It’s hard to resist clicking on a free iPhone offer link. But be careful: your click can be easily hijacked, and the results can be disastrous.
Clickjacking is an attack method, also known as User Interface Redressing, because it is set up by disguising (or redressing) a link with an overlay that tricks the user into doing something different than he or she thinks.
Most users of social networks enjoy the convenience of staying logged to them at all times. Attackers could easily take advantage of this habit to force users to like or follow something without noticing. To do this, a cybercriminal could put a tempting button –for example, with an appealing text, such as “Free iPhone – limited time offer”– on its own webpage and overlay an invisible frame with the social network’s page in it, in such a way that a “Like” or “Share” button lays over the Free iPhone button.
This simple clickjacking trick can force Facebook users to like groups or fan pages without knowing.
The described scenario is fairly innocent, in the sense that the only consequence for the victim is to be added to a social network group. But with some extra effort, the same technique could be used to determine if a user is logged to its banking account and, instead of liking or sharing some social media item, he or she could be forced to click on a button that transfer funds to an attacker’s account, for example. The worst part is that the malicious action cannot be traced, because the user was legitimate logged to his or her bank account, and he or she voluntarily clicked on the transfer button.
Because most clickjacking techniques require social engineering, social networks become ideal attack vectors.
Let’s see how they are used.
Clickjacking on Twitter
About ten years ago, the Twitter social network suffered a massive attack that quickly spread a message, which led users to click on a link, taking advantage of their natural curiosity.
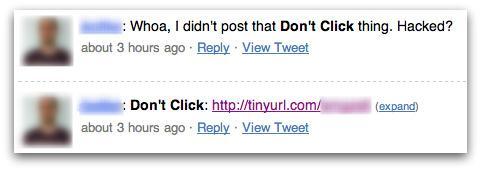
Tweets with the text “Don’t click,” followed by a link, propagated rapidly across thousands of Twitter accounts. When users clicked on the link and then on a seemingly innocent button on the target page, a tweet was sent from their accounts. That tweet included the text “Don’t click,” followed by the malicious link.
Twitter engineers patched the clickjacking attack not long after it started. The attack itself proved to be harmless, and it worked as an alarm telling the potential risks involved in Twitter clickjacking initiatives. The malicious link took the user to a web page with a hidden iframe. Inside the frame was an invisible button that sent the malicious tweet from the victim’s account.
Clickjacking on Facebook
Mobile Facebook app users are exposed to a bug that lets spammers post clickable content on their timelines, without their consent. The bug was discovered by a security professional who was analyzing a spam campaign. The expert observed that many of his contacts were publishing a link to a page with funny pictures. Before reaching the pictures, users were asked to click on a declaration of coming of age.
What they didn’t know was that the declaration was under an invisible frame.
When users accepted the declaration, they were taken to a page with funny pictures. But in the meantime, the link was published in the users’ Facebook timeline. That was possible because the web browser component in the Facebook app for Android isn’t compatible with the frame options headers (below we explain what they are), and therefore allows for malicious frame overlaying.
Facebook doesn’t recognize the issue as a bug because it has no impact on users’ accounts integrity. So it’s uncertain if it is ever going to be fixed.
Clickjacking on lesser social networks
It is not just Twitter and Facebook. Other less popular social networks and blogging platforms also have vulnerabilities that allow for clickjacking. LinkedIn, for example, had a flaw that opened a door for attackers to trick users into sharing and posting links on their behalf but without their consent. Before it got fixed, the flaw allowed attackers to load the LinkedIn ShareArticle page on a hidden frame, and overlay this frame on pages with seemingly innocent and appealing links or buttons.
Another case is Tumblr, the public web blogging platform. This site uses JavaScript code to prevent clickjacking. But this protection method becomes ineffective since the pages can be isolated in an HTML5 frame that prevents them from running JavaScript code. A carefully crafted technique could be used to steal passwords, combining the mentioned flaw with a password helper browser plugin: by tricking users to type in a false captcha text, they can be inadvertently sending their passwords to the attacker’s site.
Cross-site request forgery
One variant of clickjacking attack is called Cross-site request forgery, or CSRF for short. With the help of social engineering, cybercriminals direct CSRF attacks against end-users, forcing them to execute unwanted actions. The attack vector can be a link sent via email or chat.
