Geekflare is supported by our audience. We may earn affiliate commissions from buying links on this site.
Stay tuned while we tell you about some of the infamous cyber extortion attempts and the possible ways to stop them upfront.
A bank robbery is very unsafe for a sophisticated bad actor. It physically jeopardizes the criminal while it happens and awards hefty punishments if caught.
In contrast, you remain mostly untouched if you orchestrate a futuristic ransomware attack.
Conclusively, cyber extortions are far less risky and more profitable in comparison to conventional thefts or robberies. In addition, the weaker penalties have further favored cybercriminals.
Factor in the untraceable cryptocurrencies, and we should already start strengthening our defenses.
What is Cyber Extortion?
Cyber Extortion is an online attack to extract hefty ransom amounts. This is usually done by threatening server failures with a DDoS attack or encrypting your data, denying access.
Cyber extortion is an act of blackmail in these forms:
Data Hostage
A bad actor stops you from accessing your network of computers and asks for a ransom to restore access. This typically happens when you accidentally click a malicious link that downloads malware, encrypts the files, and locks you out.
Alternatively, someone hijacks your system, copies sensitive data, and frightens you to pay or risk exposing that to the general public. This sometimes involves social engineering in which they just play psychological tricks making you falsely believe the hack when there is none.
DDoS
Sometimes used to cover up a data theft, Distributed Denial of Service (DDoS) is when your network is flooded with fake service requests preventing your actual users from getting in.
This is carried out with a network of infected servers (botnets) or by memcaching, causing server slowdowns or failure. Depending on the scale of your online business, losses can be huge.
One can easily fund a DDoS attack for as little as $4 per hour while causing hundreds of thousands in loss to the victim. Besides the immediate loss, downtime pushes your customers to the competitors causing additional damages over time.
Major Cyber Extortion Attacks
Let’s take a look at some of the biggest such events recorded in the past.
#1. WannaCry
Starting on 12th May 2017, WannaCry was a global ransomware attack on computers running Microsoft Windows. Its actual scale is yet unknown because it still persists in some forms.
On the first day in office, WannaCry infected 230K computers in 150 countries. This affected big corporates and governments around the world. It could copy, install, execute, and spread itself within the network without any human interaction.
With WannaCry, Hackers took advantage of a Windows vulnerability using the exploit EternalBlue. Interestingly, EternalBlue was developed by the United States NSA to exploit a Windows vulnerability. The exploit code somehow got stolen and published by a hacker group named The Shadow Brokers.
Microsoft, knowing about the problem, issued an update to patch it. But the majority of users who were running outdated systems became the prime target.
The savior this time was Marcus Hutchins, who accidentally sinkholed the malware by registering a domain mentioned in the exploit code. That worked as a kill switch and kept WannaCry at bay. But there is a lot more to it, including the kill switch suffering a DDoS attack, Hutchins handling over the kill switch to Cloudflare that you can grab at TechCrunch.
Global estimated losses are around $4 billion.
#2. CNA Financial
On March 21, 2021, Chicago-based CNA Financial came to know that someone copied sensitive personal data of their employees, contract workers, and their dependents. This came to light after more than two weeks, as the hack was going undetected from March 5, 2021.
This was a hybrid attack that included data theft as well as keeping the CNA system hostage. The hackers, a Russia-based hacking group Evil Corp, used malware to encrypt CNA servers. After negotiations on the initial ransom amount of $60 million, the hackers finally settled for $40 million, as per Bloomberg.
#3. Colonial Pipeline
Colonial Pipeline hack caused disruptions in fuel supply from one of the biggest pipelines in the USA. The investigation revealed that it was the result of a single password leak on the dark web.
However, it was unknown how the bad actors got the correct username matching the compromised password. The hackers accessed Colonial systems using a Virtual Private Network meant for remote employees. Since there was no multi-factor authentication, a username and password were all but enough.
