Many people around the world are becoming interested in the hacking world. This might be due to sci-fi movies or other futuristic titles that have attracted users to learning how to hack. There are several exploitation tools in Kali Linux 2020.1 for practicing this skill. This article lists some of the most well-known and reliable exploitation tools out there. All of these tools are open-source and can be downloaded from anywhere in the world.
Metasploit Framework Console msf
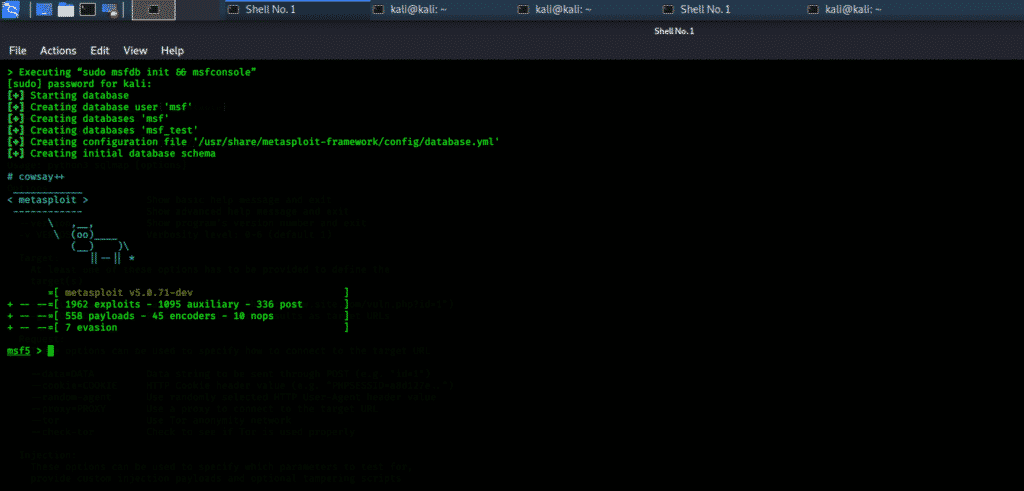
Metasploit Framework is a penetration testing tool that can exploit and validate vulnerabilities. This tool contains the basic infrastructure, specific content, and tools necessary for penetration testing and vast security assessment. Metasploit Framework is one of the most famous exploitation frameworks and is updated on a regular basis. New exploits are updated as soon as they are published. This program contains many tools that are used for creating security workspaces for vulnerability testing and penetration testing systems.
Metasploit Framework can be accessed in the Kali Whisker Menu, and can also be launched directly from the terminal.
Check the following commands to see the various tools included in the Metasploit Framework.
$ msfd -h
$ msfdb
$ msfrpc -h
$ msfvenom -h
$ msfrpcd -h
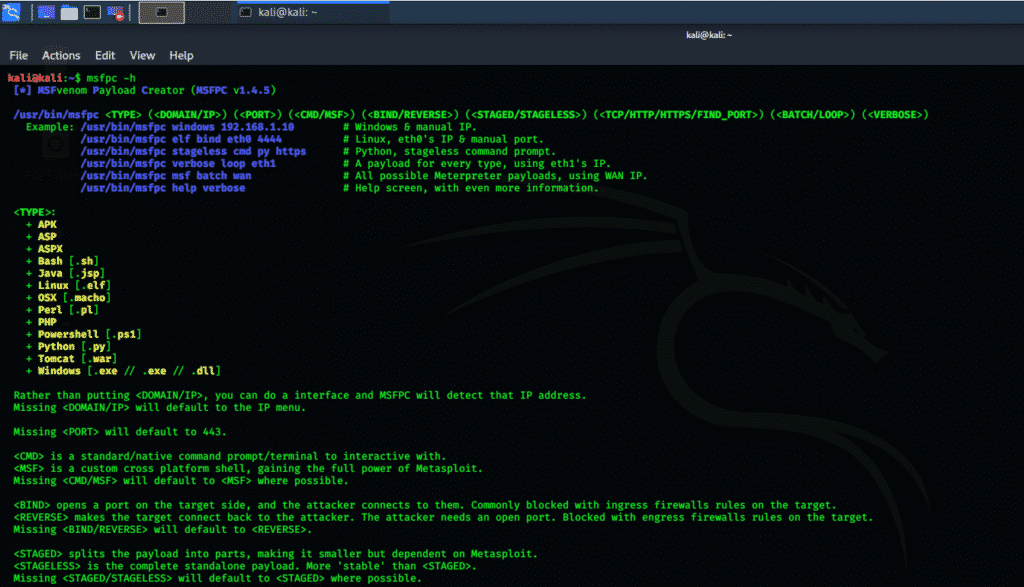
MSFPC
MSFPC is a package that contains several tools that can generate various payloads based on user-specific options. This package is also called the MSFvenom payload creator, and its goal is to automate the processes involved in working with Metasploit and msfvenom. The MSFPC help command can be launched using the following console command.
