How do you ensure your application and infrastructure are secure from security vulnerabilities?
Detectify offers a complete suite of asset inventory and monitoring solutions that include vulnerability scanning, host discovery, and software fingerprinting. Its use could help avoid unpleasant surprises, such as unknown hosts that present vulnerabilities or sub-domains that can be easily hijacked.
Many things can go wrong, and an attacker can take advantage of it. Some common ones are:
- Keeping unnecessary ports open
- Exposing insecure subdomain, sensitive files, credentials
- Keeping
.gitaccessible - Potential OWASP top vulnerabilities such as XSS, SSRF, RCE
You can debate that I can manually run the port scanner, find sub-domain, test for vulnerabilities, etc. This is good if you do it once or once in a while, but it will be time-consuming and not cost-effective when you have to do it frequently.
So what’s the solution?
Go for Detectify Asset Monitoring, which monitors your web application’s assets and performs a regular scan for above all discussed and many other checks to keep your online business safe 🛡️.
- Detectify hosts their own private community of ethical hackers to crowdsource vulnerability research so it’s giving you alerts from a real attacker’s perspective.
- Other tools rely on signatures and version testing which is more like compliance than actual security. The Detectify hackers provide the actual payloads which are used to build the security tests, giving a unique set of testing which isn’t seen in other products on the market.
- The result? A more sure-fire way of security testing that only gives you results that can be verified
- Security findings that are actually interesting to fix!
In their blog, they mention that Asset Monitoring test development time has been cut down to as fast as 25-minutes from the hacker to release.

Sounds interesting?
Let’s see how it works.
To begin working with Detectify Asset Monitoring, the first step is to verify that you own the domain you are going to monitor, or you are authorized to perform a security scan. This is a necessary step Detectify takes to ensure the sensitive information it reveals won’t end in the wrong hands.
We can do domain verification in several ways: by uploading a specific .txt file to your domain’s root directory, with Google Analytics, through a DNS record, or with a meta tag on a web page. There’s also an option of assisted verification if none of the self-service methods work for you.
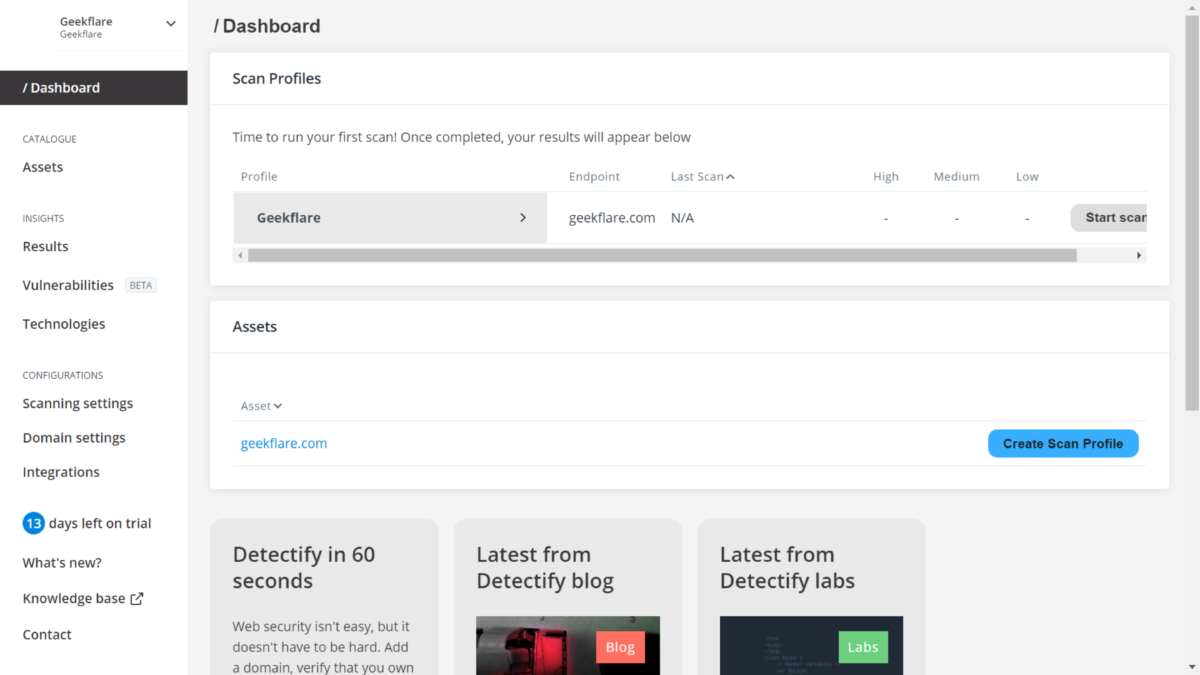
Creating a scan profile
The second step in setting up Detectify is to create a scan profile, which can be associated with any domain, subdomain, or IP address from your site with HTTP or HTTPS services running on it.
