John The Ripper is an open source and very efficient password cracker by Open-Wall. It was originally built for Unix but is now available for fifteen different platforms including Windows, DOS, BeOS, OpenVMS and Unix like operating systems. It is an Open Source tool and is free, though a premium version also exists. Initially, its primary purpose was to detect weak password configurations in Unix based Operating systems. Today it supports cracking of hundreds of hashes and ciphers.
Installation
John The Ripper can be installed in many ways. Few common ones are here:
We can install it by using apt-get or snap. Open up the terminal and run the following commands.
ubuntu@mypc:~$ sudo apt-get install john -y
This will initiate an installation process. Once it finishes type ‘john’ in the terminal.
ubuntu@mypc:~$ john
John the Ripper 1.9.0-jumbo-1 OMP [linux-gnu 64-bit 64 AVX2 AC]
Copyright (c) 1996–2019 by Solar Designer and others
Homepage: http://www.openwall.com/john/
This means John the Ripper v1.9.0 is now installed on your device. We can see the homepage URL sending us to Open-wall’s website. And Usage given below indicates how to use the utility.
It can also be downloaded and installed via snap. You need to install snap if you do not already have it.
ubuntu@mypc:~$ sudo apt update
ubuntu@mypc:~$ sudo apt install snapd
And then install JohnTheRipper via snap.
ubuntu@mypc:~$ sudo snap install john-the-ripper
Cracking Passwords with JohnTheRipper
So, JohnTheRipper is installed on your computer. Now to the interesting part, how to crack passwords with it. Type ‘john’ in the terminal. The Terminal will show you the following result:
ubuntu@mypc:~$ john
John the Ripper 1.9.0-jumbo-1 OMP [linux-gnu 64-bit 64 AVX2 AC]
Copyright (c) 1996–2019 by Solar Designer and others
Homepage: http://www.openwall.com/john/
Below the Homepage, USAGE is given as:
Usage: john [OPTIONS] [PASSWORD-FILES]
By looking at its usage, We can make out that you just need to supply it your password file(s) and the desired option(s). Different OPTIONS are listed below the usage providing us different choices as to how the attack can be carried out.
Some of the different options available are:
–single
- Default mode using default or named rules.
–wordlist
- wordlist mode, read wordlist dictionary from a FILE or standard input
–encoding
- input encoding (eg. UTF-8, ISO-8859-1).
–rules
- enable word mangling rules, using default or named rules.
–incremental
- ”incremental” mode
–external
- external mode or word filter
–restore = NAME
- restore an interrupted session [called NAME]
–session = NAME
- name a new session NAME
–status = NAME
- print status of a session [called NAME]
–show
- show cracked passwords.
–test
- run tests and benchmarks.
–salts
- load salts.
–fork = N
- Create N processes for cracking.
–pot = NAME
- pot file to use
–list = WHAT
- lists WHAT capabilities. –list=help shows more on this option.
–format = NAME
- Provide John with the hash type. e.g,
–format=raw-MD5, –format=SHA512
Different modes in JohnTheRipper
By default John tries “single” then “wordlist” and finally “incremental”. Modes can be understood as a method John uses to crack passwords. You may have heard of different kinds of attacks like Dictionary attack, Bruteforce attack etc. That precisely, are what we call John’s modes. Wordlists containing possible passwords are essential for a dictionary attack. Apart from the modes listed above John also supports another mode called external mode. You can choose to select a dictionary file or you can do brute-force with John The Ripper by trying all possible permutations in the passwords. The default config starts with single crack mode, mostly because it’s faster and even faster if you use multiple password files at a time. The most powerful mode available is the incremental mode. It will try different combinations while cracking. External mode, as the name implies, will use custom functions that you write yourself, while wordlist mode takes a word list specified as an argument to the option and tries a simple dictionary attack on passwords.
ubuntu@mypc:~$ john password-file -w word-list
John will now start checking against thousands of passwords. Password cracking is CPU-intensive and a very long process, so the time it takes will depend on your system and the strength of the password. It can take days. If the password is not cracked for days with a powerful CPU, it is a very good password. If it is really crucia; to crack the password then leave the system until John cracks it.. As mentioned earlier, this can take many days.
As it cracks, you can check status by pressing any key.
To Quit an attack session simply press ‘q’ or Ctrl C.
Once it finds the password, it will be displayed on the terminal.
All the cracked passwords are saved in a file called ~/.john/john.pot.
It displays passwords in $[HASH]:<pass> format.
ubuntu@mypc:~/.john$ cat john.pot
$dynamic_0$827ccb0eea8a706c4c34a16891f84e7b:12345
Let’s crack a password. For instance, we have a MD5 password hash that we need to crack.
bd9059497b4af2bb913a8522747af2de
We will put this into a file, say password.hash and save it in user: format.
admin:bd9059497b4af2bb913a8522747af2de
You can type any username, it is not necessary to have some specified ones.
Now we crack it!
ubuntu@mypc:~$ john password.hash –format=Raw-MD5
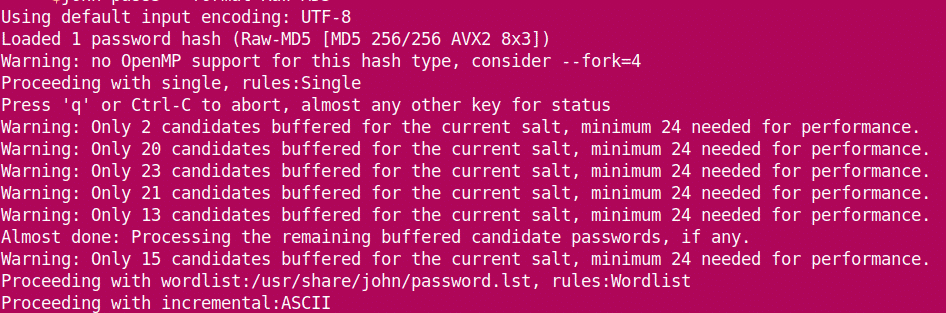
It starts cracking the password.
We see that john loads hash from the file and starts with the ‘single’ mode.
As it progresses, it goes onto the wordlist before moving onto incremental.
When it cracks the password, it stops the session and shows the results.
Password can be seen later also by:
ubuntu@mypc:~$ john password.hash –format=Raw-MD5 –show
admin:emerald
1 password hash cracked, 0 left
Also by ~/.john/john.pot :
ubuntu@mypc:~$ cat ~/.john/john.pot
$dynamic_0$bd9059497b4af2bb913a8522747af2de:emerald
$dynamic_0$827ccb0eea8a706c4c34a16891f84e7b:12345
So, the password is emerald.
The internet is full of modern password cracking tools and Utilities. JohnTheRipper may have many alternatives, but it is one of the best ones available.
Happy Cracking!
About the author

Usama Azad
A security enthusiast who loves Terminal and Open Source. My area of expertise is Python, Linux (Debian), Bash, Penetration testing, and Firewalls. I’m born and raised in Wazirabad, Pakistan and currently doing Undergraduation from National University of Science and Technology (NUST). On Twitter i go by @UsamaAzad14