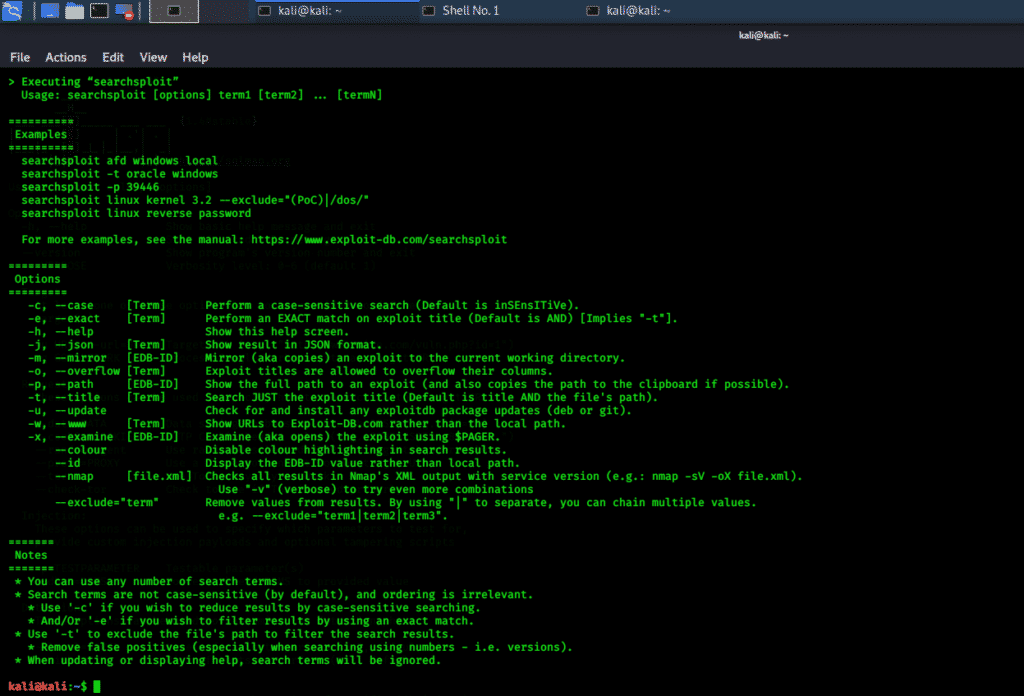
searchsploit
Searchsploit is a search tool for the Exploit-DB Framework that can execute detailed offline searches on a local machine. This method is useful in security testing and can be used for evaluating a network that does not have access to the internet. There are many vulnerabilities within the network, stored in binary files, that can be sought out using Exploit-DB binary searches.
Searchsploit is a console-based tool that can be accessed both from the Kali Whisker Menu and the terminal window.
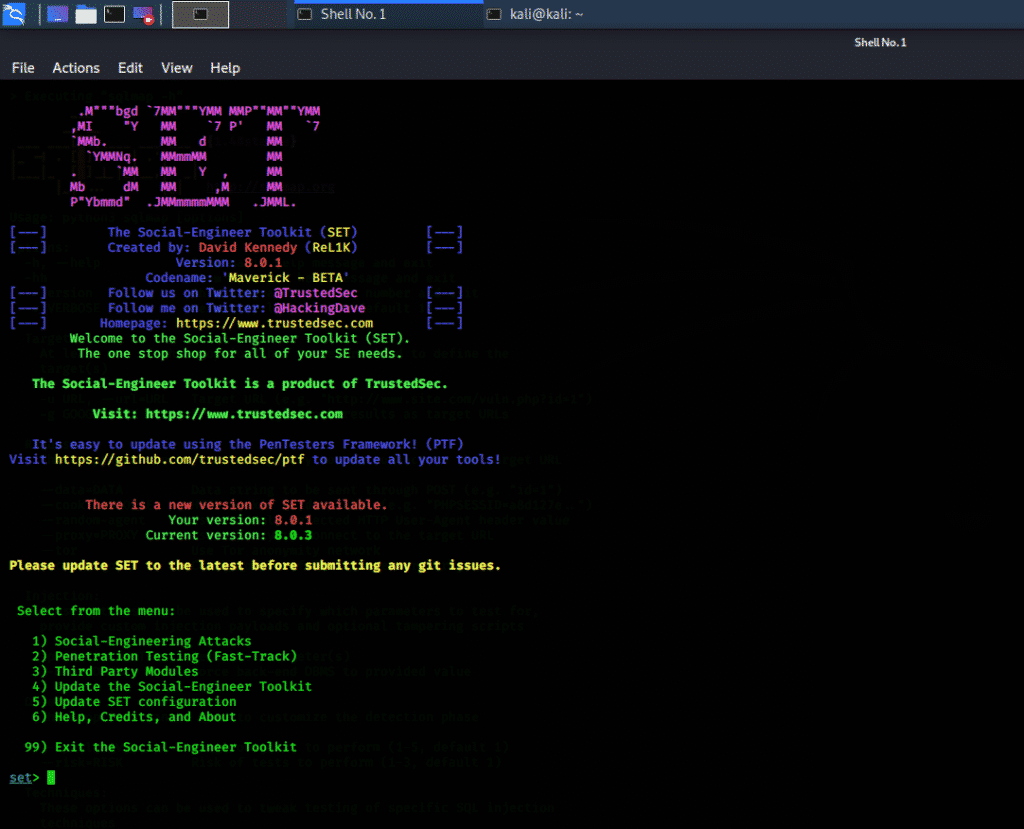
Social Engineering Toolkit/SET
Social Engineering Toolkit (SET) is an open-source, free-ware, penetration testing tool for social engineering and custom attacks. Social Engineering Toolkit contains several custom attack vectors that can help in making a successful attack in no time. This program is very fast and has two main types of attacks: social engineering attacks and penetration testing – or fast-track – attacks. This program can be started directly from the terminal window using the following command.