After a week of this activity, on May 7, 2021, one of the current employees saw a ransom note demanding $4.4 million in cryptocurrencies. Within hours, the officials shut the complete pipeline hired cyber security firms to verify and mitigate the damage. They also noticed a 100GB data theft, and the hacker threatened to expose it in the event of non-payment of the ransom amount.
The ransomware crippled the billing and accounting section of Colonial IT systems. The ransom amount was paid shortly after the attack to DarkSide, a hacking group based in eastern Europe. DarkSide provided a decryption tool that proved so slow that it took a week to normalize the pipeline operations.
Interestingly, the US Department of Justice released a public statement on June 7, 2021, citing the recovery of 63.7 bitcoins from the original payment. Somehow, the FBI got hold of the private keys related to the hacker accounts and brought back $2.3 million, apparently less than that was paid owing to the sudden slump in bitcoin prices in that period.
#4. Dyn
In addition to doing many things internet, Dyn primarily acts as a DNS service provider for some of the big names, including Twitter, Netflix, Amazon, Airbnb, Quora, CNN, Reddit, Slack, Spotify, PayPal, etc. These were brought down with a major DDoS attack on October 21, 2016.
The attacker used the Mirai botnet, which deployed a large number of compromised IoT devices to send false DNS requests. This traffic jammed the DNS servers causing extreme slowdowns piling an unknown amount of losses worldwide.
While the scale of the attack makes it difficult to calculate the exact amount of damage suffered by the websites, Dyn lost big.
Around 14,500 domains (roughly 8%) switched to a different DNS provider immediately after the attack.
While many more suffered similar attacks like the Amazon Web Services, GitHub, let’s avoid going off-road and move into drawing a rock-solid strategy to prevent such cyber extortion events.
How to Prevent Cyber Extortion?
Some of the very basic preventive measures that can help you shield against such internet attacks are:
#1. Avoid Clicking Malicious Links
Attackers often take advantage of this childish attribute of human psychology: curiosity.

Phishing Emails were the gateway of around 54% of ransomware attacks. So, in addition to reminding yourself and your employees about spam emails, organize workshops.
This can include dummy phishing emails with weekly campaigns to provide live training. It will work more like vaccinations in which a small amount of dead virus loads protect against live threats.
Additionally, you can train employees in sandboxing-like technologies to open suspicious links and applications.
#2. Software Updates and Security Solutions
Irrespective of your OS, outdated software is susceptible to cyber extortion attacks. People could easily have avoided WannaCay had they updated their Windows PCs in time.
One more common misconception is you’re safe if using a Mac. That’s completely untrue. And Malwarebytes state of malware report tears through any false sense of security among Mac users.
Windows OS has seen major attacks simply because Mac wasn’t that popular. Microsoft’s OS still has a market share of close to 74%, and targeting Mac users isn’t simply worth the trouble.
But since that’s slowly changing, Malwarebytes witnessed a 400% jump in threats aimed at Mac OS from 2018 to 2019. In addition, they noted 11 threats per Mac in comparison to 5.8 threats for a Windows device.
Conclusively, investing in a comprehensive internet security solution like Avast One can definitely prove its worth.
Additionally, you can deploy intruder detection systems like Snort or Suricata for a better safety net.
#3. Use Strong Passwords
The Colonial Pipeline attack was caused due to an employee using a weak password twice.
As per an Avast survey, about 83% of Americans use weak passwords, and as many as 53% use the same passwords on multiple accounts.
Admittedly, pushing users to use strong passwords for their own has already proved an uphill task. Asking them to do that at work seems nearly impossible.
So, what’s the solution? User authentication platforms.
You can make use of these platforms to enforce strong passwords requirements at your organization. These are 3rd-party specialists with flexible plans according to the company’s size. You can also start with always-free tiers with Ory, Supabase, Frontegg, etc.
At a personal level, use password managers.
Moreover, take the pain of updating passwords once in a while. This will ensure your safety even if your credentials get stolen somehow. And that’s a whole lot easier with premium password managers like Dashlane, which can auto-update your passwords with just a click.