After you set up a scan profile, you can configure it with different options.
For example, you can have two profiles associated with the same domain but with different credentials. That way, you can perform two different scans on the same server and compare the results.
Once your scan profile is configured, you’ll be ready to scan, which you do just by pressing the Start Scan button next to the scan profile you want to use. The dashboard will change to show that a scan is in progress.
The time to perform the scan depends on the site contents volume. If the volume is rather large, the scan may take hours, and you may notice a slight degradation of the site’s performance while the scan is in progress. So my advice is to perform scans when your site is less busy.
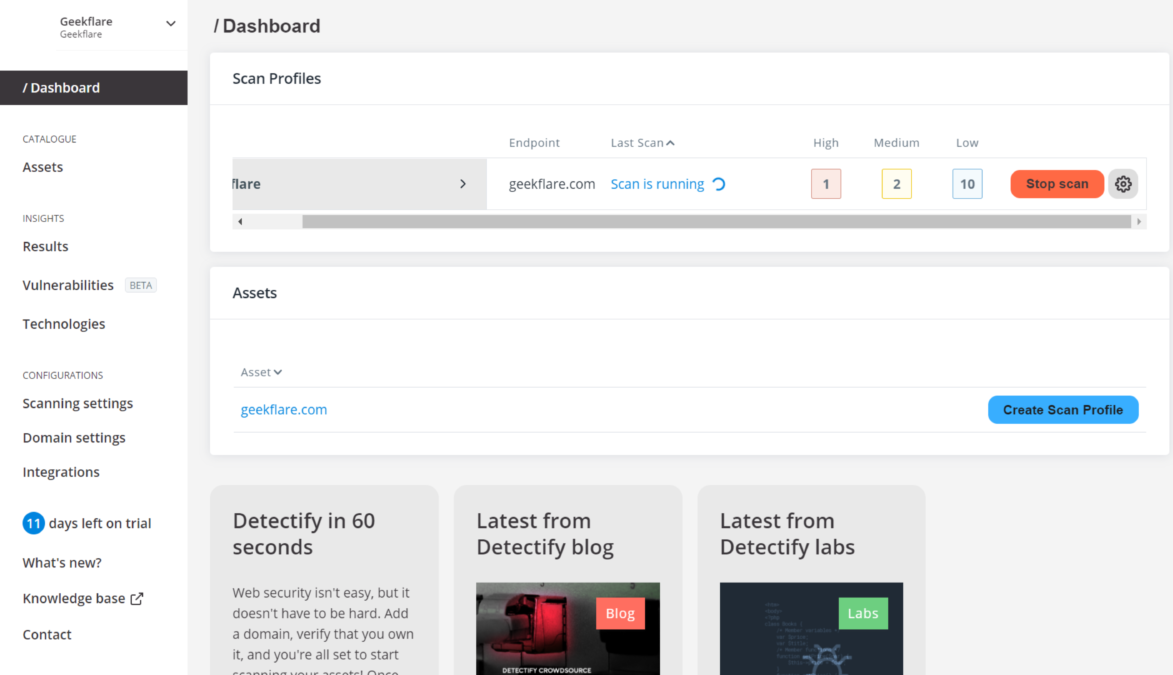
Scan reports
When Detectify finishes scanning your site, you will receive an e-mail telling you so. In that e-mail, it will inform you of the time it took to perform the scan, the number of issues found grouped by their severity, and an overall threat score that shows how good or bad the site is in terms of security.