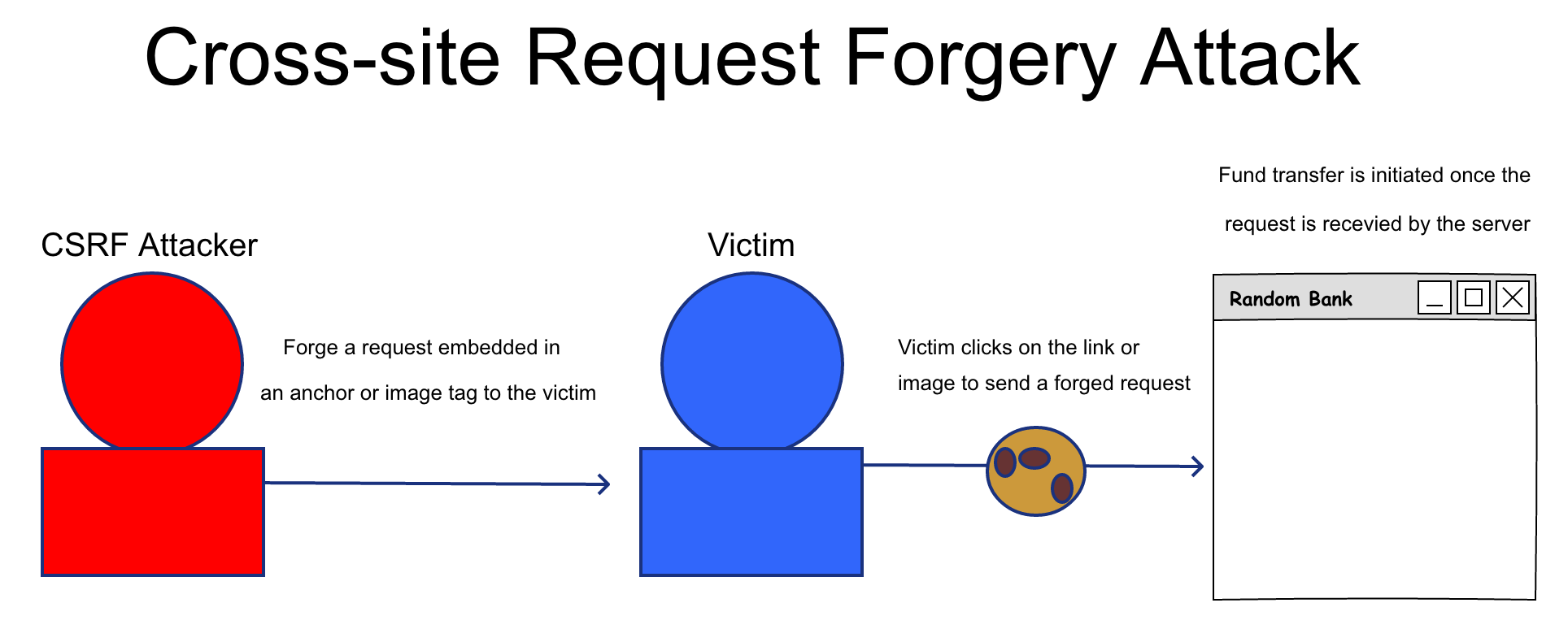
CSRF attacks do not intend to steal the user’s data because the attacker can’t see the response to the phony request. Instead, the attacks target state-changing requests, like a password change or a funds transfer. If the victim has administrative privileges, the attack has the potential to compromise an entire web application.
A CSRF attack can be stored on vulnerable websites, particularly websites with so-called “stored CSRF flaws.” This can be accomplished by entering IMG or IFRAME tags in input fields that are later shown on a page, such as comments or a search results page.
Preventing framing attacks
Modern browsers can be told if a particular resource is allowed or not to load within a frame. They also can opt to load a resource in a frame only when the request originates from the same site the user is at. This way, users cannot be tricked to click on invisible frames with content from other sites, and their clicks don’t get hijacked.
Client-side mitigation techniques are called frame busting or frame killing. Although they can be effective in some cases, they can also be easily bypassed. That is why client-side methods are not considered as best practices. Instead of frame busting, security experts recommend server-side methods such as X-Frame-Options (XFO) or more recent ones, like Content Security Policy.
X-Frame-Options is a response header that web servers include on web pages to indicate whether or not a browser is allowed to show its contents inside a frame.
The X-Frame-Option header allows three values.
- DENY, which forbids to display the page within a frame
- SAMEORIGIN, which allows displaying the page within a frame, as long as it stays in the same domain
- ALLOW-FROM URI, which allows the display of the page within a frame but only in a specified URI (Uniform Resource Identifier), e.g., only within a particular, specific webpage.
More recent anti-clickjacking methods include Content Security Policy (CSP) with the frame-ancestors directive. This option is being widely used in the replacement of XFO. One major benefit of CSP in comparison to XFO is that it allows a web server to authorize multiple domains to frame its content. However, it is not yet supported by all browsers.
CSP’s frame-ancestors directive admits three types of values: ‘none,’ to prevent any domain from showing the content; ‘self,’ to only allow the current site to show the content in a frame, or a list of URLs with wildcards, such as ‘*.some site.com,’ ‘https://www.example.com/index.html,’ etc., to only allow framing on any page that matches an element from the list.
How to protect yourself against clickjacking
It is convenient to stay logged to a social network while browsing around, but if you do so, you need to be cautious with your clicks. You should also pay attention to the sites you visit because not all of them take the necessary measures to prevent clickjacking. In case you are not sure about a website you are visiting, you should not click on any suspicious click, no matter how tempting it could be.
Another thing to pay attention to is your browser version. Even if a site uses all the clickjacking prevention headers we mentioned before, not all browsers support all of them, so be sure to use the latest version you can get and that it supports anti-clickjacking features.
Common sense is an effective self-protection device against clickjacking. When you see unusual content, including a link posted by a friend on any social network, before doing anything, you should ask yourself if that is the type of content your friend would publish. If not, you should warn your friend that he or she could have become a victim of clickjacking.
One last piece of advice: if you are an influencer, or you just have a really big number of followers or friends on any social network, you should double your precautions and practice a responsible behavior online. Because if you become a clickjacking victim, the attack will end up affecting a whole lot of people.



