Do you believe this famous saying?
“A coin has two sides” or “There’s no rose without a thorn.”
It makes sense to me.
Let’s take the example of technology.
While technology has the power to transform the way we live, it also has the potential to take it all back.
That’s right!
Cyberattacks have become so frequent that you could see a new headline flashing every second day about a high-profile organization becoming the victims.
Not only are organizations suffering, but many public figures as well. Money and fame, everything could be at risk due to cybercriminals spoofing around. And the irony is that its solution also lies in mighty Technology itself. The technology to counteract such malicious activities could be firewalls.
A firewall is a protective barrier that can protect your network by preventing unauthorized access. With the number of attacks rising high, the global market for network performance management reached $11 billion in 2019, says this report.
It has many types, including network firewalls, software, cloud, and hardware-based firewall, application firewall, and more.
So, sometimes it becomes confusing to differentiate between network and application firewalls.
But not anymore; because in this article, I’m going to discuss that and put some more light on network firewalls and recommendations for it.
Stay tuned!
What is a Network Firewall?

A network firewall is a system that is capable of controlling access to your organization network and thereby protects your network. It acts as a filter to block non-legitimate incoming traffic before it could enter your organization’s network to cause damage.
Its major purpose is to provide protection to an inside network by separating it from the outside network. It also controls the communications between both the networks.
The different types of network firewalls are:
- Packet filters: They are traditional firewall systems that rely on packet attributes such as IP address of source and destination, protocols, and ports associated with individual packets. These attributes determine whether the packet or inkling traffic must be given access through the firewall or not.
- Stateful inspection firewalls: these firewalls have added capability of inspecting packets belonging to a complete session. If a session is perfectly established between two end-points, it permits communication.
- Application layer firewalls: they can examine application-layer information like an HTTP request, FTP, etc. If it finds some non-legitimate applications, it can block them right there.
- Next-generation firewalls: They are advanced firewalls with deep inspection capabilities beyond protocol or port blocking and inspection. It includes application-level inspection, intelligence, intrusion prevention, web application firewalls, etc.
How is it different than the Application Firewall?
Not every firewall is capable of protecting your system from all sorts of threats. For this, businesses consider using mainly two types of firewalls – network firewall and web application firewall (WAF). It’s important to understand the difference between these two firewalls to ensure better security for your network.
For this, let’s understand a bit about WAF in the first place.
A Web Application Firewall (WAF) can protect web applications from vulnerabilities unique to web applications and HTTP/S security loopholes.
In IT, digital security is divided into seven layers. WAFs provide the 7th layer of security, which is also termed as application-layer security.
Web applications are targeted with different attacks, including:
- Distributed Denial-of-Service (DDoS)
- Cross-site Scripting (XSS)
- SQL injection
- Brute force
- Spam
- Session hijacking
Difference
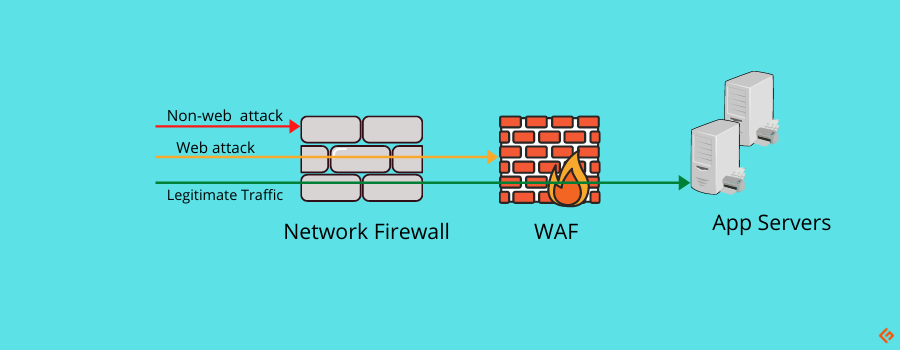
- Security Layer: Network firewalls perform at layer 3-4, which includes vulnerabilities associated with the incoming and outgoing network traffic as well as data transfer. WAFs operate at layer 7, which includes application-specific vulnerabilities, as mentioned above.
