In the game of network security, you are either secure or you are not; there exists no middle ground.
If a computer is connected to the Internet connection, it is vulnerable to online attacks. The only difference is some computers could be more susceptible than others.
Look at this global cybersecurity statistics to get a clear picture – a Veronis report highlights that cybercriminals attack the internet every 39 seconds and 2,244 times daily on average. Data breaches had already exposed about 4.1 billion data in 2019.
All kinds of businesses, no matter what their sizes are have become a target, especially small scale businesses. It impacts their reputation, costs them in millions, and compromises their customer data.
This information is enough to understand that a barrier must be there to protect users from threats coming online.
The barrier we are going to talk about in this article is a Firewall.
So, let’s put some light on this important aspect of network security.
What is a Firewall?
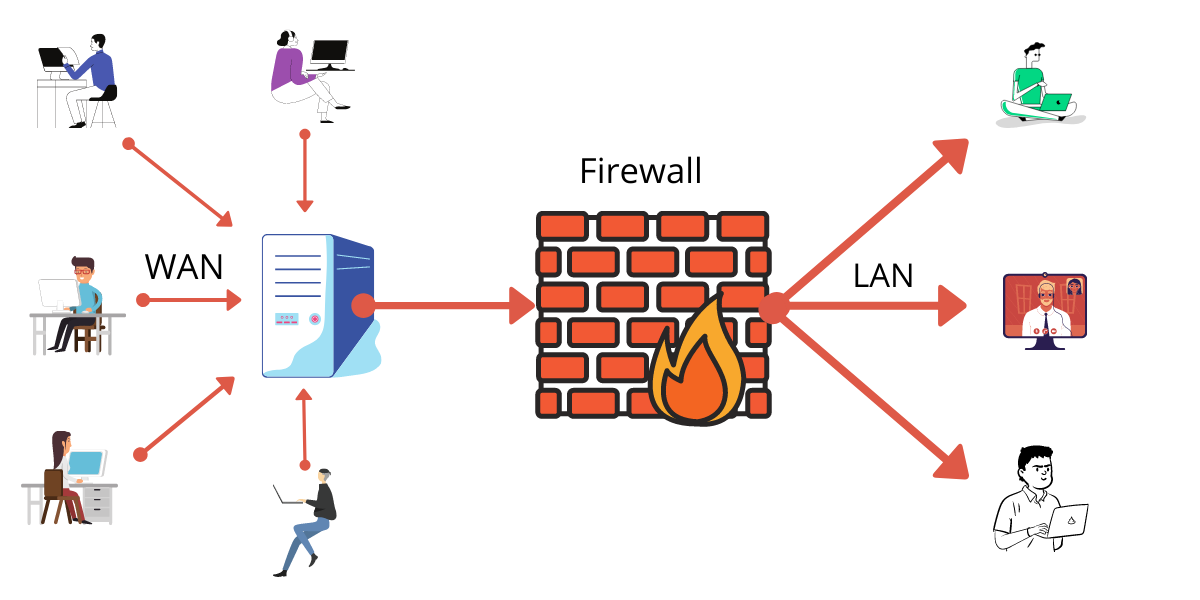
In the computing language, a firewall is a security software or hardware that can monitor and control network traffic, both incoming and outgoing. It establishes a kind of barrier between reliable internal and unknown external networks.
Therefore, a firewall, also known as a network firewall, is capable of preventing unauthorized access to/from private networks.
A network firewall is based on security rules to accept, reject, or drop specific traffic. The aim of the firewall is to allow or deny the connection or request, depending on implemented rules.
Firewalls History
There’s an interesting story about the name “firewall”.
A firewall is inspired by a tangible object known as a “firewall” or a fire retaining wall. It is installed inside buildings, separating two apartments. So, in the occurrence of fire, the firewall can prevent the fire from spreading from one apartment to another.
The application of this term in computer networking began back in the 1980s. At that time, the internet was newly based on connectivity and global usage. In fact, routers were the predecessors of firewalls because then it used to separate one network from another.
Packet filters
A first-generation network firewall used to monitor packets, in other words, bytes transferring between computers. They are still used today, but modern firewalls have traversed a long path with technological development.
Stateful filters
Second-generation firewalls that came around 1990 that perform the same work as packet filters do besides monitoring activities between two endpoints. Stateful filters are vulnerable to DDoS attacks.
Application layer
The third generation firewall that could understand protocols and applications like FTP, HTTP. Hence, it could detect unwanted applications trying to bypass the network firewall.
Next-generation firewall (NGFW)
It is a deeper or advanced inspection of the application layer, which includes intrusion prevention systems (IPS), web application firewall (WAF), and user identity management.
Types of Firewalls?
You can find different types of firewalls, and sometime it might be confusing. Here are some of the popular firewall types you’ll often hear.
- Network firewall
- Web application firewall
- Hardware-based
- Software-based
- Cloud-based
- Personal computer (Windows, macOS) firewall
- Mobile firewall
They are mostly categorized under two types – network-based and host-based.
Network-based vs. Host-based firewalls
Network-based firewalls
These perform on network levels and filter all the traffic coming and going across a network. They filter traffic by checking against firewall rules and protecting the network. A network firewall is usually installed at the network edge and acts as the first layer of protection to block any unwanted traffic which shouldn’t be entering the datacenters.
Host-based firewalls
They are installed on different network nodes, controlling each outgoing and incoming packet or byte. The firewall consists of an application suite installed on a server or computer.
Host-based firewalls can protect the individual host against unauthorized access and attacks.
Hardware vs. Software vs. Cloud Firewall
Hardware-based firewall
A dedicated firewall that is installed within your network and all the traffic traverse through this device. It could be an expensive implementation but often required in an organization to protect their networks.
Some of the popular hardware firewalls come from Cisco, SonicWall, Fortinet.
Software-based firewall
It is usually a virtual appliance or VM with firewall software installed. There is plenty of open source firewall you can explore. They are customizable but offer lesser control over protection features and functions than hardware.
pfSense is one of the popular open-source software-based firewalls.
Cloud-based firewall

