick enough to recover the operation.
In other words, a company sets its RTO to an hour or two to avoid consequences in the form of finance or data.
RPO
Recovery Point Objectives (RPO) is the data loss that an IT infrastructure can handle in terms of the time and amount of information.
Confusing?
Take an example of a database that records transactions of a bank, including transfers, scheduling, payments, and more. When a disaster happens, the database is recovered in real-time. The difference between the database at the time of disaster and the database recovery after a disaster is zero in this case.
For some companies, it is acceptable to take about 24 hours to recover all the information from the backup, but it can be catastrophic sometimes. It is essential to set your infrastructure according to the RPO requirements. This includes enhancing the frequency of the backups, adding a standby database into your architecture, and more.
Failover
Think of a situation where you are traveling a long distance. Suddenly, you got a flat tire due to some unexpected reason. You thank the spare tire available in your vehicle and the tools to change the defective tire.
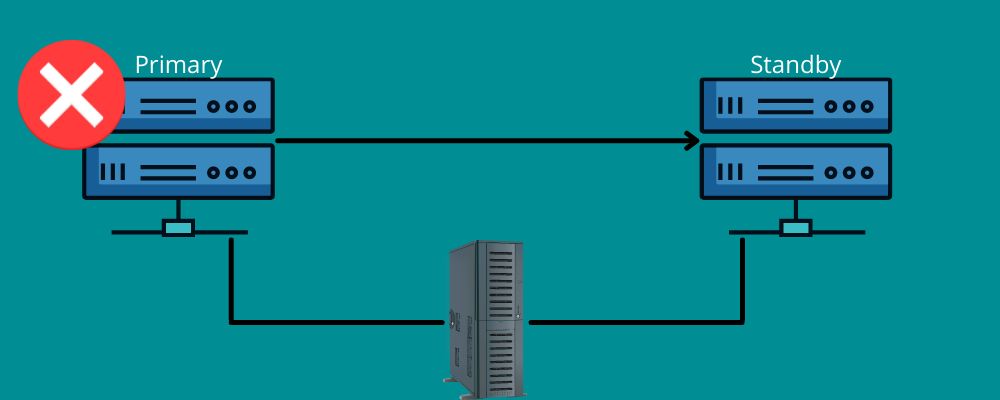
Failover works in the same manner.
It means you need a backup connection during the disaster. In a nutshell, failover means having networks and systems that you can use at the time of a disaster to switch your information to the recovery system.
Failover ensures all your services are running smoothly, even if there are infrastructural or hardware failures. This way, you can prevent your organization from losing data and revenue and avoid service disruptions for your end-users.
You can either set it manually or allow it to function automatically to move the data to the standby server.
Failback
IT failback is a simple operation where the original production goes back to its original place (system) after a disaster is handled. During the attack, companies follow a failover operation due to which all the workloads transfer to a VM replica or backup system.
However, you can not just skip the next step of returning. When you recover everything and get back into action, you need to transfer all the workloads to their original VMs or systems. This overall process of returning the workloads to the original workplace or system is known as failback. It means you are coming “back” after the attack.
Failback is also used for the scheduled maintenance of an enterprise. It is true that failback always occurs after failover. In other words, failover is the first step, and failback is the second step in recovering essential data. It can be set up between cloud to cloud, on-premises to on-premises, on-premises to cloud, or any combination from these.
DR
Disaster Recovery (DR) is the process where you have pre-built plans to recover your assets within the timeframe.
DR gives the ability to an organization to respond fast and recover every single service from an unexpected event. It also gives formal documentation that contains instructions on taking immediate actions in the case of unforeseen incidents.
BCP
Business Continuity Plan (BCP) is one of the most acceptable disaster recovery plans that allows IT infrastructure to make strategies in order to handle IT disruptions to servers, mobile devices, personal computers, and networks.
BCP is slightly different from disaster recovery as it helps an organization make plans to reestablish enterprise software and productivity to meet key business needs.
Here, a company creates a recovery system to overcome potential threats, such as cyber-attacks or natural disasters. It is designed to secure assets and ensure all the services will be back in action quickly after the strike.
BCM

Business Continuity Management (BCM) is a risk management process specially designed to act as a shield against threats to business processes. BCM is the next step of BCP, where it validates the recovery plans to make sure everyone in the business responds to the plan instantly and recovers all the essential stuff.
BCM acts as a management framework to identify infrastructure risks when it faces external and/or internal threats. It also ensures that the framework works efficiently with the help of regular testing to enhance predictability, reduce risk, and align the plan for future attacks.
BIA
Business Impact Analysis (BIA) is the process of analyzing the survival rate of a business by identifying crucial systems, operations, and processes. It tells about the effect of a disaster on your organization due to the interruption in your operations.
BIA predicts the consequences before an attack actually happens in order to collect key information that can help create powerful recovery strategies. It also identifies the cost involved due to the failures, such as replacement cost of equipment, loss of cash flow, profits, salaries, and more.
When creating a BIA report, you must consider the crucial processes involved in your business, the impact of disruptions to different areas, acceptable duration, tolerable areas, financial costs, and more.
Call Tree
A call tree is a process of curating a list of staff to call upon during an emergency. It is a procedure that follows a tree-like structure.
For example, during a disaster, one person will contact a small group of members with an urgent message, those staff members call each group separately. This way, all the staff will get informed during the threat and start their assigned job to recover every function and process in time. Making a list is simple but implementing it in real-time creates confusion.
You must perform regular call activities to prepare every emergency staff member to stay alert. Regular testing can also help identify changed or missing numbers that can severely impact performance.
A call tree contains information to be used during an emergency to deliver instructions. It can also be done manually, but people use automation to accelerate the process and notify the members in today’s digital world.
Command Center/Control Center
It is a virtual or physical facility specially prepared to provide command or control over the recovery plans during a crisis. It communicates with the team to manage the systems and functions during the disaster.
Traditionally, infrastructure depends on the command center dealing with crises without any proper approach. Nowadays, organizations have designed their control center perfectly, which turns the immediate response to core competency.
Once it senses a disaster, the command center rapidly drives towards the recovery phase. Moreover, it serves as the reporting point in the case of services, press, deliveries, and more. It also brings together people from multiple disciplines during such scenarios.
Incident Response