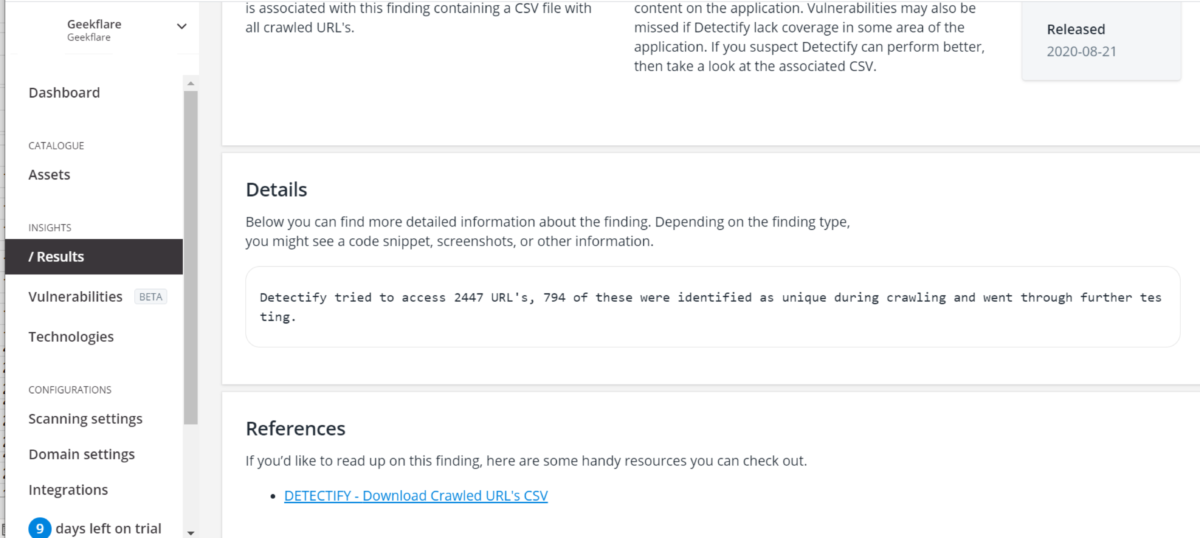
You can see what URLs were crawled during the scan by going to the latest scan report and clicking on the “Crawled URL’s” item in the information findings list. The Details section shows how many URLs the crawler tried to access during the scan and how many of those were identified as unique.
There’s a hyperlink at the bottom of the page to download a CSV file containing all the crawled URLs and the status code of each one. You can go through this list to ensure all the important parts of your site have been visited.
To plan for remediation and to get more accurate results in future scans, Detectify allows you to tag each finding as “Fixed”, “Accepted risk” or “False positive”. If you tag a finding as “Fixed”, the scanner will use that same tag in future reports, so you won’t need to deal with it again for remediation. An “Accepted risk” is something you don’t want to get reported on every scan, while “False positive” is a finding that may resemble a vulnerability, although it is not.