- Focus: Network firewalls are focused on protecting inbound and outbound traffic, whereas WAFs protect applications.
- Operation Mode: Network firewalls utilize two methods of operation – transparent and routed modes. WAFs operate on – active inspection and passive mode.
- Placement: Network firewalls are placed on the network perimeter, whereas WAFs are placed close to the Internet-facing applications.
- Attack protection: Network firewalls protect from vulnerabilities like less secure zones and unauthorized access. WAFs protect from SQL injections, DDoS, and XSS attacks.
- Algorithms: Network firewalls use algorithms like packet filtering, proxy, and stateful inspection. WAFs use anomaly detection, heuristics, and signature-based algorithms.
How does it help to Stop Attacks at the edge?
A network firewall controls the flow of data and traffic to or from your network. These data are known as “packets,” which may or may not contain malicious codes to damage your system.
During busy days or peak holiday seasons, hackers bombard your network with malware, spam, virus, and other malicious intent.
At this time, your firewall applies a certain set of rules on the incoming and outgoing network traffic to examine whether they align with those rules or not.
- If it matches – the firewall allows the traffic to pass-through.
- If no – it rejects or blocks the traffic.
In this way, your network remains perfectly safe from any sorts of threats, be it internal or external.
Did I say internal?
Yes, the firewall is not just for the Internet-facing network but internal too. Remember, most of the attacks initiate internally, so ensure to implement firewall strategy wherever possible.
How to make the most of your firewall?
Are you new to using a network firewall?
If yes, then follow some firewall hacks to use your firewall effectively.
- Inspect the coverage of the firewall: If you have changed something on your network lately, do not forget to check all the systems that the firewall covers. Examine whether they are still protected or not to fix things immediately before the damage is done.
- Keep an eye on connected devices: If you or your employees connect a smartphone or any other device to the network, then it is necessary to protect them. For this, try installing a personal firewall on these devices to protect your data.
- Isolate your payment system: Safeguard your payment streams by keeping them away from vulnerabilities. For this, set your firewall, so it stops all kinds of untrusted data transfer to/from your payment systems.
Permit things that are of utmost necessity for card processing and sales while prohibiting direct communication between these systems and the Internet.
What are some of the popular cloud-based network firewalls available?
Let’s explore!
Google Cloud
For each Virtual Private Cloud (VPC), Google Cloud generates default rules for firewalls at the network level. These rules allow you to accept or reject connections to/from your VM instances, depending upon the specified configuration.
When the firewall rules are enabled, it protects your instances irrespective of their operating system and configuration. Even though your VM instances are not started, they are still safe.
The VPC firewall rules of Google Cloud are applicable between your VM instances and outside network and also between themselves.
Highlights
- A network is given 2 implied firewall rules to block incoming traffic and permit outgoing traffic
- Priority levels ranging between 0-65535 are supported
- It supports only IPv4 connections
Check out how to implement a firewall on Google Cloud.
Barracuda
Secure your network Infrastructure by using the Barracuda CloudGen Firewall. It offers scalable and centralized management in addition to sophisticated security analytics to help reduce your administrative overhead.
The firewall can also enforce granular policies to protect the whole WAN. It is ideal for managed service providers, multi-site enterprises, and other firms with complicated and distributed network infrastructure. Block zero-day and advanced threats capable of bypassing antivirus engines and signature-based IPS.
Highlights
- Application profiling
- Web filtering
- Intrusion detection and prevention
- Anti-spam and malware protection
- DoS and DDoS protection
- SSL interception
- Complete access control on the network
- Authoritative DNS and DNS server
Check Point
Get superior security with Check Point, which delivers the award-winning solution SandBlast Network. It protects your network from advanced multi-vector attacks of 5th generation, better than most firewalls offering 3-4 levels of protection.