Firewalls leveraging cloud solutions are cloud firewalls, pretty self-explanatory, right?
You can also call them Firewall-as-a-Service (FaaS), and they are similar to proxy firewalls. In addition to providing a strong shield to your network, they are excellent to scale with the growth of your company.
SUCURI, Cloudflare, Imperva, Sophos are some of the popular cloud-based firewalls.
How does a firewall work?
A firewall maintains a set of rules which are applied to both incoming and outgoing traffic. It matches the traffic against those rules, and if the rules are matched, it initiates the access.
For outgoing traffic originating from the server, the firewall lets them pass mostly (configurable). But for incoming traffic reaching from major protocols like TCP, ICMP, or UDP, the firewalls monitor them strictly.
The firewall inspects incoming traffic based on their:
- Source
- Content
- Destination
- Port
The firewall uses this data to decide whether the traffic abides by the set rules. If yes, then it permits; otherwise, the traffic gets blocked by the firewall.
Who needs a Firewall?
Everyone!
It’s a common misconception that only large firms or financial institutions must use firewalls. But the reality is different; every business must use a firewall irrespective of their size.
A report says that 60% of SMBs that have been victims of cyber-crime went out of their business within six months.
Not to mention, cyber-criminals are always on the go to evolve their techniques and finding advanced ways to target businesses.
Without using a firewall, your network and data are potentially at major risks and vulnerabilities to malicious intent. Malware can steal your credit card data, bank credentials, customer information, destroy data, bring down your network, divert hardware bandwidth, and many more.
Hence, firewalls act as absolute saviors in these scenarios. Both consumers and corporations can use firewalls.
Companies can use firewalls into their security information & event management strategy, cybersecurity devices, etc. You can also install them in your network perimeter for guarding against external security threats or inside the network for segmenting and protecting against internal threats.
You can use a personal firewall, which is a single product consisting of software or embedded firmware device. Use it to:
- Set restrictions in your in-home devices,
- While surfing the internet using a broadband connection which is always on,
- While using public Wi-Fi in an airport, park, or cafe
- If a program tries to connect with the internet, etc.
What are the benefits of Firewalls?
Installing a firewall in your network can suppress all the jitters associated with your computer’s security.
I guess you get an idea by now, but let’s explore more.
Safer network
By monitoring traffic entering the network, a firewall keeps your network safe. By employing a 2-way firewall, you can also enjoy double-duty protection as it monitors both incoming and outgoing traffic.
It keeps an eye on every packet, and on finding a hazardous packet, the firewall blocks it then and there.
Protects from Trojans

Trojans or Trojan horses are a type of malware that is dangerous for your computer. They silently sit on your system and spy all the files present in it. What’s more, it accumulates the information and sends it to a destined web server.
But you would not have a slight hint about what’s going on your computer until it starts showing its repercussions.
No worries if you have installed a firewall on your system as it can block Trojans immediately before they can enter and damage your computer.
Stop hackers

Hackers are always waiting for network loopholes. Once they see it, there’s no looking back. They will target those systems and carry out malicious activities like spreading the virus through a botnet, key-loggers, and so on.
Apart from this, even your neighbors whom you might not suspect could advantage from your open network connection.
A firewall is key to all these problems and provides you with a secure network free from such intrusions.
Access control
Firewalls include access policies that you can implement for certain services and hosts. The reason is attackers may exploit some hosts, and hence your network becomes vulnerable too.
So, blocking such hosts is the solution here. You can enforce access policy on these hosts or services with the help of firewalls.
Points to consider while choosing a Firewall
At this point in the article, you must have understood the importance of having a network firewall.
So, if you have made up your mind on staying secure by leveraging it, there are some things that you should consider before you make a purchase. It will help you pick the one that can justify your network needs.
DDoS Protection
DDoS attacks are on the rise and have already claimed major websites, leading them to go offline for extended hours.
These attacks come to happen with no warning where even the IT ninjas could not anticipate until the harm us has done already. It suddenly reduces the performance and bandwidth of attacked websites.
Hence, always go with a firewall that can offer or integrate with DDoS detection as well as prevention. You can also pair it with an intrusion detector to have an extra layer of protection and say no to malicious traffic.
Alerting
Just relying on firewalls is not enough; you need to know when threats are inline. For this reason, choose a firewall capable of sending attack alerts to your system administrator before it could pose any harm.
Attack alerts remind you to check your firewall quickly to see what’s going on. It can also help you to determine the attack method. Hence, you can utilize this knowledge along with the firewall to mitigate any threat when you still have time.
Remote access
No one is untouched with the waves of remote work these days, and they are mostly IT sector employees. But, if you allow them to access the company network remotely, it may involve security risks.
In this case, firewalls handle activities concerning VPNs for authorization, support, etc. While you have the option to buy a VPN solution, combining a firewall with VPNs within the architecture is better and cost-efficient.
Cost

Thanks for the options available.
Depending on the budget and requirement, you can use hardware or software-based firewalls.
If your application is hosted on the cloud platform, then leveraging a cloud-based firewall will be a good idea. There are plenty of choices and choose what works well with your application.
Trust me, the cost of a data breach is way more than investing in a decent firewall. So, don’t try to save the money here.
Conclusion
Firewalls are the first line of defense in your network. If that line of defense is not maintained, it could cost you millions or harm your reputation. But there’s nothing to worry; if you are using a decent firewall, you can stay secure from external threats.