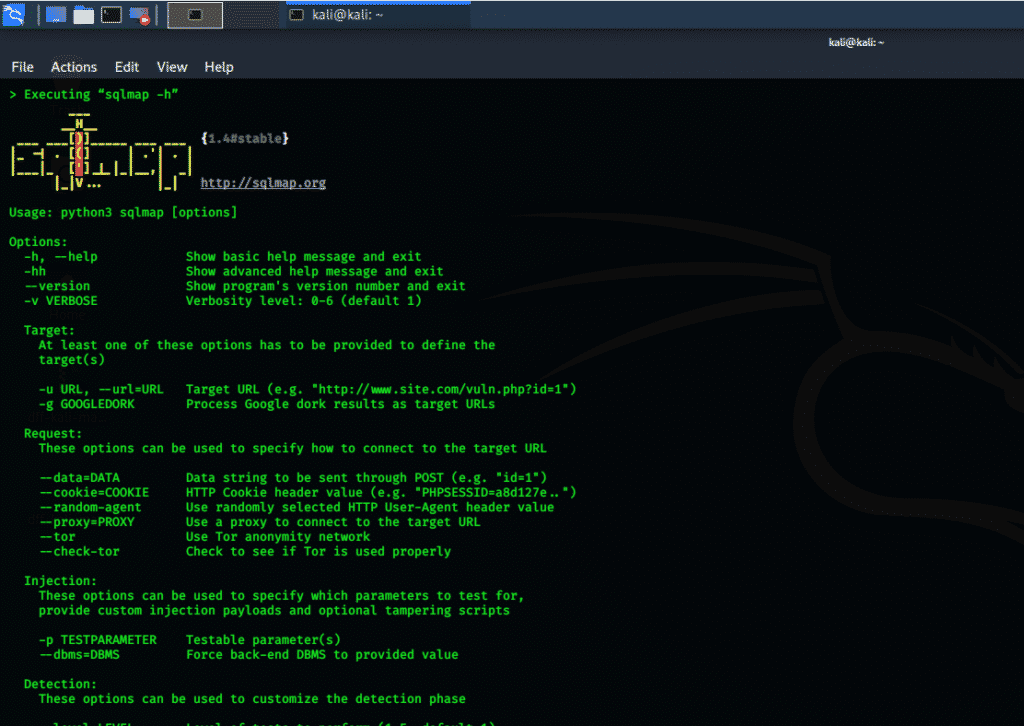
sqlmap
Sqlmap is one of the most popular open-source exploitation tools for SQL injection. Sqlmap automates the detection process and exploitation flaws of SQL database servers. This tool has a very powerful detecting engine. Sqlmap also provides a wide range of switches, from database fingerprinting to accessing the complete underlying file system. This program executes commands through out-of-band connections, and is the ultimate tool for penetration testing.
Features of this tool include:
- Full support for the following database management systems: Microsoft SQL Server, PostgreSQL, Microsoft Access, MySQL, SQLite, Oracle, and Firebird
- Provides support to various SQL injection methods
- Can bypass SQL injection and get access to the database
- Dictionary-based attacks for password hashing and cracking
A number of functions are included in the sqlmap framework, such as injection, detection, methods, enumerations, operating system access, and sqlmap shell.
Conclusion
In this article, we identified the most important exploitation frameworks and tools in Kali Linux 2020.1. All toolkits and frameworks discussed in this article are open-source and provide features that are necessary for every pentester.
About the author
Younis Said
I am a freelancing software project developer, a software engineering graduate and a content writer. I love working with Linux and open-source software.