Check Point’s NGFW includes 60 , innovative security solutions. It is based on the new Infinity Architecture that can prevent attacks of 1.5 Tbps. Moreover, it focuses on preventing both the application layer and malware attacks.
Highlights
- Zero-day protection
- On-demand scaling
- Unified security across clouds, networks, and IoT
- Modular hardware
- Customization for expanding slots
- Solid-state drives to boost performance
- Broader coverage for your network, mobile, cloud, and endpoints
- Granular network-based DLP with 700 data-types for FTP, email, and web traffic
- Centralized management control
Zscaler
Using the Zscaler Cloud Firewall, you can enable secure local network breakouts for the entire protocols and ports without appliances. It is capable of scaling elastically to manage your traffic.
The firewall can deliver real-time control, visibility, policy enforcement immediately across your network. It can also log each session in-depth and uses advanced analytics for insights into network vulnerabilities from the same console for all applications, locations, and users.
Highlights
- Granular policies
- Proxy-based architecture
- Cloud IPS
- DNS security
- SSL inspection
- Delivers Firewall-as-a-Service (FaaS)
- Optimizes MPLS backhauls
SonicWall

Businesses ranging from small enterprises to global giants cloud infrastructure can use the tight security firewalls of SonicWall.
They can address your specific security needs and usability at a reasonable price to secure your network. You can add an extra layer of security with SonicWall’s Advanced Gateway Security Suite (AGSS) that offers complete security services and customization options.
Highlights
- Gateway Security Services (GSS) to protect against anti-spyware, anti-virus, intrusion prevention, application control, etc.
- Content filtration to block inappropriate, malicious, and/or illegal web content
- Capture Advanced Threat Protection (ATP)
SophosXG

SophosXG is undeniably one of the leading network security firewalls out there. It provides powerful next-gen protection by leveraging technologies like intrusion prevention and deep learning to safeguard your network.
Its automatic threat response isolates your systems instantly on identifying security threats in order to contain it from spreading. Additionally, the firewall has high visibility into suspicious traffic to help you control the network.
Highlights
- Easy-to-use VPN for free
- SOHO protection including SD-RED or XG 86
- Mobile VPN with SSL and IPSec
- Encrypted traffic with TLS 1.3 support
- High-performance DPI Engine
- Network Flow FastPath
- SSDs, flexible connectivity, and generous RAM
- Central cloud management with reporting tools and Zero-touch deployment
Cisco
Reputed by top research and advisory companies like Gartner, Cisco is one of the market leaders in firewalls. Stay protected from increasing online vulnerabilities by choosing the Cisco NGFW.
It also simplifies security management and lets you gain better visibility across hybrid and distributed networks. The NGFW utilizes integrated security and networking capabilities into the existing infrastructure to provide extended protection.
Highlights
- Virtual NGFW capable of inspecting threats of more than 1Gbps
- Adaptive Security Virtual Appliance (ASAv)
- ASA with FirePOWER
- Meraki MX Series appliances
- Next-gen intrusion prevention
- Firepower management center and device manager
- Cisco Threat Response & Defense Orchestrator
- Cisco SecureX for strengthening the security
Fortinet
Fortinet NGFWs can address the security concerns of an organization. They leverage artificial intelligence to provide proactive threat detection and prevention. Its firewalls are highly scalable and can meet the needs of hybrid IT network architectures.
Fortinet firewalls inspect both encrypted and clear-text traffic to protect your security dome. Besides, they can prevent DDoS attacks, ransomware without affecting user experience or downtime troubles.
Fortinet is available as an appliance and virtual machine.
Conclusion
Protecting your network from malicious intent, both external and internal, has become evident more than ever due to rampant secure invasions. Don’t panic; instead, go for a high-quality network firewall and safeguard your network and data to have peaceful nights!
Next, learn Network Security.