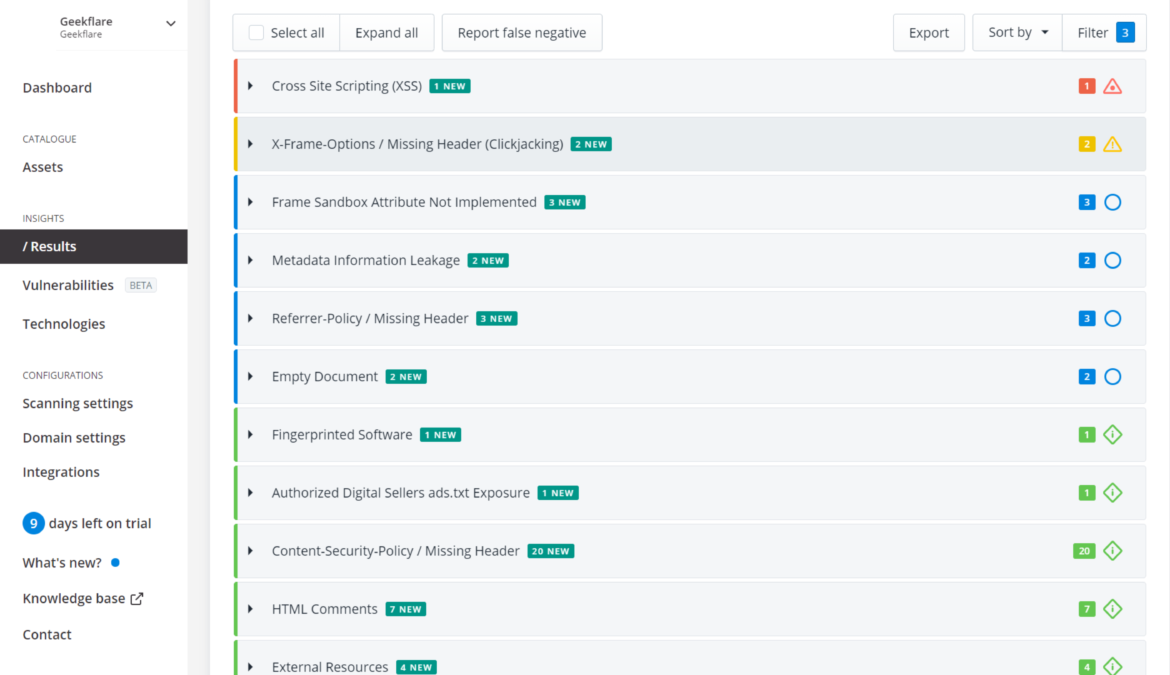
Ah! many findings to fix which I never thought.
Detectify offers many different pages and views to see the scan results. The “All tests” view allows you to see all the vulnerabilities the scan discovered. If you’re familiar with the OWASP classification, you can check out the OWASP view to see how vulnerable your site is to the top 10 vulnerabilities.
To fine-tune future scans, you can use Detectify’s white/blacklisting options to add your site areas that could be hidden because no links point to them. Or you can disallow paths that you don’t want the crawler to get in.
The asset inventory
Detectify’s asset inventory page shows a list of root assets – such as added domains or IP addresses – with a lot of useful information that will help you secure your IT investments. Next to each asset, a blue or grey icon indicates if Asset Monitoring is turned on or off for it.
You can click on any of the assets in the inventory to get an overview of it. From there, you can examine sub-domain, scan profiles, fingerprinted technologies, asset monitoring findings, asset settings, and much more.