But don’t just stop with a complicated password; try being creative with the username too.
#4. Offline Backups
The sophistication level of such attacks can sometimes trick even the big-name cybersecurity experts, let alone a small business owner.
Therefore, keep updated backups. This will help bring your system up on a fateful day.
And offline backups are an added advantage. They are your secure cold storage, unreachable by cyber extortionists.
Besides, take note of the available restore capabilities because prolonged downtimes can sometimes make the asked ransom look lucrative. And that’s precisely why some business owners negotiate with the threat actors and end up paying huge amounts.
Alternatively, 3rd-party backup and data recovery solutions like Acronis can come in handy. They provide ransomware protection and hassle-free data recovery mechanisms.
#5. Content Delivery Network (CDN)
Many have detected and averted big DDoS attacks thanks to competent content delivery networks.
As discussed above, it was, after all, an excellent CDN, Cloudflare, which maintained the WannaCry killswitch online non-stop for two years. It also helped it to withstand numerous DDoS attacks within that time frame.
A CDN maintains a cached copy of your website around the globe on multiple servers. They transfer excess loads to their network, avoiding server overloads and downtimes.
This strategy not only protects against DDoS threats but results in blazingly fast websites for worldwide customers.
Finally, there can’t be a complete list to protect you against cyber extortion. Things evolve, and it’s best to have a cybersecurity expert on board every time.
But what if it happens anyway? What should be your course of action if you get hit with an online extortion attempt.
Cyber Extortion Response
The first thing that comes to mind after a ransomware attack other than the usual anxiety is to pay and get done with it.
But that may not always work.
A survey conducted by SOPHOS, a UK-based IT security firm, shows that paying the ransom is not the best way out. The attack survey report mentions that only 8% of companies got the complete data back after paying the ransom. And 29% were able to restore only 50% or less of the stolen/encrypted data.
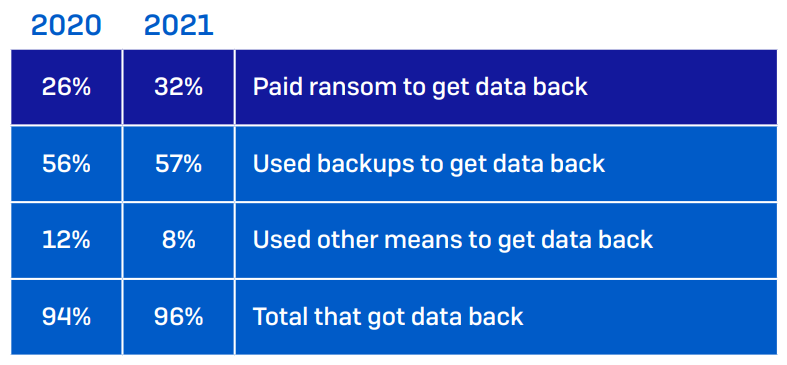
So, your act of compliance with ransom demands may backfire. It makes you dependent on the bad actor and his tools to decrypt your data delaying other rescue efforts.
Moreover, there is no guarantee that the tool given by the hacker will ever work. It may fail or further infect your system. In addition, paying the criminals highlights your organization as their paying customers. So, there is a very high chance of a similar attack in the future.
Conclusively, paying should be your last resort. Using other methods like restoring backups is safer than paying an unknown criminal with cryptocurrencies.
In addition, a few firms contacted leading cybersecurity experts and informed the law enforcement authorities. And that’s what saved them, like in the case of Colonial Pipeline extortion recovery by the FBI.
Cyber Extortion: Conclusion
You should note that it’s not as uncommon as one may think. And the obviously best way is to bolster your shields and keep backups.
If it happens regardless, keep calm, start local rescue operations, and contact experts.
But try not to give in to the ransom demands because that might not work even if you pay your fortunes out.
PS: Going through our cybersecurity checklist for your business may prove beneficial.