Incident response is a type of response given to deal with an attack. It is done with the help of the right procedures and personnel to preserve network and data security effectively at the right time.
If an organization has an incident plan prior to the unexpected event, it can secure its data from threats in real-time. The incident response specialists always stay alert to the problems and act naturally during an incident. They take certain measures to avoid security breaches, ensuring they skip not a single step during disaster recovery.
In the beginning, you must determine the critical data and store it in the cloud or any remote location to ensure safety. Address current infrastructure needs and evolving cyber threats by updating incident response plans regularly.
Backup
Backup solutions help an IT infrastructure to maintain copies of data and store it securely at the right time. If you face database corruption, accidental deletion of all the data, or any other problem, you must be ready with the backup to restore the data instantly and keep going with the services.

It involves replicating the files and storing them in a secure location to access all the data easily after an unusual event. It will help if you back up your data in multiple locations to ensure you can restore it even if a site fails.
Resilience
The ability of communities, states, organizations, and individuals to resist or withstand a disaster without compromising the services and systems is known as disaster resilience.
An organization must be prepared to withhold a large amount of stress due to the hazards. Ensure you have the capabilities to minimize your losses with better planning instead of waiting for someone to come and rescue you. This will help you accommodate the disasters and efficiently recover your IT infrastructure.
Here, the main goal is to preserve and restore the essential functions and structures at the right time whenever necessary. To become a disaster-resilient organization, you must prepare in advance and have the ability to anticipate risks, adjust to changes, share and learn, integrate various sectors, and manage risk levels.
SLA

Service Level Agreement (SLA) is a disaster plan in which you mention to the end-users the time you may take to restore services during an emergency.
SLA ensures customers that their data is safe and not compromised or shared with third parties. It is the single point of contact with the end-user issues.
Every IT infrastructure gives assurance about SLA to its customers. So, Make sure you communicate with your end-users beforehand.
SPOF
A Single Point of Failure (SPOF) is a piece of equipment, an individual, resource, or application to which many other systems or applications are connected.
If such a piece of equipment or resource goes down, all the essential parts connected to the system go down with it. Thus, the entire process and business operation will be affected.
Therefore, you must have a strategy to handle such a problem to keep your organization running. The very first thing you can do is identify that single piece of equipment or system that can impact more. Next, run a business impact analysis and get a risk assessment score to be aware of the scenes going to happen. Dig in and find them before the event.
Once you list all the SPOF, classify them according to the recovery process. Put each one of the SPOF in three different categories:
- Recover easily and directly with less time and budget.
- Recovery would be difficult, but a reliable process could be developed to restore.
- Nothing can be done to recover once it goes down.
You can act accordingly based on the category.
System Recovery
During hardware failure, you must run a recovery process to retrieve the particular system or server to its original form. And to recover the entire system, you need to be ready with recovery requirements, backups, firmware compatibility, and hardware compatibility.
System recovery is a process that resets the machine into its previous settings or the same state as it was when new. Doing this will wipe out all virus infections due to installed software or applications in your system.
This process includes recovery planning of an IT infrastructure that sets and follows certain procedures to ensure data availability against man-made or natural disruptions.
System Restore
System restore is a recovery tool that allows you to restore certain files and information to their previous state at the right time.
With system restore, you can recover registry keys, installed programs, drivers, system files, and more back to its previous version. This acts as a lifesaver in many disasters.
Test Plan
It refers to a document that stores information on a test strategy, estimations, resources, deadlines, objectives, and schedules. It works as a blueprint that runs tests to ensure hardware and software safety.
This includes various tests according to the procedures and steps planned to manage disaster after-effects. Perform the regular tests in order to prepare yourself and your organization not to skip a single step during the course of action. This way, an IT infrastructure can understand the shortcomings and be ready for the fight.
Conclusion
No one knows when a disaster will happen. Therefore, proper safety and security measures are essential for every business.
Disaster recovery terminologies will help you understand how to respond to attacks and disasters. It will also help you prepare in advance so you can safeguard your infrastructure during an unexpected event. You will be able to create an effective, real-time disaster recovery strategy to save millions of dollars and withhold customer trust.