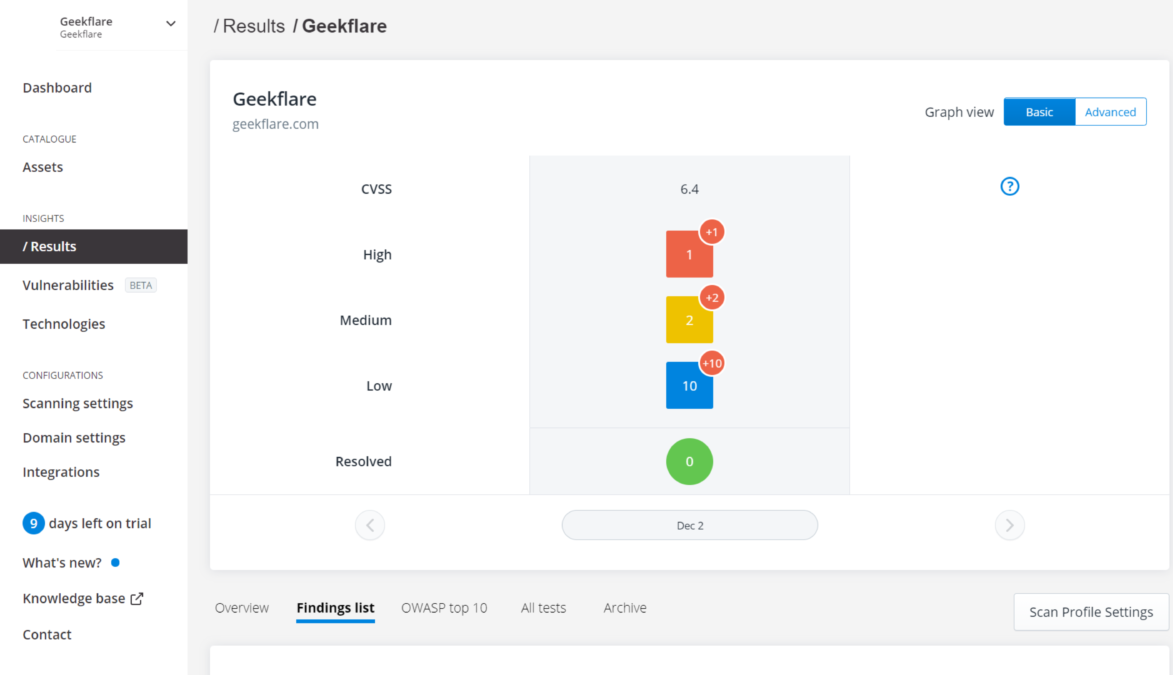
Asset Monitoring findings
It groups finding results into three categories according to their severity: high, medium, and low.
High-level findings mostly reflect issues where sensitive information (e.g., customer credentials or passwords) is being exposed to the public or is potentially exploitable.
Medium-level findings show situations in which it exposes some information. Even though that exposure may not be harmful by itself, a hacker could take advantage of it by combining it with other information.
Finally, low-level findings show sub-domains that could potentially be taken over and should be checked to verify their ownership.
Detectify provides a knowledge base with plenty of fixes and remediation tips to help you deal with the findings encountered during the scan. Once you take action to remediate the issues, you can run a second scan to check if the issues have been effectively remediated. Exporting options let you create PDF, XML, or JSON files with findings reports to send them to third parties or services such as Trello or JIRA.
Getting the most out of Detectify
Detectify’s best-practices guide recommends adding a domain name without subdomains to get an overview of your entire site if it is not too big. But there’s a time limit of 9 hours for an entire scan, after which the scanner jumps to the next phase of the process. For that reason, it could be a good idea to break your domain down into smaller scan profiles.
Your first scan may show you that some assets have more vulnerabilities than others. That’s another reason – besides the scanning duration – to start breaking your domain down. You should identify the most critical subdomains and create a scan profile for each one of them.
Pay attention to the “Discovered Hosts” list, since it can show you some unexpected findings. For example, systems that you didn’t know you had. This list is useful to identify the most crucial applications that deserve a more in-depth scan and, therefore, an individual scan profile.
Detectify suggests it’s better to define smaller scopes for each scan profile because it can get more accurate and consistent findings. It is also a good idea to break down scopes by keeping together similar technologies or frameworks within each profile. This way, the scanner will be able to run more relevant tests for each scan profile.
Conclusion
Asset inventory and monitoring are crucial for any size and website, including eCommerce, SaaS, retail, financial, and marketplace. Don’t keep any asset unattended; try the trial for 2 weeks to see how it can help you find loopholes to improve web application security.



